48
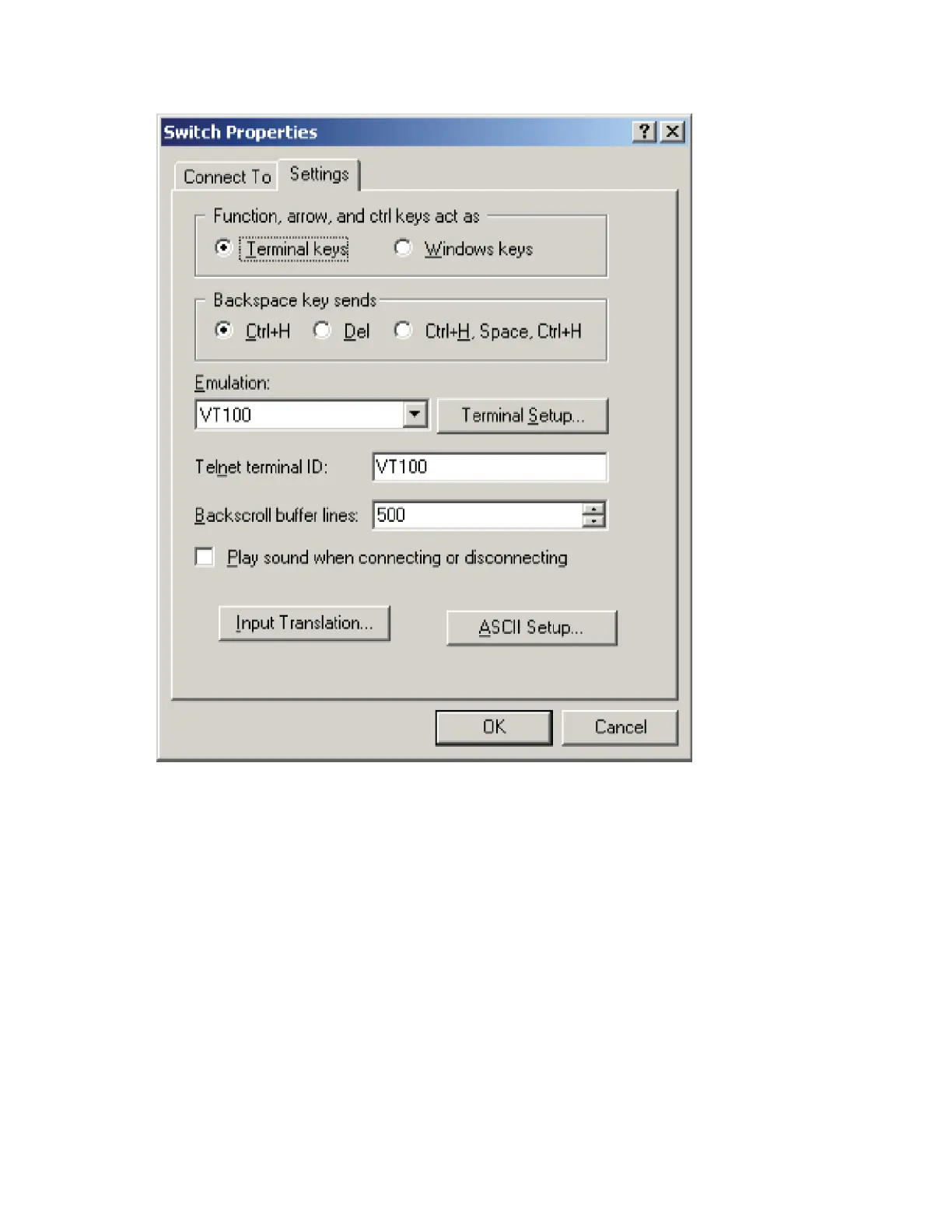
Figure 62 Setting terminal emulation in Switch Properties dialog box
Powering on the switch
Verification before power-on
Before powering on the switch, verify that:
The power cord is properly connected.
The input power voltage meets the requirement of the switch.
The console cable is properly connected, the terminal or PC used for configuration has started, and
the configuration parameters have been set.
 Loading...
Loading...











