Preventing Data Leaks Due to Unauthorized Transmission
17
2
Preventing Data Leaks Due to
Unauthorized Transmission
If user authentication is specified, the user who has logged on can be designated
as the sender to prevent unauthorized access.
You can also limit the direct entry of destinations to prevent files from being sent
to destinations not registered in the address book.
Specifying Which Users Are Allowed to Send Files
If user authentication is specified, the user who has logged on is designated as
the sender. With this setting, you can prevent unauthorized access. If you have
not specified user authentication, see General Settings Guide.
Note
❒ You need to register the e-mail address. See General Settings Guide.
Restrictions on Destinations
This can be specified by the user administrator.
Make the setting to disable the direct entry of e-mail addresses under the scan-
ner function.
By making this setting, the destinations can be restricted to addresses registered
in the address book.
Preparation
For details about logging on with administrator authentication, see p.75
“Logging on Using Administrator Authentication”.
For details about logging off with administrator authentication, see p.76
“Logging off Using Administrator Authentication”.
A
AA
A
Press the {
{{
{User Tools/Counter}
}}
} key.
B
BB
B
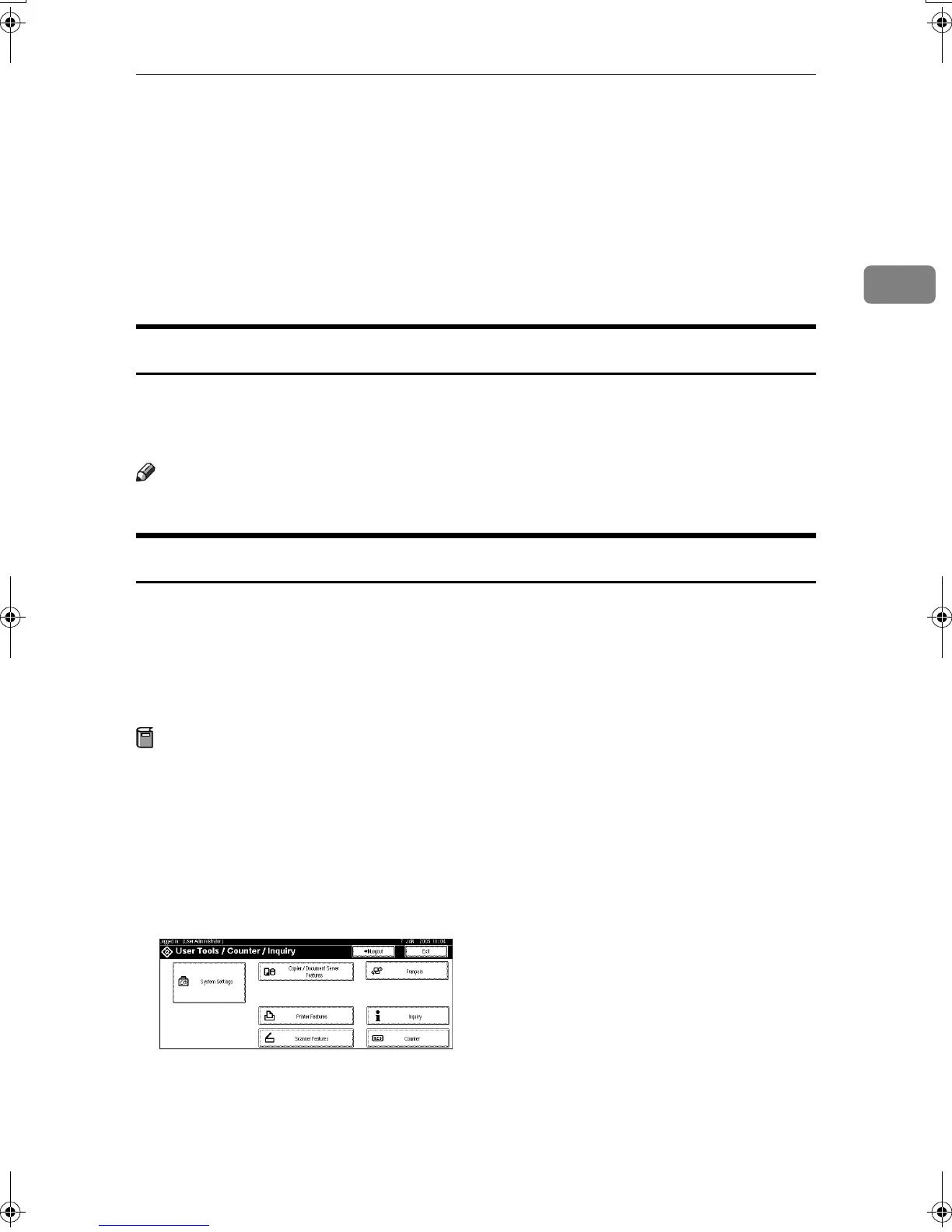
Press [System Settings].
MarC25_EN_SecRef_F_FM.book Page 17 Monday, August 2, 2004 6:14 PM

 Loading...
Loading...