21-5
Catalyst 3550 Multilayer Switch Software Configuration Guide
78-11194-09
Chapter 21 Configuring Port-Based Traffic Control
Configuring Protected Ports
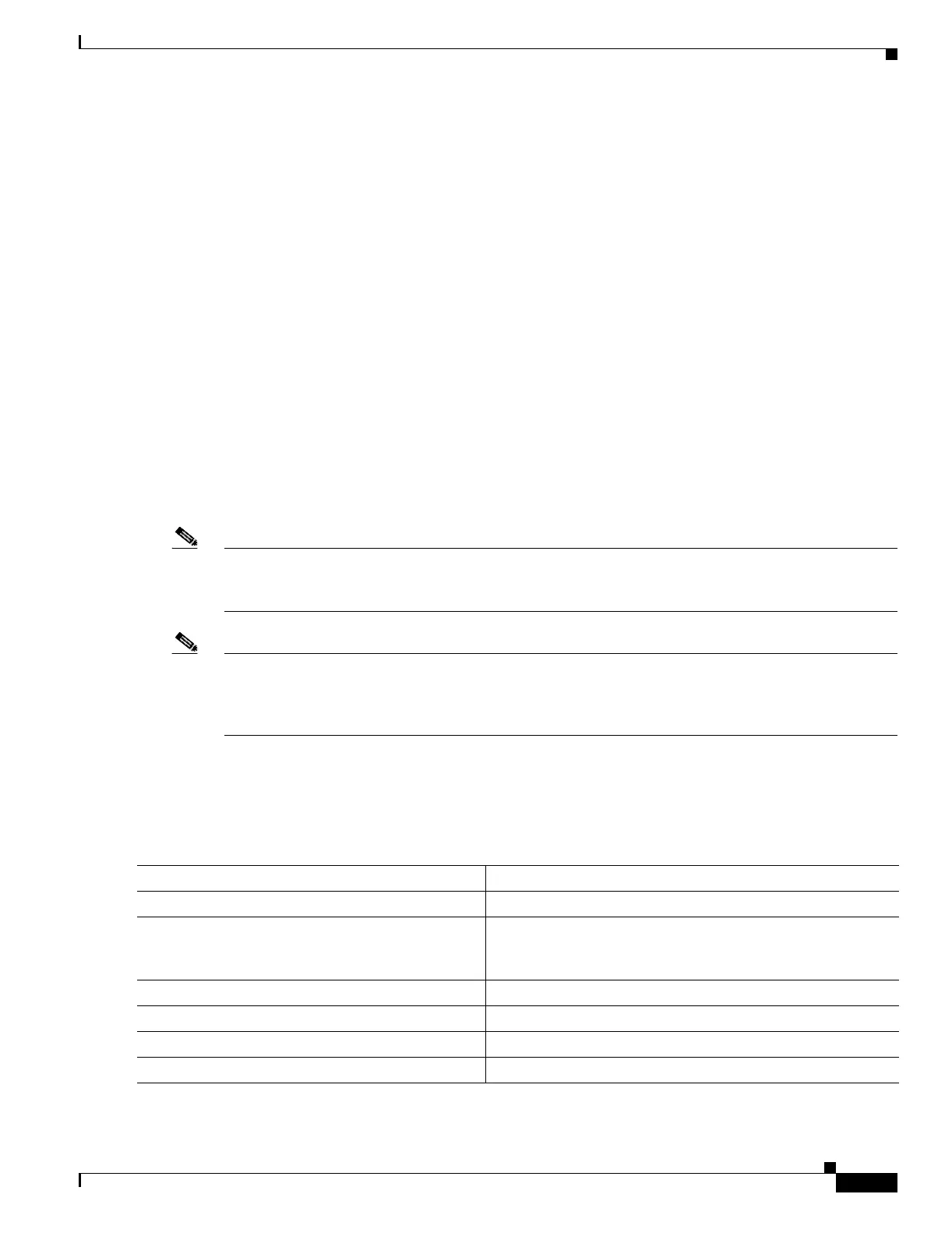
Switch# show storm-control fastethernet0/17 multicast
Interface Filter State Level Current
--------- ------------- ------- -------
Fa0/17 inactive 100.00% N/A
Configuring Protected Ports
Some applications require that no traffic be forwarded between ports on the same switch so that one
neighbor does not see the traffic generated by another neighbor. In such an environment, the use of
protected ports ensures that there is no exchange of unicast, broadcast, or multicast traffic between these
ports on the switch.
Protected ports have these features:
• A protected port does not forward any traffic (unicast, multicast, or broadcast) to any other port that
is also a protected port. Traffic cannot be forwarded between protected ports at Layer 2; all traffic
passing between protected ports must be forwarded through a Layer 3 device.
• Forwarding behavior between a protected port and a nonprotected port proceeds as usual.
• Protected ports are supported on 802.1Q trunks.
The default is to have no protected ports defined.
Note The protected port feature is not compatible with fallback bridging. When fallback bridging is enabled,
it is possible for packets to be forwarded from one protected port on a switch to another protected port
on the same switch if the ports are in different VLANs.
Note There could be times when unknown unicast or multicast traffic from a nonprotected port is flooded to
a protected port because a MAC address has timed out or has not been learned by the switch. Use the
switchport block unicast and switchport block multicast interface configuration commands to
guarantee that no unicast or multicast traffic is flooded to the port in such a case.
You can configure protected ports on a physical interface (for example, Gigabit Ethernet 0/1) or an
EtherChannel group (for example, port-channel 5). When you enable protected ports for a port channel,
it is enabled for all ports in the port-channel group.
Beginning in privileged EXEC mode, follow these steps to define a port as a protected port:
Command Purpose
Step 1
configure terminal Enter global configuration mode.
Step 2
interface interface-id Specify the type and number of the physical interface to
configure, for example gigabitethernet0/1, and enter
interface configuration mode.
Step 3
switchport protected Configure the interface to be a protected port.
Step 4
end Return to privileged EXEC mode.
Step 5
show interfaces interface-id switchport Verify your entries.
Step 6
copy running-config startup-config (Optional) Save your entries in the configuration file.

 Loading...
Loading...











