267
NOTE:
• A manual IPsec policy can reference only one IPsec proposal. To change an IPsec proposal for an IPsec
policy, you must remove the proposal reference first.
• If you configure a key in two modes: string and hexadecimal, only the last configured one will be used.
Displaying and maintaining IPsec
To do… Use the command… Remarks
Display IPsec policy information
display ipsec policy [ brief | name policy-name
[ seq-number ] ] [ | { begin | exclude | include }
regular-expression ]
Available in any view
Display IPsec proposal
information
display ipsec proposal [ proposal-name ] [ |
{ begin | exclude | include }
regular-expression ]
Available in any view
Display IPsec SA information
display ipsec sa [ brief | policy policy-name
[ seq-number ] ] [ | { begin | exclude | include }
regular-expression ]
Available in any view
Display IPsec packet statistics
display ipsec statistics [ | { begin | exclude |
include } regular-expression ]
Available in any view
Clear SAs
reset ipsec sa [ policy policy-name
[ seq-number ] ]
Available in user view
Clear IPsec statistics reset ipsec statistics Available in user view
IPsec for RIPng configuration example
NOTE:
The IPsec configuration procedures for protecting OSPFv3 and IPv6 BGP are similar. For more information
about RIPng, OSPFv3, and IPv6 BGP, see
Layer 3
—
IP Routing Configuration Guide
. Only the 3600 v2 EI
switches support IPsec for OSPFv3 and IPv6 BGP.
Network requirements
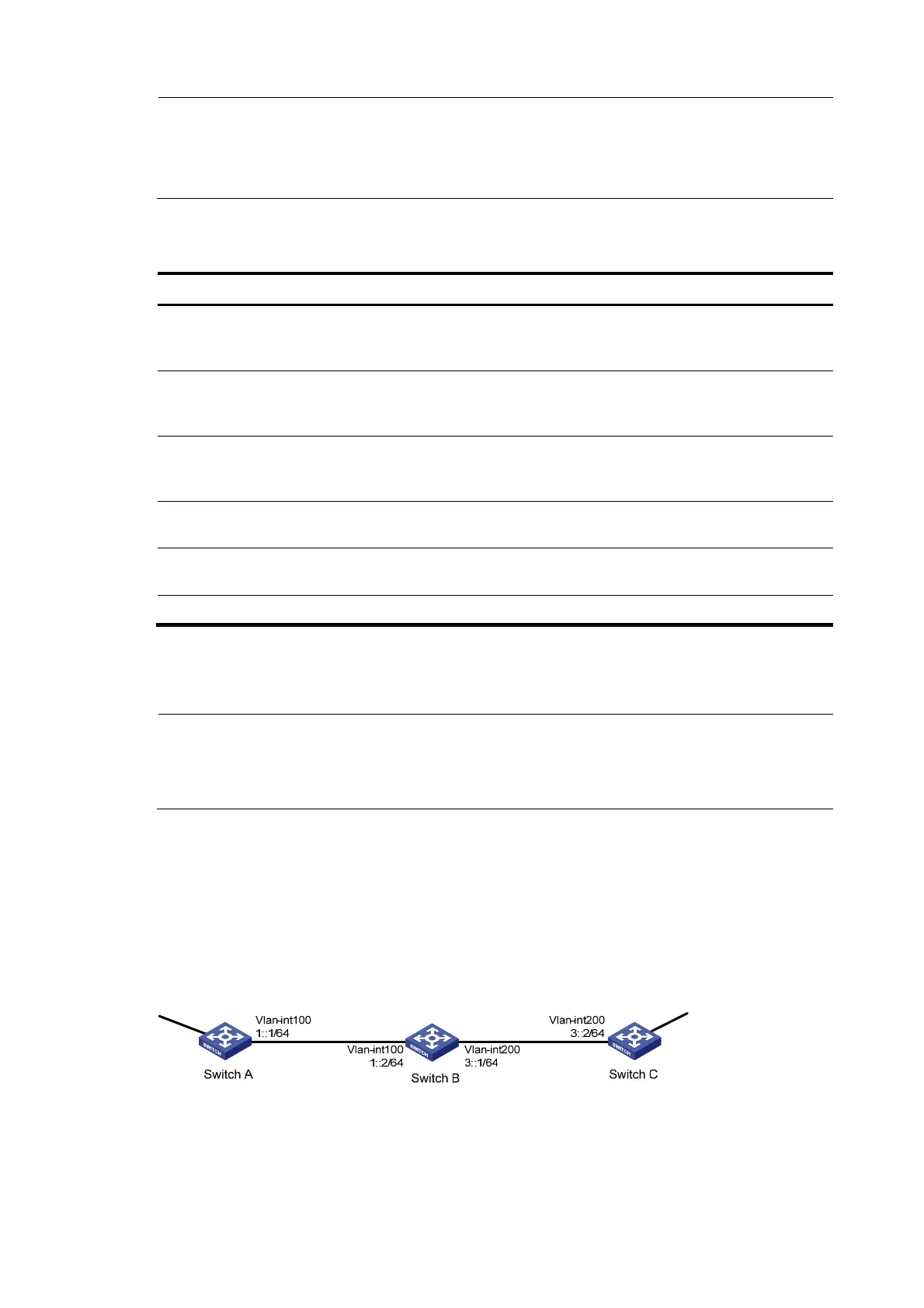
As shown in Figure 100, Switch A, Switch B, and Switch C are connected. They learn IPv6 routing
information through RIPng.
Configure IPsec for RIPng so that RIPng packets exchanged between the switches are transmitted through
an IPsec tunnel. Configure IPsec to use the security protocol ESP, the encryption algorithm DES, and the
authentication algorithm SHA1-HMAC-96.
Figure 100 Network diagram
 Loading...
Loading...















