381
Blacklist configuration example
Network requirements
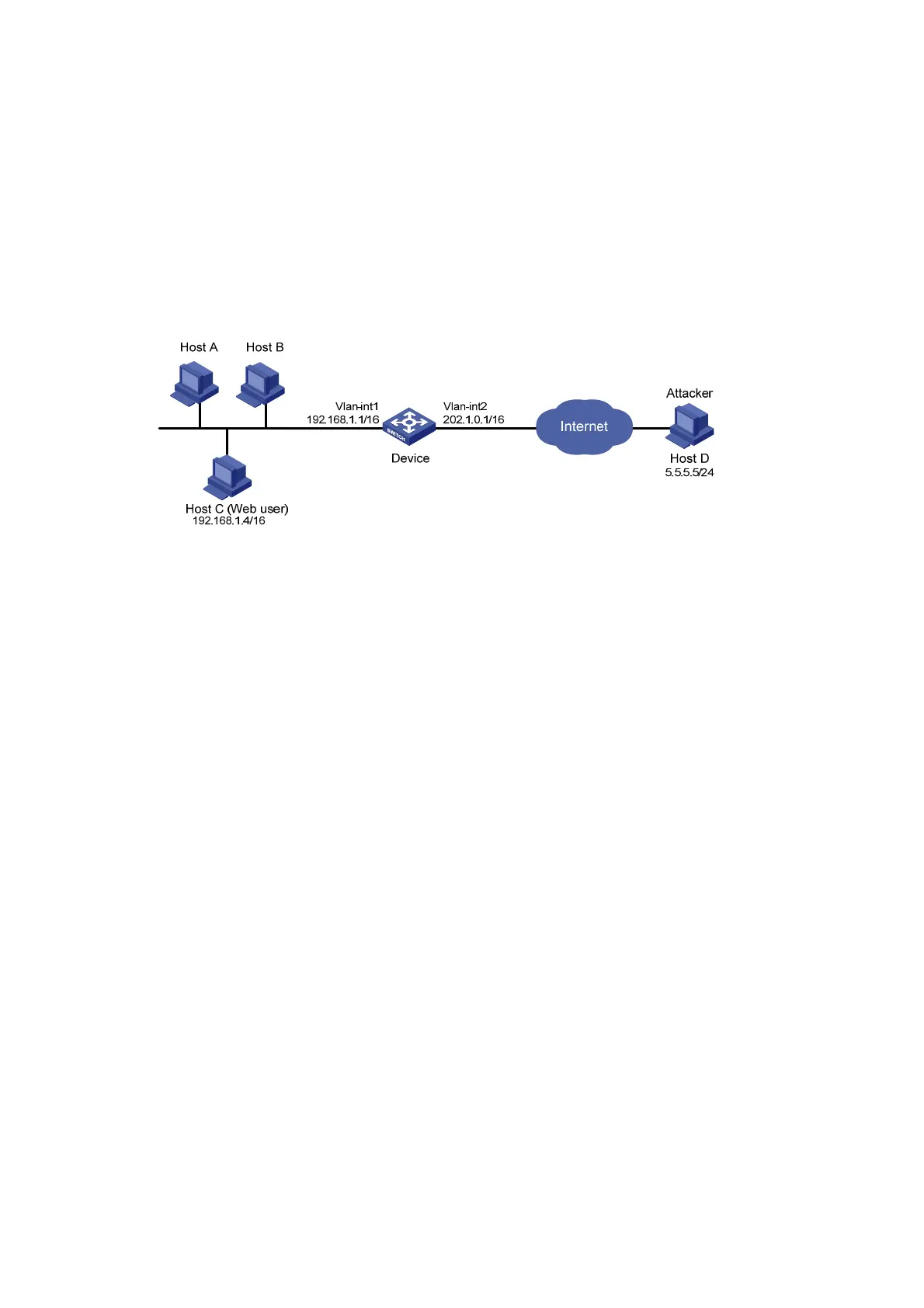
As shown in Figure 147, Host A, Host B, and Host C are internal users, and external user Host D is
considered an attacker.
Configure Device to always filter packets from Host D, and to prevent internal users from guessing
passwords.
Figure 147 Network diagram
Configuration procedure
# Assign IP addresses to the interfaces of Device. (Details not shown)
# Enable the blacklist feature.
<Device> system-view
[Device] blacklist enable
# Add the IP address of Host D 5.5.5.5 to the blacklist. Do not specify any aging time to make the entry
never age out.
[Device] blacklist ip 5.5.5.5
Verifying the configuration
If Host C tries to log in to Device through web for six times but fails to log in, the device blacklists Host
C. Use the display blacklist all command to view all added blacklist entries.
[Device] display blacklist all
Blacklist information
------------------------------------------------------------------------------
Blacklist : enabled
Blacklist items : 2
------------------------------------------------------------------------------
IP Type Aging started Aging finished Dropped packets
YYYY/MM/DD hh:mm:ss YYYY/MM/DD hh:mm:ss
5.5.5.5 manual 2011/04/09 16:02:20 Never 0
192.168.1.4 manual 2011/04/09 16:02:26 2011/04/09 16:12:26 0
Host D and Host C are on the blacklist. Host C will stay on the list for 10 minutes, and will then be able
to try to log in again. The entry for Host D will never age out. When you do not consider Host D an
attacker anymore, you can use the undo blacklist ip 5.5.5.5 command to remove the entry.
 Loading...
Loading...















