InteliLite Global Guide
120
6.1.2 Remote communication
A PC can be connected to the controller also remotely via CM-GPRS or CM-Ethernet plug-in module.
IMPORTANT: Factory default password and access code are "0". It is highly recommended to
change these parameters.
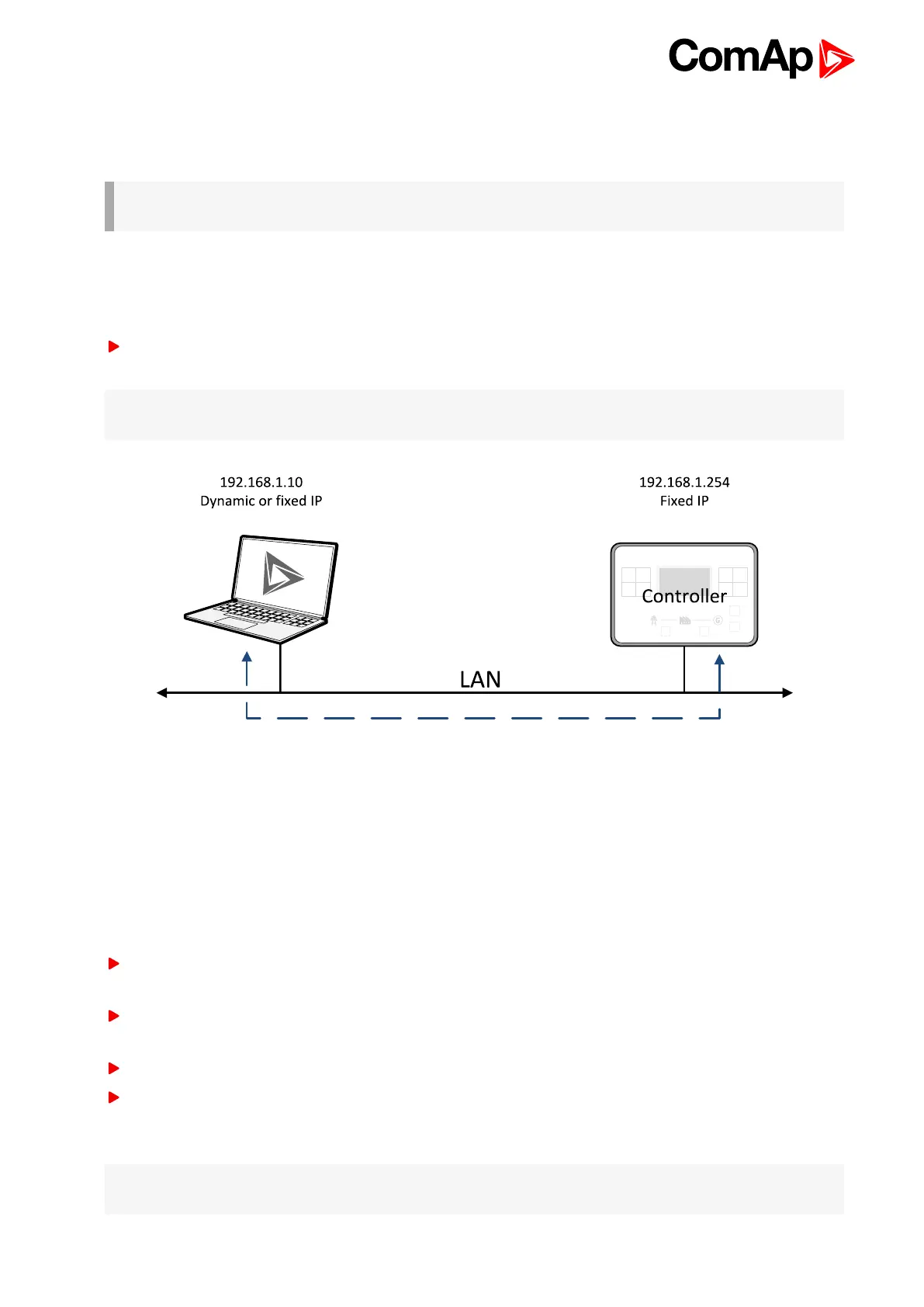
Ethernet LAN connection
Direct IP LAN connection is intended to be used if the CM-Ethernet module is reachable from the client
computer by specifying the IP address at which the module can be contacted.
If direct IP connection is to be used within a local network the CM-Ethernet must have static IP address in
the respective local network.
Note: If you have troubles with setting up static and public IP address for direct connection from Internet use
AirGate connection instead.
Image 6.6 Ethernet LAN connection
Setting-up static IP address
There are two basic ways to get the static IP address.
First way is to switch theCM-Ethernet to manual IP address mode. Adjust the setpoint IP Address Mode (page
332) to FIXED. In that case all setpoints of IP settings(IP Address (page 332), Subnet Mask (page 333), Gateway
IP (page 333), DNS IP Address 1 (page 334)) have to be adjusted manually. If this method is used several basic
rules should be kept to avoid conflicts with the remaining network infrastructure:
The static IP used in the controller must be selected in accordance with the local network in which CM-
Ethernet is connected.
The static IP used in the controller must be excluded from the pool of addresses which is assigned by
DHCP server, which is in charge of the respective local network.
The local infrastructure must generally allow using devices with manually assigned IP addresses.
There must not be any other device using the same static IP address. This can be tested from a computer
connected to the same network using "ping <required_ip_address>" command issued from the command
line. The IP address is not occupied if there is not any response to the ping command.
Note: The list above contains only basic rules. Other specific restrictions/rules may take place depending on
the local network security policy, technology used, topology etc.

 Loading...
Loading...











