1-6
Cisco ASA Series CLI Configuration Guide
Chapter 1 Starting Interface Configuration (ASA 5510 and Higher)
Information About Starting ASA 5510 and Higher Interface Configuration
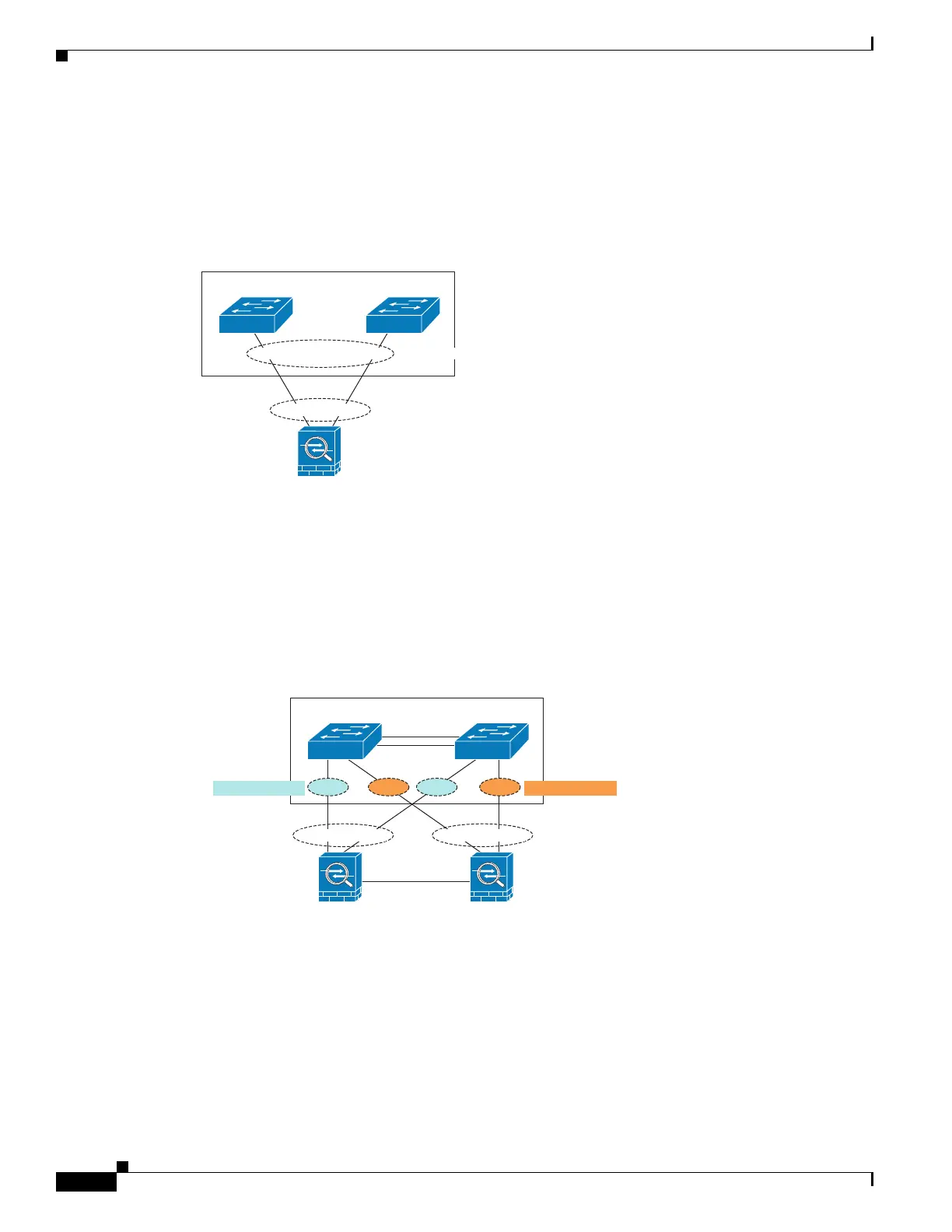
When the switch is part of a Virtual Switching System (VSS), then you can connect ASA interfaces
within the same EtherChannel to separate switches in the VSS. The switch interfaces are members of the
same EtherChannel port-channel interface, because the separate switches act like a single switch (see
Figure 1-1).
Figure 1-1 Connecting to a VSS
If you use the ASA in an Active/Standby failover deployment, then you need to create separate
EtherChannels on the switches in the VSS, one for each ASA (see Figure 1-1). On each ASA, a single
EtherChannel connects to both switches. Even if you could group all switch interfaces into a single
EtherChannel connecting to both ASAs (in this case, the EtherChannel will not be established because
of the separate ASA system IDs), a single EtherChannel would not be desirable because you do not want
traffic sent to the standby ASA.
Figure 1-2 Active/Standby Failover and VSS
Link Aggregation Control Protocol
The Link Aggregation Control Protocol (LACP) aggregates interfaces by exchanging the Link
Aggregation Control Protocol Data Units (LACPDUs) between two network devices.
Firewall
Switch 1
port-channel 1
VSS
Switch 2
port-channel 2
gig0/0
gig3/5 gig6/5
gig0/1
Primary Firewall
Switch 1
port-channel 1port-channel 1
VSS
Switch 2
Secondary Firewall
port-channel 3port-channel 2
gig0/0 gig0/1 gig0/0 gig0/1
gig3/2 gig3/3 gig6/3gig6/2

 Loading...
Loading...











