1-25
Cisco ASA Series CLI Configuration Guide
Chapter 1 Configuring Twice NAT
Configuration Examples for Twice NAT
• Different Translation Depending on the Destination Address and Port (Dynamic PAT), page 1-26
Different Translation Depending on the Destination (Dynamic PAT)
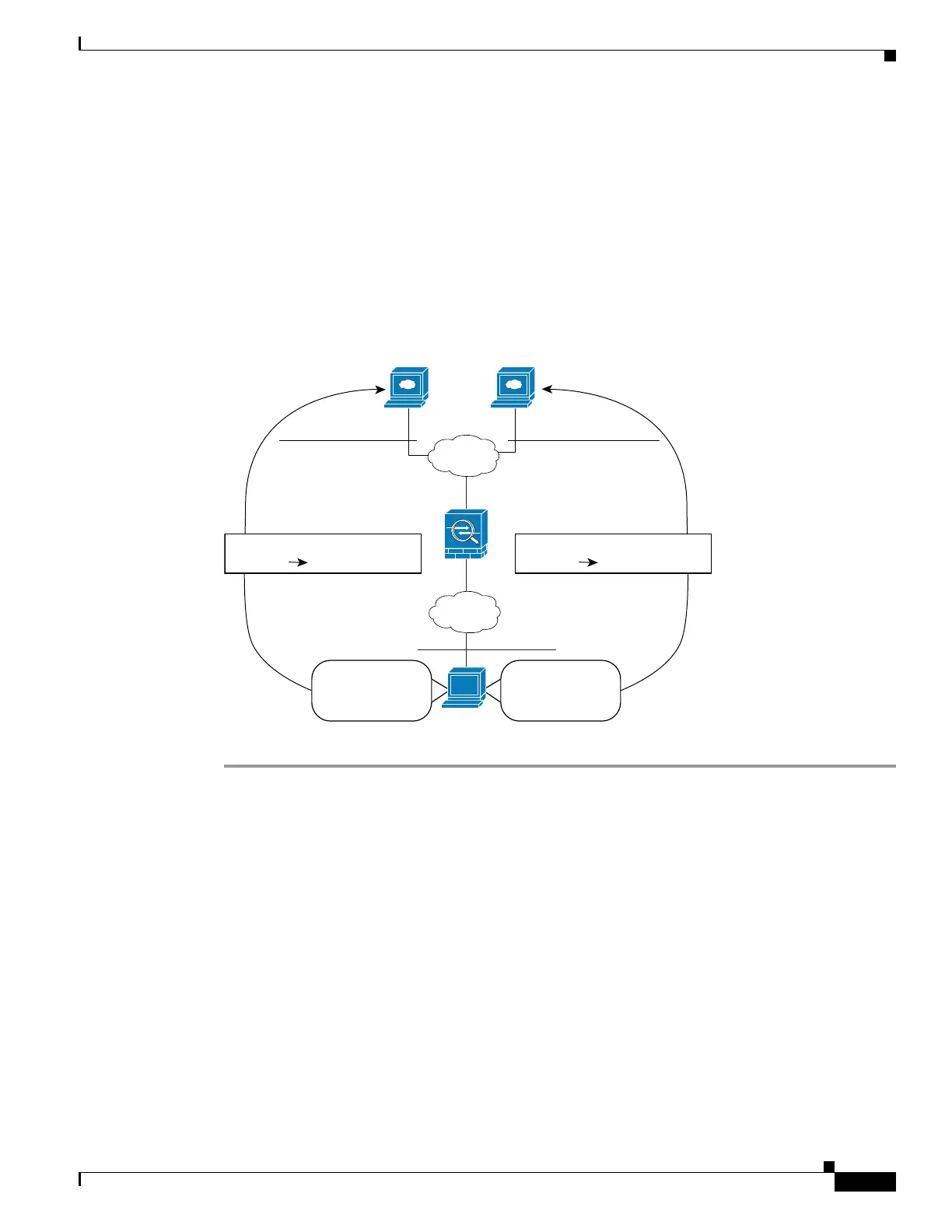
Figure 1-1 shows a host on the 10.1.2.0/24 network accessing two different servers. When the host
accesses the server at 209.165.201.11, the real address is translated to 209.165.202.129:port. When the
host accesses the server at 209.165.200.225, the real address is translated to 209.165.202.130:port.
Figure 1-1 Twice NAT with Different Destination Addresses
Step 1 Add a network object for the inside network:
hostname(config)# object network myInsideNetwork
hostname(config-network-object)# subnet 10.1.2.0 255.255.255.0
Step 2 Add a network object for the DMZ network 1:
hostname(config)# object network DMZnetwork1
hostname(config-network-object)# subnet 209.165.201.0 255.255.255.224
Step 3 Add a network object for the PAT address:
hostname(config)# object network PATaddress1
hostname(config-network-object)# host 209.165.202.129
Step 4 Configure the first twice NAT rule:
hostname(config)# nat (inside,dmz) source dynamic myInsideNetwork PATaddress1 destination
static DMZnetwork1 DMZnetwork1
Because you do not want to translate the destination address, you need to configure identity NAT for it
by specifying the same address for the real and mapped destination addresses.
Server 1
209.165.201.11
Server 2
209.165.200.225
DMZ
Inside
10.1.2.27
10.1.2.0/24
130039
209.165.201.0/27 209.165.200.224/27
Translation
209.165.202.12910.1.2.27
Translation
209.165.202.13010.1.2.27
Packet
Dest. Address:
209.165.201.11
Packet
Dest. Address:
209.165.200.225

 Loading...
Loading...











