8.1 Security Settings
8-9
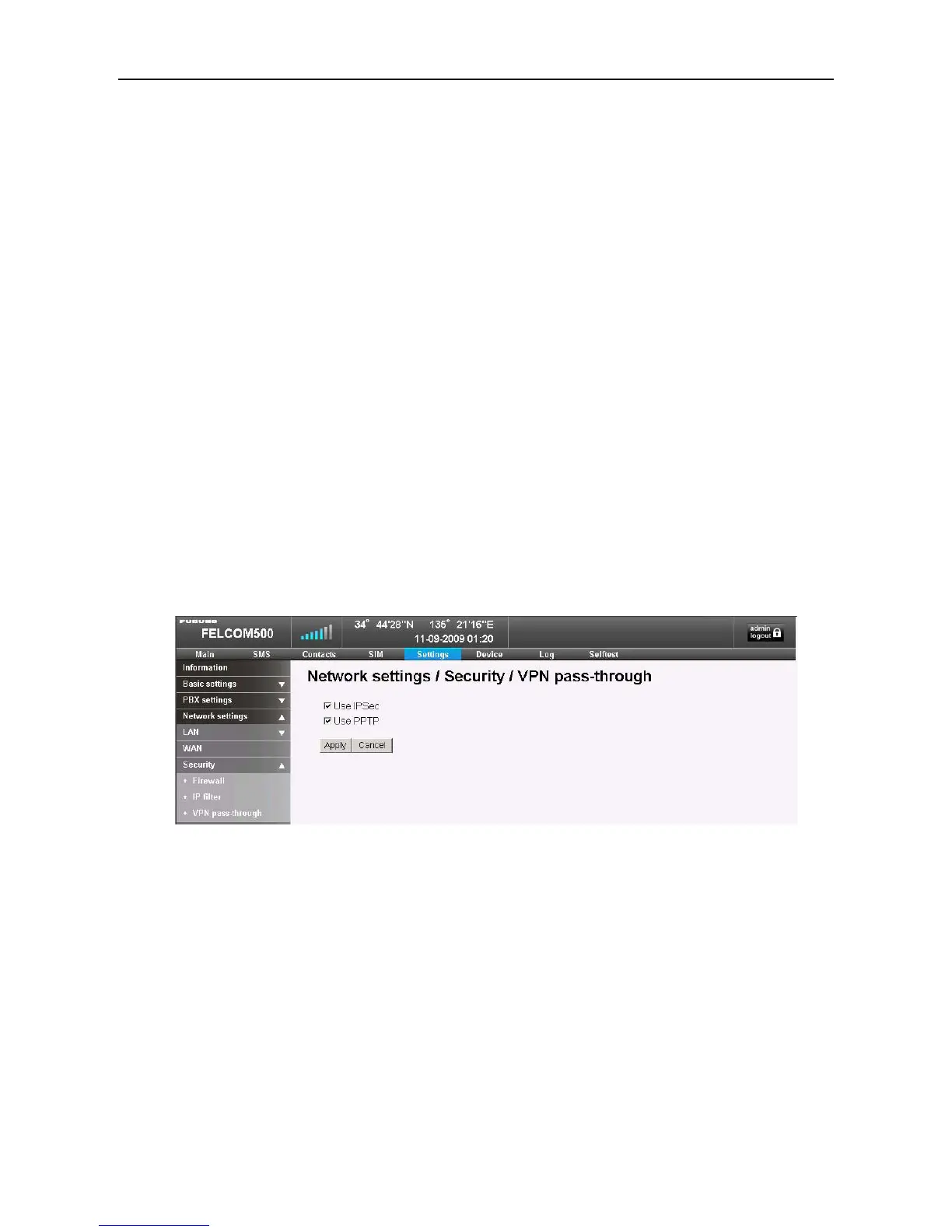
8.1.3 VPN pass-through
This setting should be implemented by the administrator. The outline of the
procedure will be described here.
IPSec: IP Security Protocol、PPTP: Point-to-Point Tunneling Protocol
This protocol is used for encrypting the VPN (Virtual Private Network) connection for
the security of the communication.
Place ticks for both of them in normal cases to make these protocols valid.
Reference) What is VPN?
Internet has communications established by an unspecified number of users where
each of the users selects an appropriate route for him/herself. However, it is true
that the security for the communication route is not being sufficiently considered.
The reason is because communications are not made via LAN connections using
dedicated lines.
Based on such circumstances, VPN has been developed as a technology for using the
Internet line by ensuring the security of the “END to END” communication by
assigning IPsec or PPTP for specific users.
The information security is improved by making a PC located in a physically long
distance seem as if it is located within the LAN network.

 Loading...
Loading...