10-10
Catalyst 6500 Series Switch and Cisco 7600 Series Router Firewall Services Module Configuration Guide
OL-6392-01
Chapter 10 Controlling Network Access with Access Control Lists
Access Control List Overview
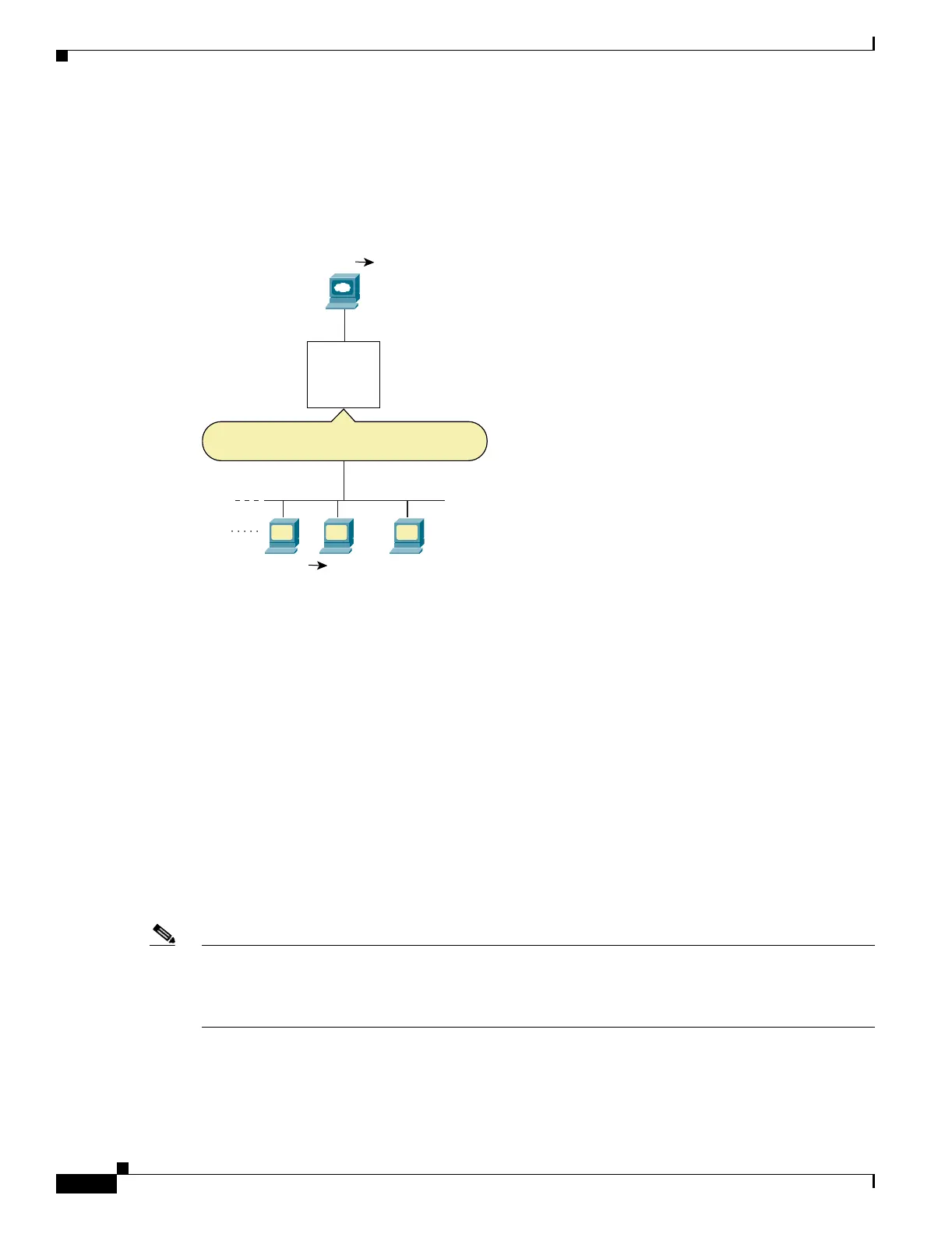
If you perform NAT on both interfaces, then keep in mind the addresses that are visible to a given
interface. In Figure 10-3, an outside server uses static NAT so that a translated address appears on the
inside network.
Figure 10-3 IP Addresses in ACLs: NAT used for Source and Destination Addresses
See the following commands for this example:
FWSM/contexta(config)# access-list INSIDE extended permit ip 10.1.1.0 255.255.255.0 host
10.1.1.56
FWSM/contexta(config)# access-group INSIDE in interface inside
For an example of IP addresses used in outbound ACLs, see Figure 10-5 on page 10-12.
Inbound and Outbound Access Control Lists
Traffic flowing across an interface in the FWSM can be controlled in two ways. Traffic that enters the
FWSM can be controlled by attaching an inbound ACL to the source interface. Traffic that exits the
FWSM can be controlled by attaching an outbound ACL to the destination interface. To allow any traffic
to enter the FWSM, you must attach an inbound ACL to an interface; otherwise, the FWSM
automatically drops all traffic that enters that interface. By default, traffic can exit the FWSM on any
interface unless you restrict it using an outbound ACL, which adds restrictions to those already
configured in the inbound ACL.
Note “Inbound” and “outbound” refer to the application of an ACL on an interface, either to traffic entering
the FWSM on an interface or traffic exiting the FWSM on an interface. These terms do not refer to the
movement of traffic from a lower security interface to a higher security interface, commonly known as
inbound, or from a higher to lower interface, commonly known as outbound.
209.165.200.225
10.1.1.0/24
Inside
Outside
Static NAT
10.1.1.56
ACL
Permit from 10.1.1.0/24 to 10.1.1.56
PAT
209.165.201.4:port10.1.1.0/24
104635
 Loading...
Loading...

















