5-9
Catalyst 6500 Series Switch and Cisco 7600 Series Router Firewall Services Module Configuration Guide
OL-6392-01
Chapter 5 Managing Security Contexts
Security Context Overview
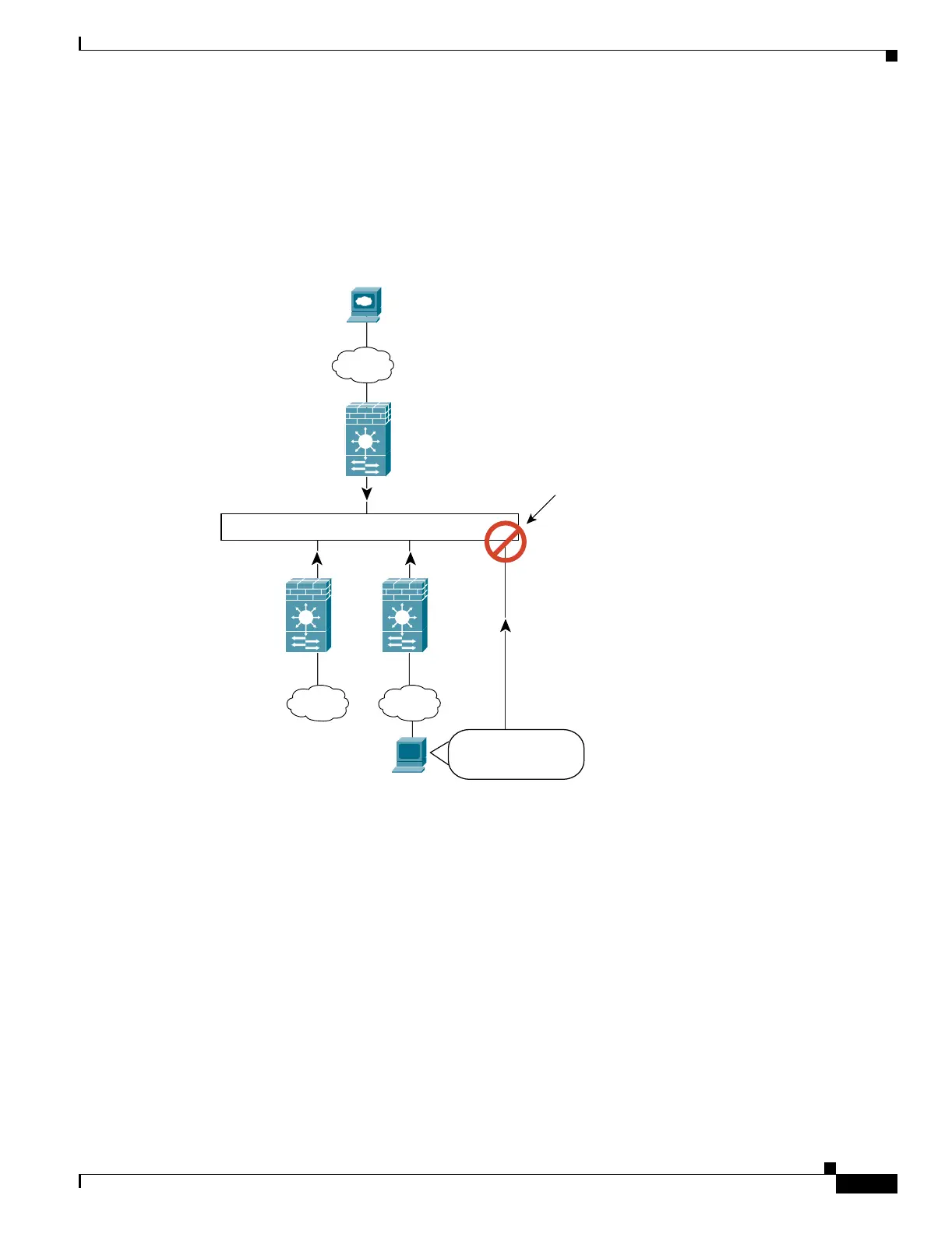
Because of the limitation for originating traffic on a shared VLAN, a scenario where you place one
context behind another is not practical because you would have to configure static statements in the top
context for every single outside address that users connected to the bottom context want to access. (See
Figure 5-7.)
Figure 5-7 Cascading Context Limitations
Logging into the FWSM in Multiple Context Mode
When you session into the FWSM, you access the system execution space. If you later configure Telnet
or SSH access to a context, you can log into a specific context. If you log into a specific context, you can
only access the configuration for that context. However, if you log into the admin context or session into
the system execution space, you can access all contexts.
When you change to a context from admin, you continue to use the username and command
authorization settings set in the admin context.
The system execution space does not support any AAA commands, but you can configure its own login
and enable passwords, as well as usernames in the local database to provide individual logins.
Admin
Context
Context A
Gateway
Context
VLAN 301
VLAN 300
Host
Shared VLAN 200
www.cisco.com
209.165.201.4
Internet
HTTP Packet
Dest. Address:
209.165.201.4
InsideInside
IP Address Classifier
Classifier does not know whether
to send packet to Admin context or
Gateway context.
104640
 Loading...
Loading...

















