5-7
Catalyst 6500 Series Switch and Cisco 7600 Series Router Firewall Services Module Configuration Guide
OL-6392-01
Chapter 5 Managing Security Contexts
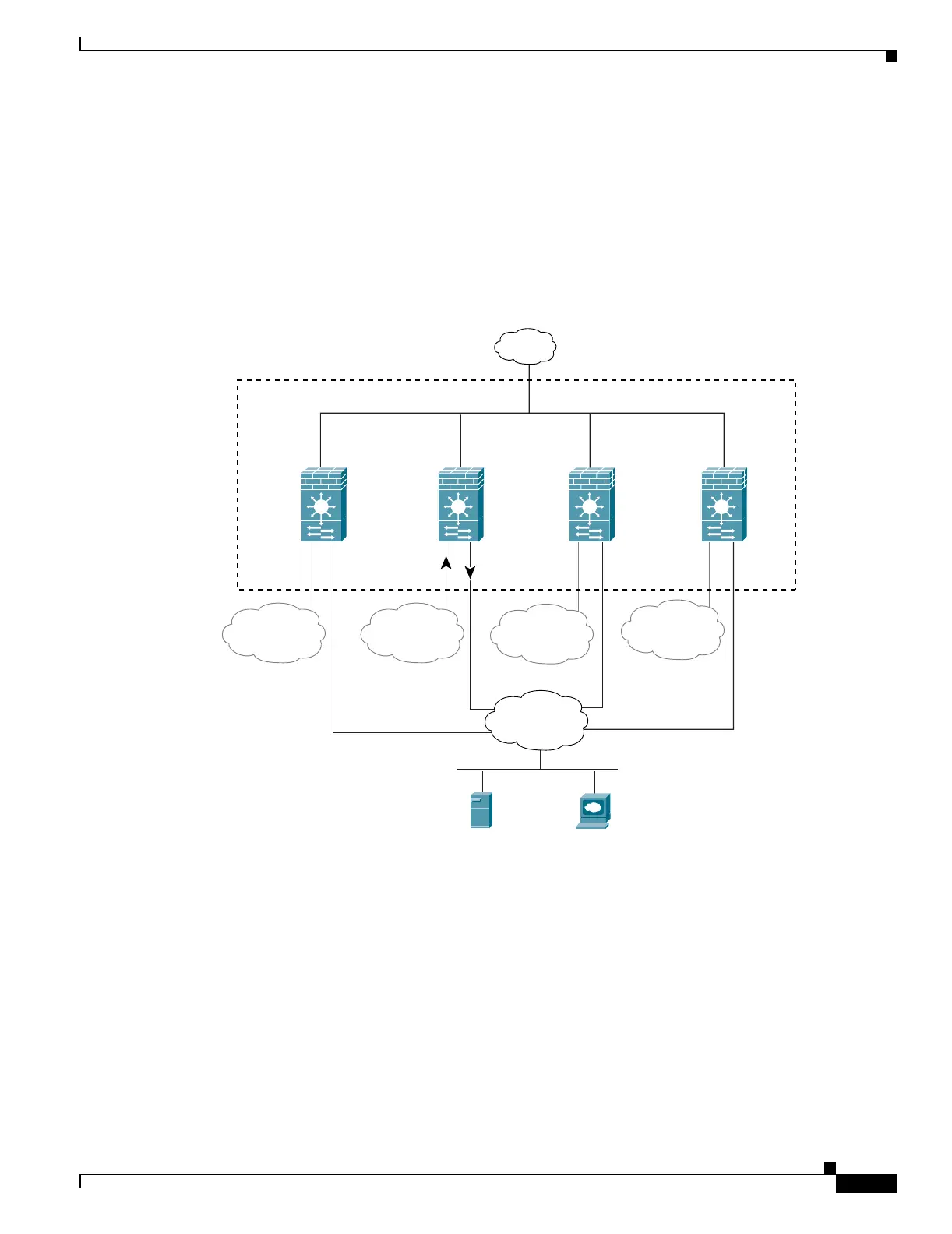
Security Context Overview
Alternatively, you can share a VLAN on the inside of each context and place the shared resources on a
DMZ, labeled “VLAN 300” in Figure 5-5. The downside of placing the shared network inside each
context is that you must configure the interface for all contexts; however, this task can be simplified by
cutting and pasting between context configurations, and changing only the interface IP address. You also
need to make sure that traffic cannot go from one context to another, using the shared network as an
interim hop. For example, you could disallow any traffic from originating on the shared network. If you
need to originate traffic on the shared interface, for example, to access the Internet, then refer to the
“Shared Interface Limitations” section.
Figure 5-5 Shared Resources on a Shared DMZ
Shared Interface Limitations
For traffic originating on a shared interface, you must configure a static NAT statement for the
destination address within a context. This requirement is valid for accessing both higher security
interfaces (outside to inside, where a static NAT translation is already required) as well as lower security
interfaces (inside to outside), such as connecting to the Internet. This requirement exists because the
FWSM classifier must use a unique IP address to determine to which context to send traffic (when you
use a shared VLAN, the classifier cannot use the VLAN to classify traffic). However, the FWSM
classifier only “knows” about context addresses from already existing NAT translations (returning
traffic) and from static NAT translations.
Inside
Customer A
Admin
Network
Inside
Customer B
Inside
Customer C
Shared
Network
Admin
Context
Context A Context B
VLAN 203 VLAN 204VLAN 202
VLAN 300 VLAN 300
VLAN 300
VLAN 300
Syslog Server AAA Server
VLAN 201
VLAN 200
Context C
Switch
Internet
104663
 Loading...
Loading...

















