4-8
Catalyst 6500 Series Switch and Cisco 7600 Series Router Firewall Services Module Configuration Guide
OL-6392-01
Chapter 4 Configuring the Firewall Mode
Firewall Mode Overview
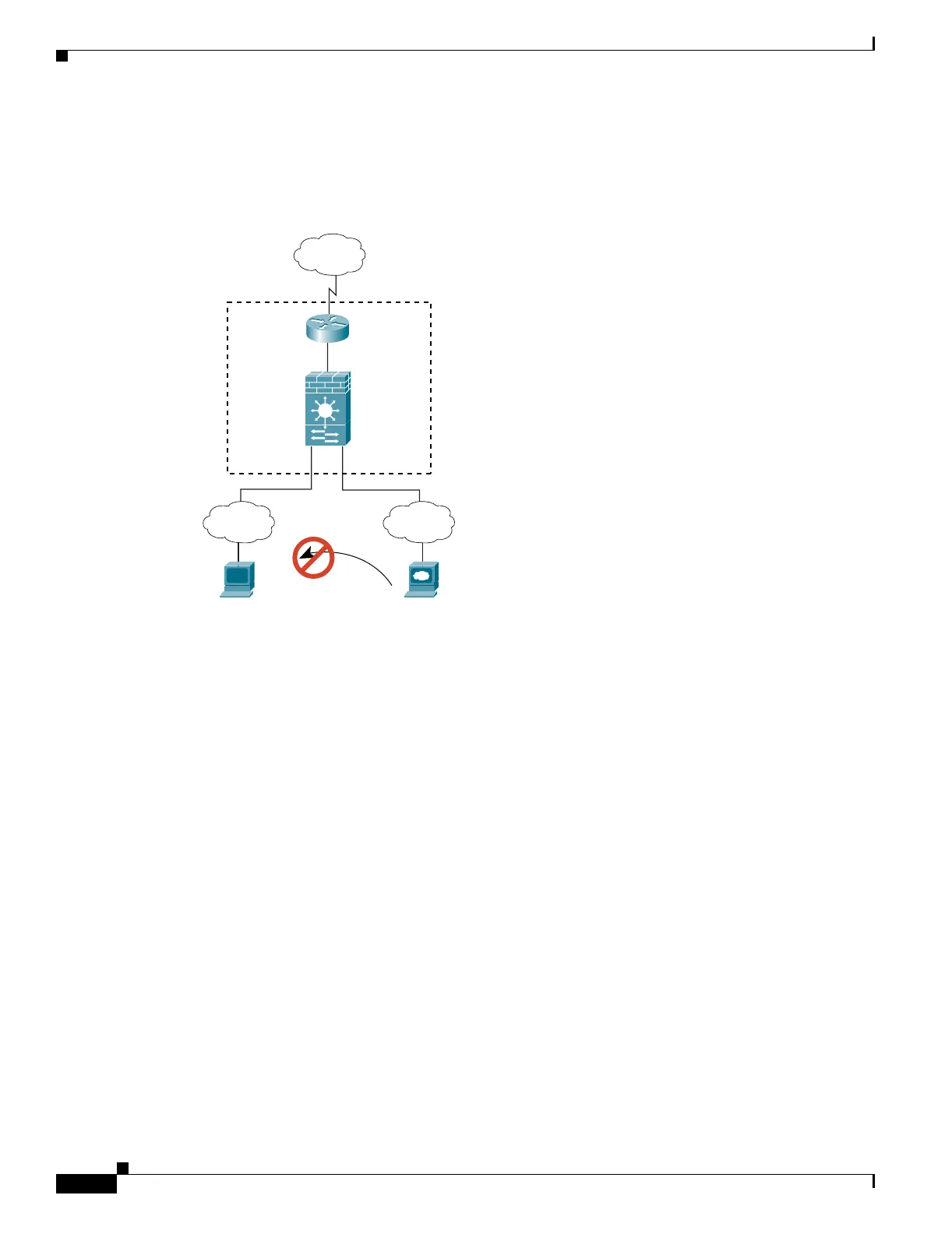
An DMZ User Attempts to Access an Inside Host
Figure 4-6 shows a user in the DMZ attempting to access the inside network.
Figure 4-6 DMZ to Inside
The steps below describe how data moves through the FWSM (see Figure 4-6):
1. A user on the DMZ network attempts to reach an inside host. The DMZ host might know the real
address of an inside host, and because the DMZ does not have to route the traffic on the internet, the
private addressing scheme does not prevent routing.
2. The FWSM receives the packet, and because it is a new session, the FWSM verifies if the packet is
allowed according to the security policy (ACLs, filters, AAA).
3. The packet is denied, and the FWSM drops the packet and logs the connection attempt.
Transparent Mode Overview
This section describes transparent firewall mode, and includes the following topics:
• Transparent Firewall Features, page 4-9
• Using the Transparent Firewall in Your Network, page 4-10
• Transparent Firewall Guidelines, page 4-11
• How Data Moves Through the Transparent Firewall, page 4-12
Web Server
10.1.1.3
User
10.1.2.27
FWSM
Outside
Inside DMZ
Switch
209.165.201.2
10.1.1.110.1.2.1
104641
 Loading...
Loading...

















