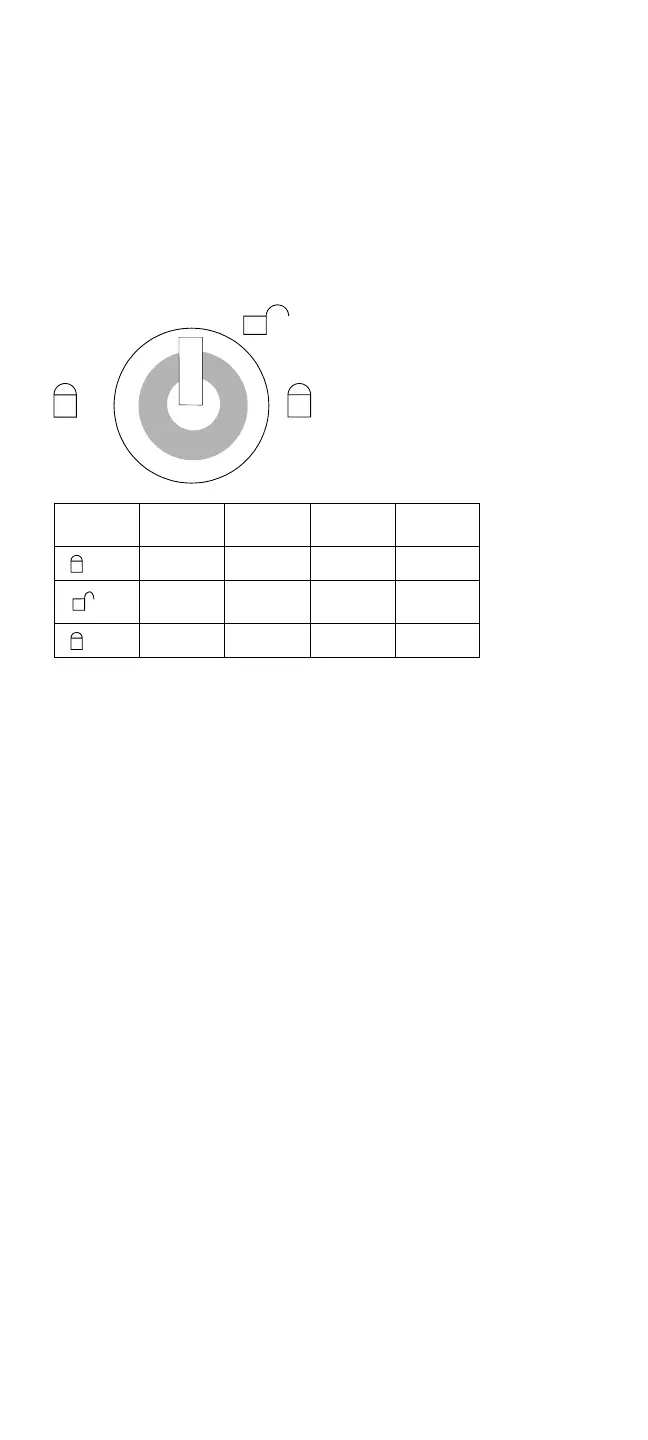
The key lock has three positions.
2
1
Security Hole: A hole for the Kensington** lock is
located at the rear of the Dock II. The cable on the
Kensington lock is looped around a stable chair or a
similar item and the Kensington lock is attached to the hole
at the rear of the Dock II. This prevents the Dock II to be
carried away by an unauthorized person.
Icon Cover
Lock
Computer
Lock
Power
Secured
Key
1
Lock Lock No Removable
Unlock Unlock No Not
Removable
2
Lock Lock Yes Removable
Main Card
SCSI Subsystem: The Dock II supports the SCSI
controller and BIOS which has functions similar to the
Adaptec AHA-1530P** Adapter. The Dock II also supports
the IBM SCSI device for PS/2*.
SCSI Devices:
The SCSI controller on the main card
supports up to seven SCSI devices (includes internal and
external). Two of the seven devices can be installed
inside the Dock II.
Terminators:
The terminator requirements for SCSI
devices are:
The last device in an external SCSI chain must have
the terminator installed. Some devices may require
more than one terminator.
All other external SCSI devices must have the
terminators removed.
The internal SCSI device must have the terminator
installed.
The location and appearance of the terminators may vary
from device to device. An identification label or tag
(usually “T-RES”) is attached to each terminator for easy
identification.
Dock II (3546)
423
 Loading...
Loading...











