Configure a Beacon G6
Security configuration
Configuring access control
4. Click Add + to add more website URLs to be blocked or click Done.
END OF STEPS
7.50 Configuring access control
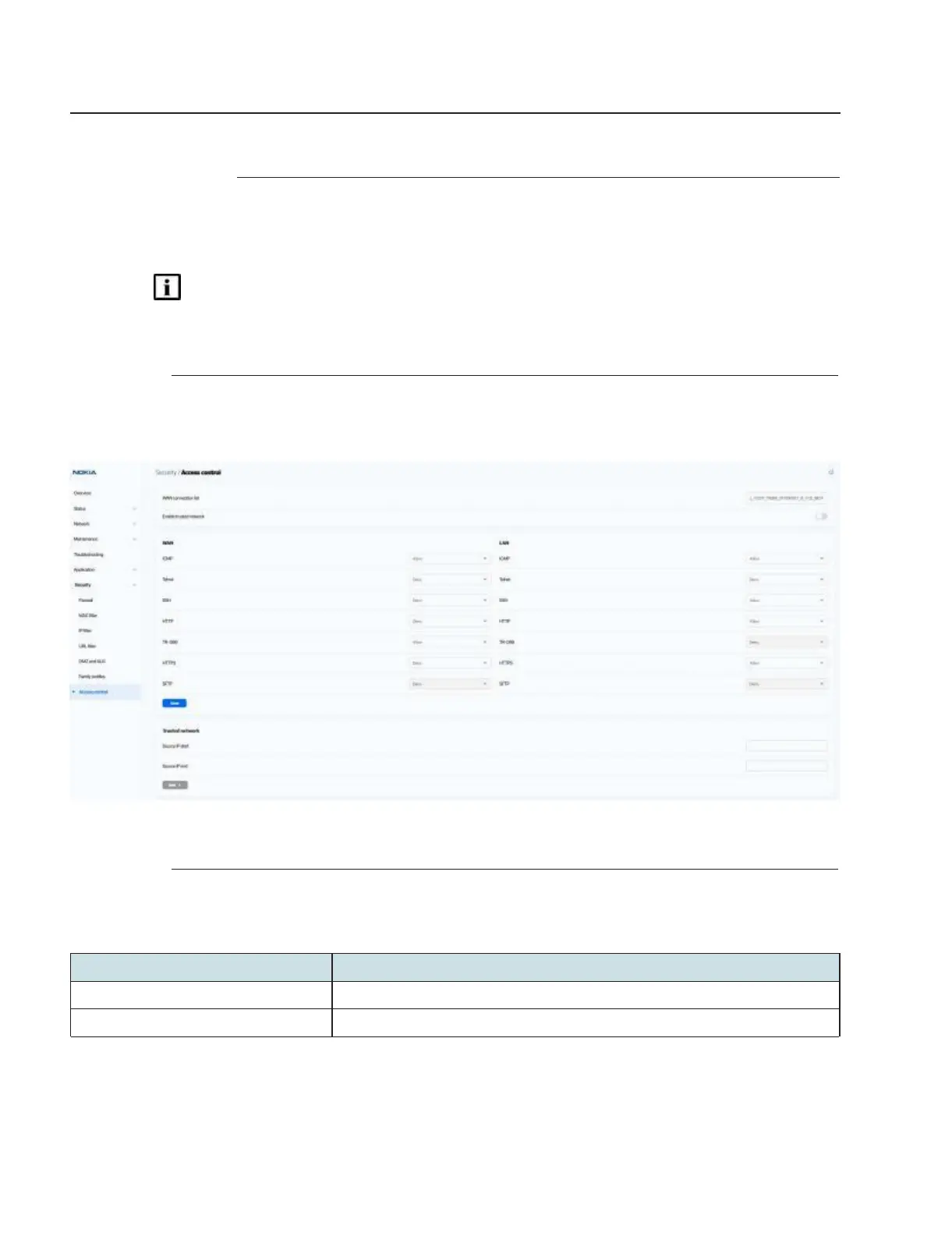
This procedure describes how to configure the access control level (ACL).
Note: ACL takes precedence over the firewall policy.
The trusted network will be shared for all WAN connections; it is not applied individually to a
WAN connection.
1
Click Security→Access control in the left pane. The Access control page displays.
Figure 7-54 Access control page
2
Configure the following parameters:
Table 7-37 Access control parameters
Select a WAN connection from the list.
Select the toggle button to enable a trusted network.
Use subject to agreed restrictions on disclosure and use.
154 3FE-49949-AAAA-TCZZA
 Loading...
Loading...











