1-5
Cisco ASA Series CLI Configuration Guide
Chapter 1 Configuring Cisco Unified Presence
Information About Cisco Unified Presence
Security Certificate Exchange Between Cisco UP and the Security
Appliance
You need to generate the keypair for the certificate (such as cup_proxy_key) used by the ASA, and
configure a trustpoint to identify the self-signed certificate sent by the ASA to Cisco UP (such as
cup_proxy) in the TLS handshake.
For the ASA to trust the Cisco UP certificate, you need to create a trustpoint to identify the certificate
from the Cisco UP (such as
cert_from_cup), and specify the enrollment type as terminal to indicate that
you will paste the certificate received from the Cisco UP into the terminal.
XMPP Federation Deployments
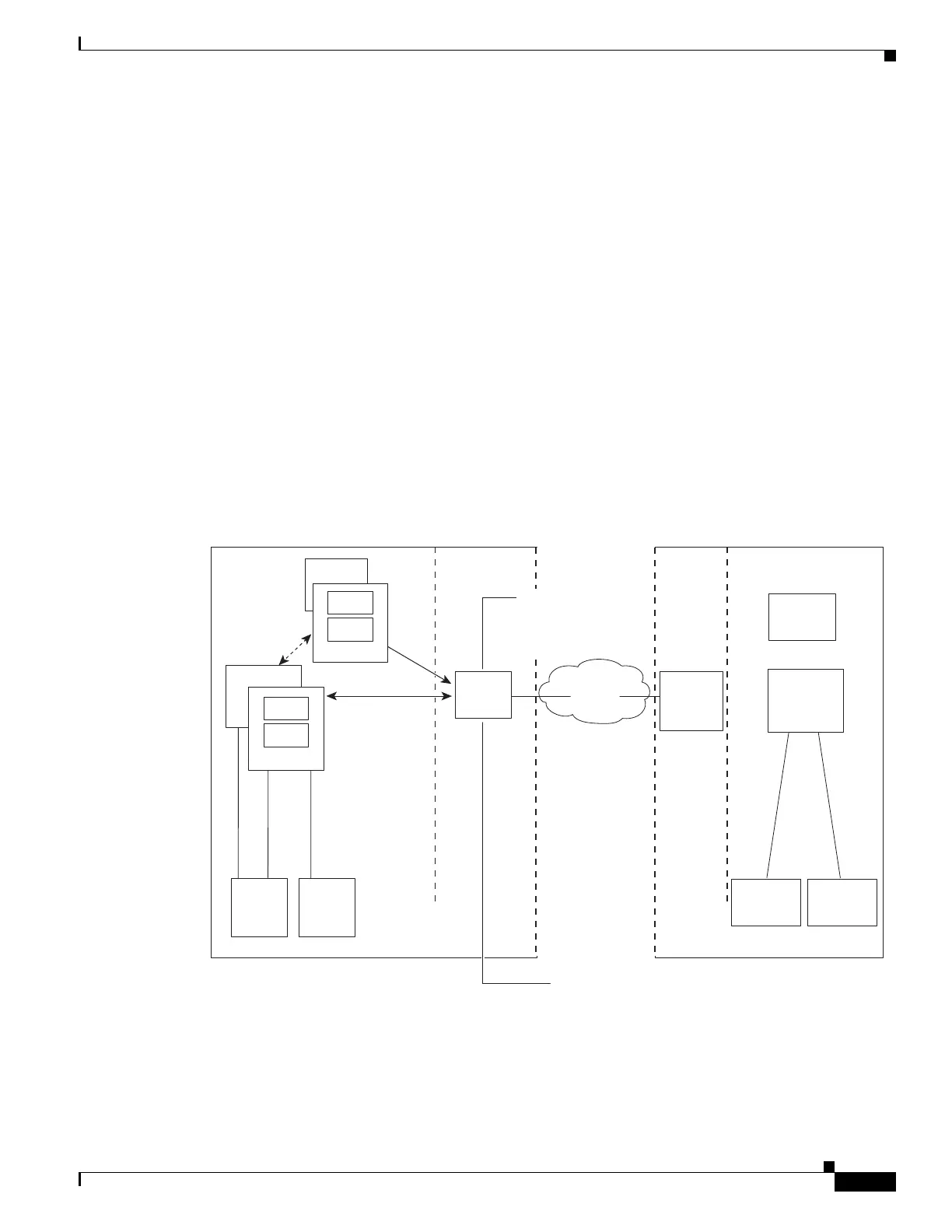
Figure 1-4 provides an example of an XMPP federated network between Cisco Unified Presence
enterprise deployment and an IBM Sametime enterprise deployment. TLS is optional for XMPP
federation. ASA acts only as a firewall for XMPP federation; it does not provide TLS proxy functionality
or PAT for XMPP federation.
Figure 1-4 Basic XMPP Federated Network between Cisco Unified Presence and IBM Sametime
XMPP
Client
(Tom)
277887
Internet
CUCM
CUCM
Enterprise X Enterprise Z
DMZ DMZprivate private network
ASA functions as:
• Firewall
• Open Port 5269
Pass-through for
XMPP Requests
No Termination
of connections
*ASA
XMPP
CUP (US)
CUP
CUP
CUP (UK)
CUP
CUP
Inter-cluster
communication
*Cisco Adaptive Security Appliance
Sametime
(Bob)
Sametime
(Bill)
IBM
Sametime
Gateway
Directory
IBM
Sametime
Gateway
IBM
Sametime
Server
XMPP
Client
(Ann)
 Loading...
Loading...















