1-7
Cisco ASA Series CLI Configuration Guide
Chapter 1 Configuring the Identity Firewall
Licensing for the Identity Firewall
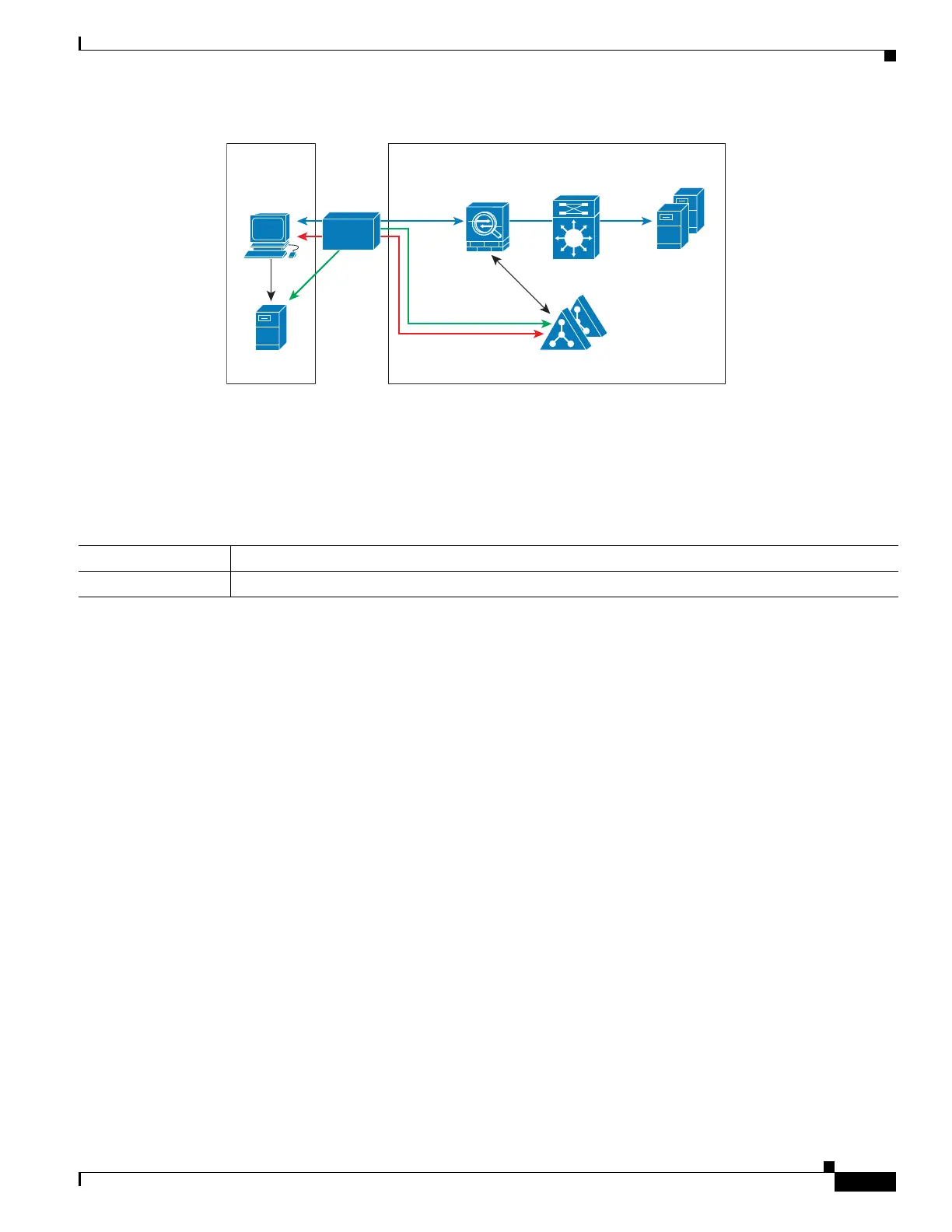
Figure 1-7 WAN-based Deployment with Remote AD Agent and AD Servers
Licensing for the Identity Firewall
The following table shows the licensing requirements for this feature:
Guidelines and Limitations
This section includes the guidelines and limitations for this feature.
Context Mode Guidelines
Supported in single and multiple context mode.
Firewall Mode Guidelines
Supported in routed and transparent firewall modes.
Failover Guidelines
The Identity Firewall supports user identity-IP address mappings and AD Agent status replication from
active to standby when stateful failover is enabled. However, only user identity-IP address mappings,
AD Agent status, and domain status are replicated. User and user group records are not replicated to the
standby ASA.
When failover is configured, the standby ASA must also be configured to connect to the AD Agent
directly to retrieve user groups. The standby ASA does not send NetBIOS packets to clients even when
the NetBIOS probing options are configured for the Identity Firewall.
When a client is determined as inactive by the active ASA, the information is propagated to the standby
ASA. User statistics are not propagated to the standby ASA.
When you have failover configured, you must configure the AD Agent to communicate with both the
active and standby ASA devices. See the Installation and Setup Guide for the Active Directory Agent for
the steps to configure the ASA on the AD Agent server.
Client
ASA
AD ServersAD Agent
304006
Remote Site Enterprise Main Site
RADIUS
mkg.example.com
10.1.1.2
WMI
Login/Authentication
LDAP
WAN
Model License Requirement
All models Base License.
 Loading...
Loading...















