and outgoing data packets. If a mapped MAC address stops receiving or sending
data, the switch will discard its address on the MAC table. Thus, processing time for
inspecting the address table is decreased and performance of the switch is
increased.
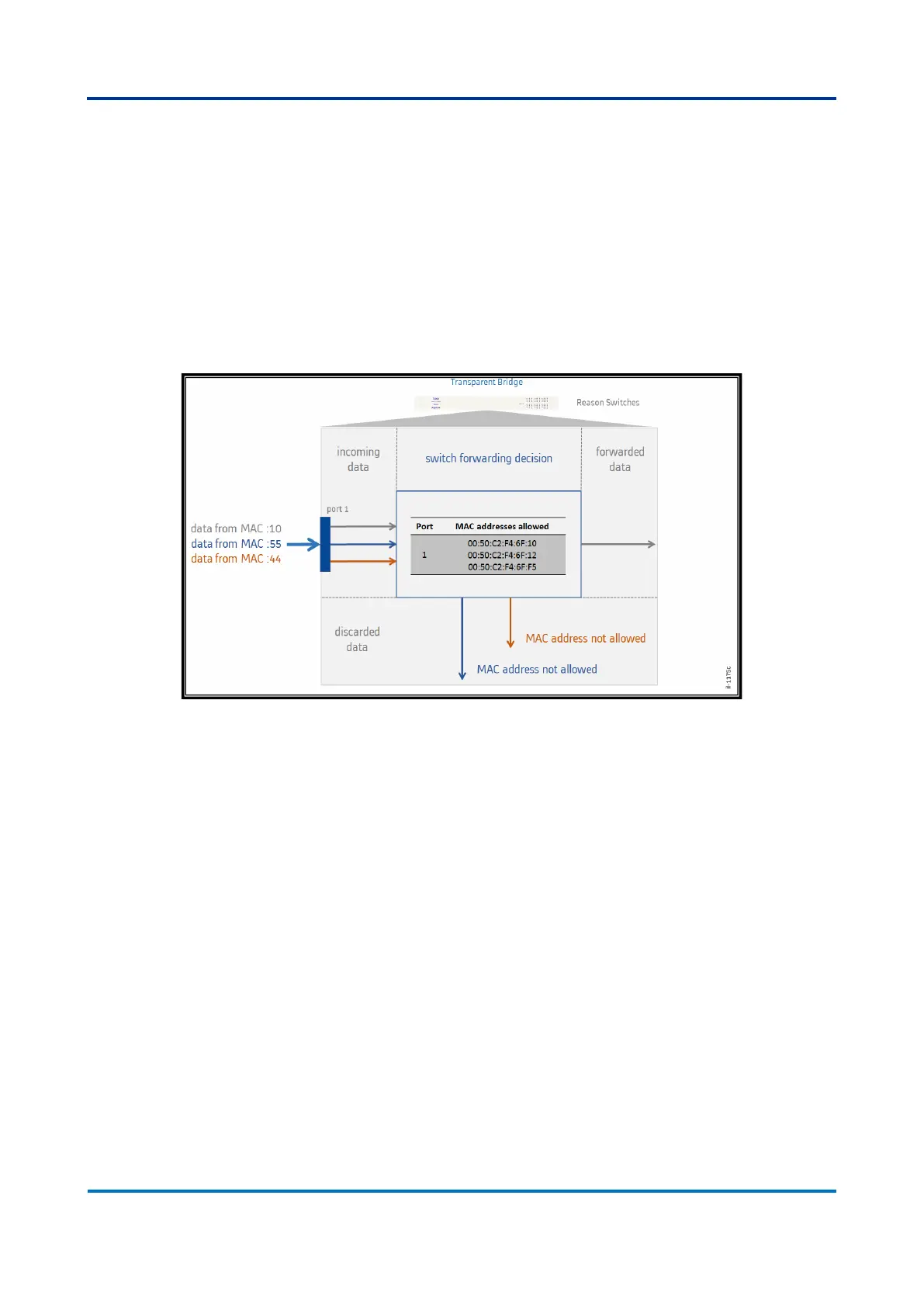
It is possible, for security reasons, to restrict the access to a switch’s LAN by manually
inserting MAC addresses of the allowed hosts at a given interface. In this case, the
port will operate in secure mode, and the equipment will only forward traffic from set
MAC addresses and will drop data from MAC addresses which are not set. Thus, it is
possible to limit LAN access only by MAC addresses. The following figure shows how
MAC access management works in the switch.
Figure 40: LAN access restriction with MAC address configuration
 Loading...
Loading...