S
ECURE
S
HELL
C
OMMANDS
22-21
Secure Shell Commands
This section describes the commands used to configure the SSH server.
Note that you also need to install a SSH client on the management station
when using this protocol to configure the switch.
Note: The switch supports both SSH Version 1.5 and 2.0 clients.
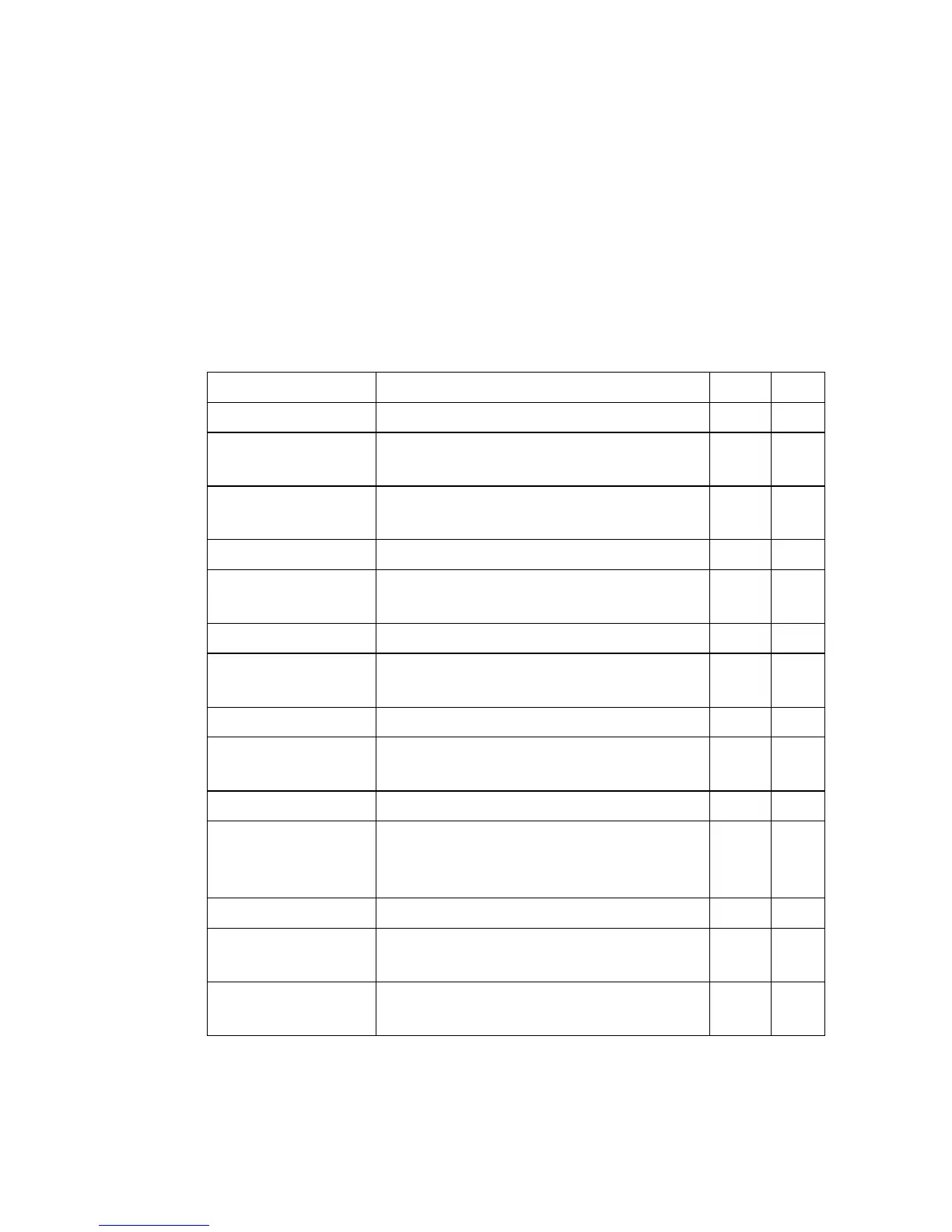
Table 22-10 Secure Shell Commands
Command Function Mode Page
ip ssh server Enables the SSH server on the switch GC 22-24
ip ssh timeout Specifies the authentication timeout for the
SSH server
GC 22-25
ip ssh
authentication-retries
Specifies the number of retries allowed by a
client
GC 22-26
ip ssh server-key size Sets the SSH server key size GC 22-27
copy tftp public-key Copies the user’s public key from a TFTP
server to the switch
PE 20-13
delete public-key Deletes the public key for the specified user PE 22-28
ip ssh crypto
host-key generate
Generates the host key PE 22-28
ip ssh crypto zeroize Clear the host key from RAM PE 22-29
ip ssh save host-key Saves the host key from RAM to flash
memory
PE 22-30
disconnect Terminates a line connection PE 20-31
show ip ssh Displays the status of the SSH server and
the configured values for authentication
timeout and retries
PE 22-31
show ssh Displays the status of current SSH sessions PE 22-31
show public-key Shows the public key for the specified user
or for the host
PE 22-32
show users Shows SSH users, including privilege level
and public key type
PE 20-9

 Loading...
Loading...










