xStack® DES-3200 Series Layer 2 Managed Fast Ethernet Switch
218
After completing the preceding steps, a SSH Client on a remote PC can be configured to manage the Switch using
a secure, in band connection.
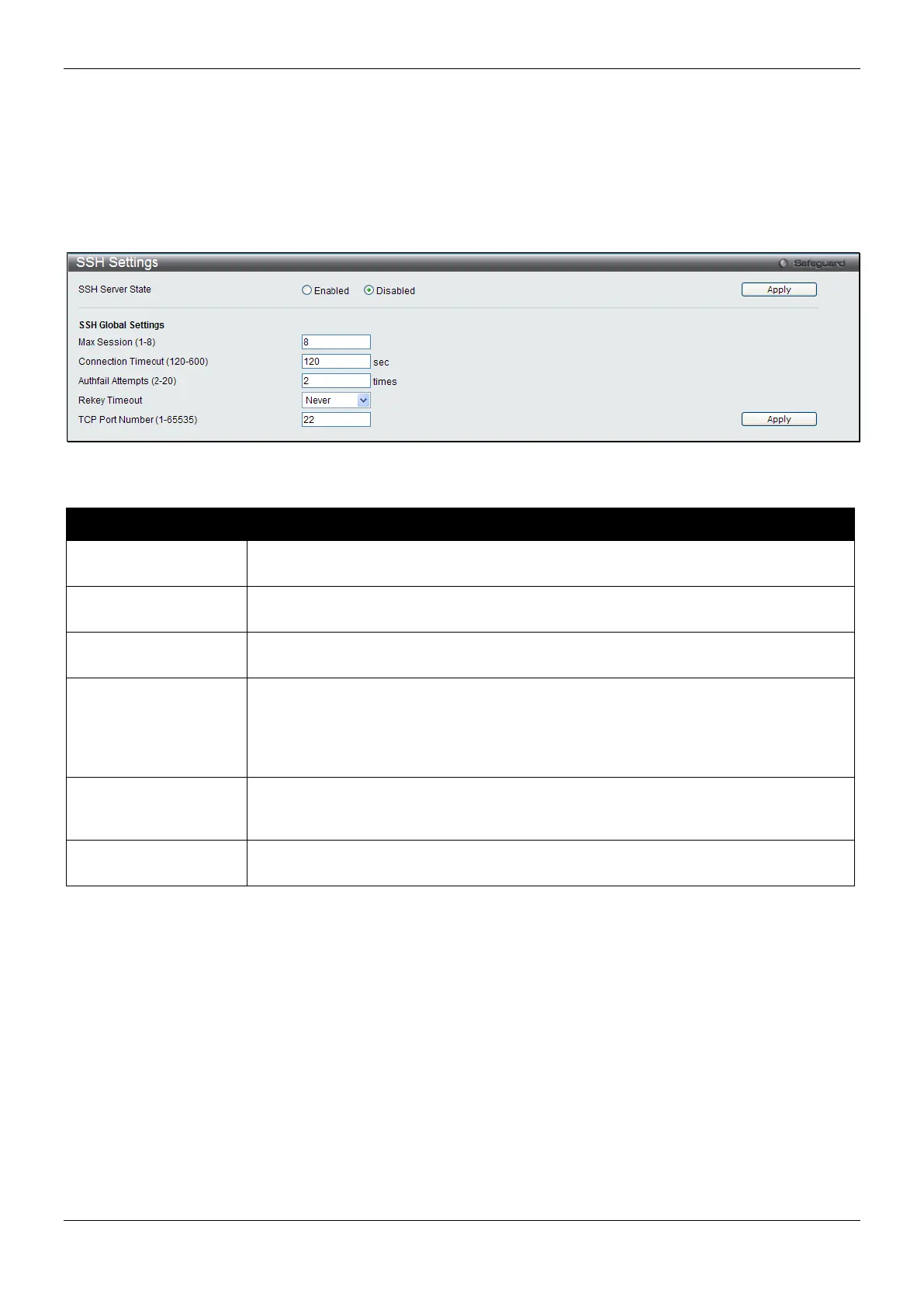
SSH Settings
Users can configure and view settings for the SSH server.
To view this window, click Security > SSH > SSH Settings as shown below:
Figure 8-60 SSH Settings window
The fields that can be configured are described below:
Parameter Description
SSH Server State
Use the radio buttons to enable or disable SSH on the Switch. The default is
Max. Session (1-8) Enter a value between 1 and 8 to set the number of users that may simultaneously
access the Switch. The default setting is 8.
Connection Timeout
Allows the user to set the connection timeout. The user may set a time between 120
and 600 seconds. The default setting is 120 seconds.
Authfail Attempts (2-
20)
Allows the Administrator to set the maximum number of attempts that a user may try
to log on to the SSH Server utilizing the SSH authentication. After the maximum
number of attempts has been exceeded, the Switch will be disconnected and the user
must reconnect to the Switch to attempt another login. The number of maximum
attempts may be set between 2 and 20. The default setting is 2.
Rekey Timeout
This field is used to set the time period that the Switch will change the security shell
encryptions by using the drop-down menu. The available options are Never, 10 min,
30 min, and 60 min. The default setting is Never.
TCP Port Number (1-
Here the user can enter the TCP Port Number used for SSH. The default value is 22.
Click the Apply button to accept the changes made for each individual section.
SSH Authentication Method and Algorithm Settings
Users can configure the desired types of SSH algorithms used for authentication encryption. There are three
categories of algorithms listed and specific algorithms of each may be enabled or disabled by ticking their
corresponding check boxes. All algorithms are enabled by default.
To view this window, click Security > SSH > SSH Authentication method and Algorithm Settings as shown
below:

 Loading...
Loading...











