MMX2 series – User's Manual 23
User
▪
Password
▪ No password is set by default, the authentication can be enabled after setting a password. The old
password is not necessary for modifying.
▪
characters.
▪ The device does not store the password string, so it can not be queried.
▪ The password can be reset by calling factory defaults (Reset to Factory Default Settings).
Follow the instructions to set the authentication:
Step 1. Network
(Setting a Password for Authentication).
Step 2.
Controller software (NetworkEnabling Authentication).
Step 3. Restart network services.
ATTENTION! The password will not be encrypted by this authentication mode, it remains accessible when
the communication happens on HTTP.
HTTP protocol uses clear text format for data transport. This method allows a third-party to listen in and
eavesdrop on the transferred information.
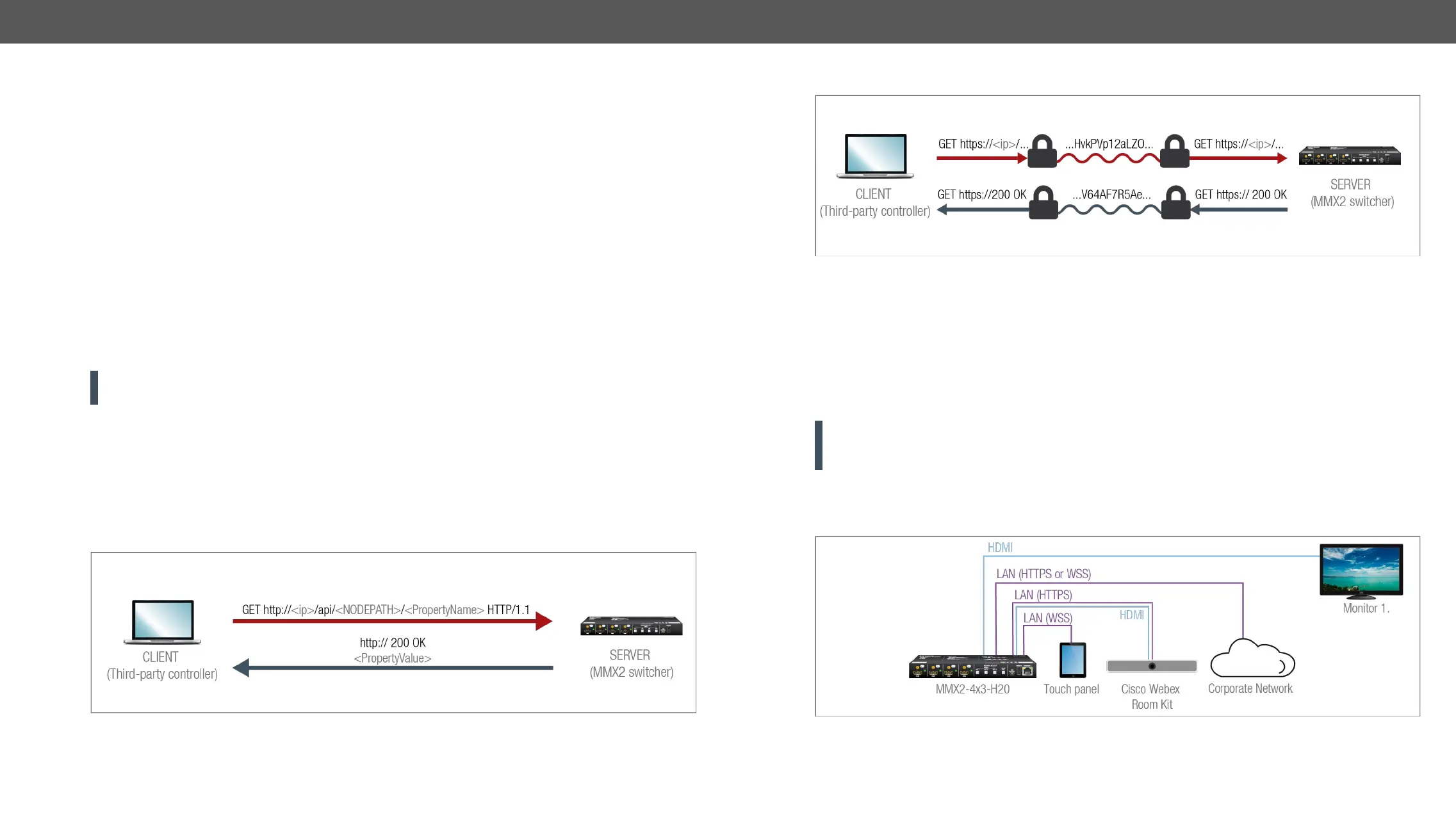
HTTP request-response
To ensure the secure data transmission, the HTTP port (80) can be disabled, and the all the information can
for a third-party and keeps the data secure.
HTTPS request-response
The same services are available on HTTPS as HTTP (for the detailed service list, see the
section).
▪ The
▪
▪
rejection.
ATTENTION! HTTPS does not guarantee that the communication is secure. Make sure that the client
communicates with the server directly, without any third-party element in the communication route
(Man-in-the-middle attack).
Basic Security System Example
by secured channels.

 Loading...
Loading...