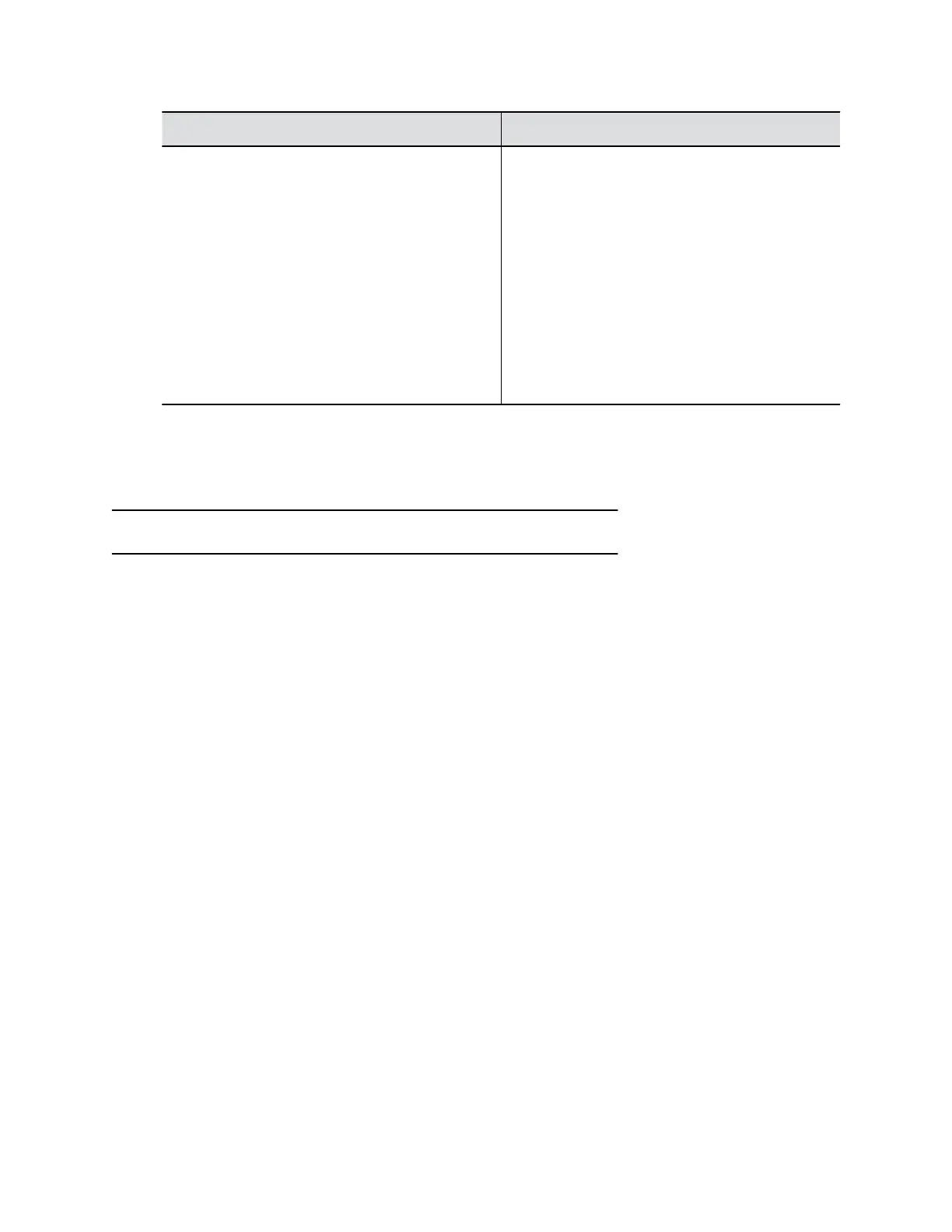
Setting Description
Login Mode Specifies the credentials necessary for a control
system to connect to the RS-232 port.
• Admin password only: (Default) Requires the
administrator password (if you set one) when
the control system connects.
• Username/Password: Requires the user name
and administrator password (if you set one)
when the control system connects.
• None: The system doesn’t require a user name
or password when the control system connects.
Note: This setting only displays when you set
RS-232 Mode to Control.
3. Select Save.
Disable USB 3.0 Ports
You can configure your G7500 system so no one can use its USB 3.0 ports.
Note: You can’t turn off the USB-C port, which only provides power.
Procedure
1. In the system web interface, go to Security > Access.
2. Select Disable All USB Ports.
PKI Certificates
If your organization uses a public key infrastructure (PKI) for securing network connections, Polycom
recommends that you have a strong understanding of certificate management and how it applies to your
G7500 system.
PKI certificates authenticate secure network connections to and from the G7500 system. The system
uses standard PKI techniques to configure and manage certificates and certificate signing requests
(CSRs). ANSI X.509 standards regulate the certificate characteristics.
Your system can generate CSRs to send to a certificate authority (CA), a trusted entity that validates and
officially issues, or signs, PKI certificates. Your system uses those certificates for client and server
authentication.
If your system is in an environment without PKI, you don’t need a CA-signed certificate; the system
comes with a self-signed certificate for its TLS connections. When you deploy PKI, however, self-signed
certificates aren’t trusted and you must use CA-signed certificates.
Here are some examples of how you use PKI certificates:
▪ If your environment uses the 802.1X authentication framework for wired connections, create a CSR
and install the resulting CA-signed certificate on your system so it’s trusted on the network.
▪ If you want to navigate with a browser over a secure connection to your system web interface,
create a CSR and install the resulting CA certificate chain on your system to replace its factory-
installed certificate, which is not trusted.
Securing the System
Polycom, Inc. 49

 Loading...
Loading...











