| Configuring the Security Features | 245
Managing the Server Certificates
The system can serve as a TLS server. When clients request a TLS connection with the system, the
system sends the server certificate (device certificate) to the clients for authentication.
About this task
The server certificate contains the default and the custom certificates, and you can specify the certificate
type sent by the endpoint to the client for authentication.
• Default Certificates: a unique server certificate and a generic server certificate.
Only if no unique certificate exists, the system may send a generic certificate for authentication.
• Custom Certificates: You can only upload one server certificate to the endpoint. The old server
certificate will be overridden by the new one. The server certificate must be in .pem or .cer file format
with the size less than 5M.
Procedure
1. On your web user interface, go to Security > Server Certs.
2. Configure and save the following settings:
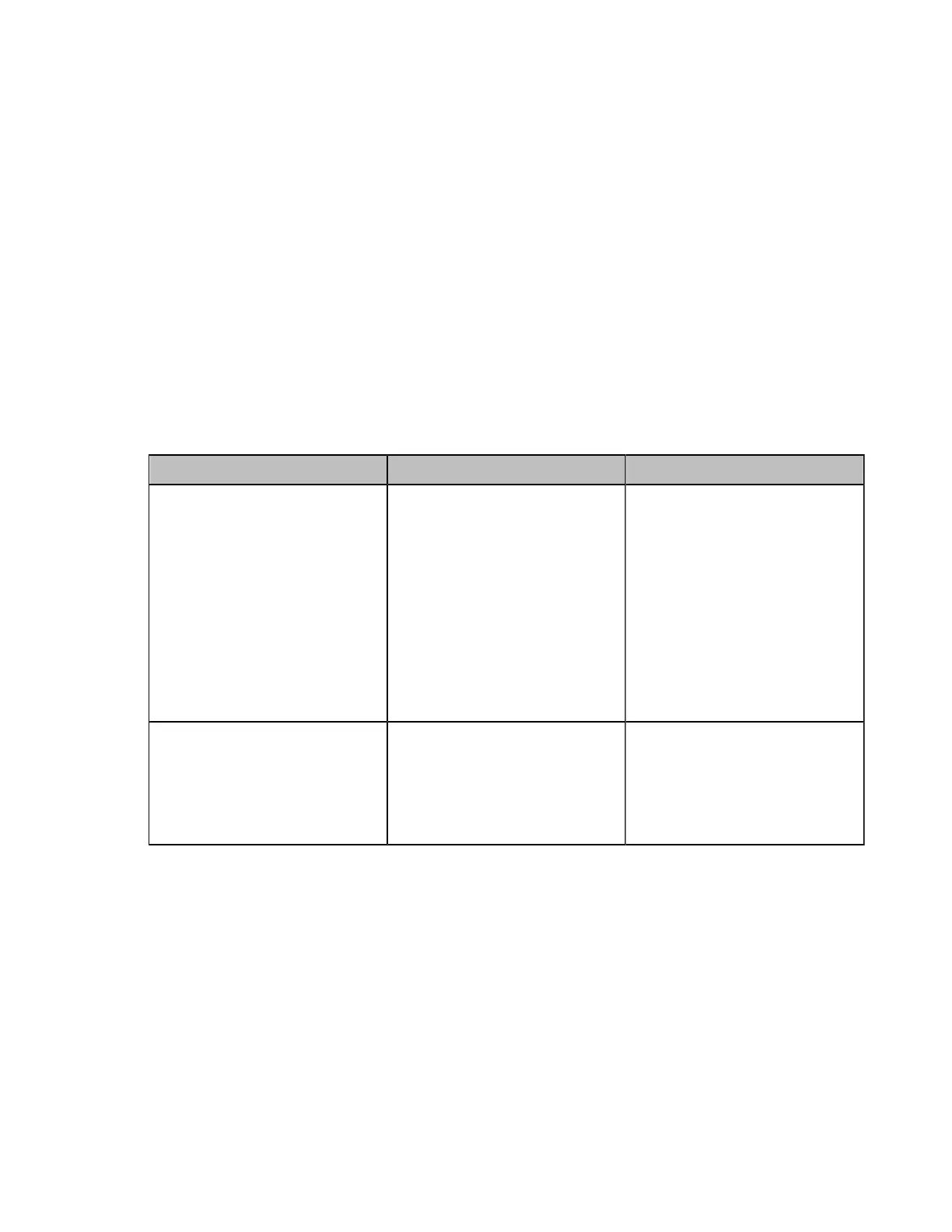
Parameter Description Configuration Method
Device Certificates
Specify the type of the server
certificates for the system to
send for TLS authentication.
• Default Certificates
• Custom Certificates
Note: the default value is Default
Certificates.
If you change this parameter, the
system will reboot to make the
change take effect.
Web user interface
Upload Server Certificate File
Upload the server certificate.
Note: the certificate must be
in .pem or .cer file format. Only
one server certificate can be
uploaded to the system.
Web user interface
Secure Real-Time Transport Protocol (SRTP)
Secure Real-Time Transport Protocol (SRTP) encrypts the RTP during SIP calls to avoid interception
and eavesdropping. The RTP and the RTP stream in a call are encrypted by AES algorithm which is
compliant with RFC3711. The data in the RTP stream cannot be understood even though it is captured or
intercepted. Only the receiver has the key to restore the data. To use SRTP, the parties participating in the
call must enable SRTP feature simultaneously. When this feature is enabled on both sites, the encryption
type used in the session is negotiated by the systems. This negotiation process is compliant with RFC
4568.
When you place a call that enables SRTP, the system sends an INVITE message with the RTP encryption
algorithm to the destination system.
The rules of SRTP for media encryption in SIP calls are described as below:

 Loading...
Loading...