the Firewall in the Device Manager, on page 118 for more information about configuring static routes in the
device manager.
Step 11 Click Add a Dynamic DNS (DDNS) method.
DDNS ensures the management center can reach the threat defense at its Fully-Qualified Domain Name
(FQDN) if the threat defense's IP address changes. See Device > System Settings > DDNS Ser viceto configure
DDNS.
If you configure DDNS before you add the threat defense to the management center, the threat defense
automatically adds certificates for all of the major CAs from the Cisco Trusted Root CA bundle so that the
threat defense can validate the DDNS server certificate for the HTTPS connection. The threat defense supports
any DDNS server that uses the DynDNS Remote API specification (https://help.dyn.com/remote-access-api/).
Step 12 Click Connect. The Registration Status dialog box shows the current status of the switch to the management
center. After the Saving Management Center/CDO Registration Settings step, go to the management center,
and add the firewall.
If you want to cancel the switch to the management center, click Cancel Registration. Otherwise, do not
close the device manager browser window until after the Saving Management Center/CDO Registration
Settings step. If you do, the process will be paused, and will only resume when you reconnect to the device
manager.
If you remain connected to the device manager after the Saving Management Center/CDO Registration
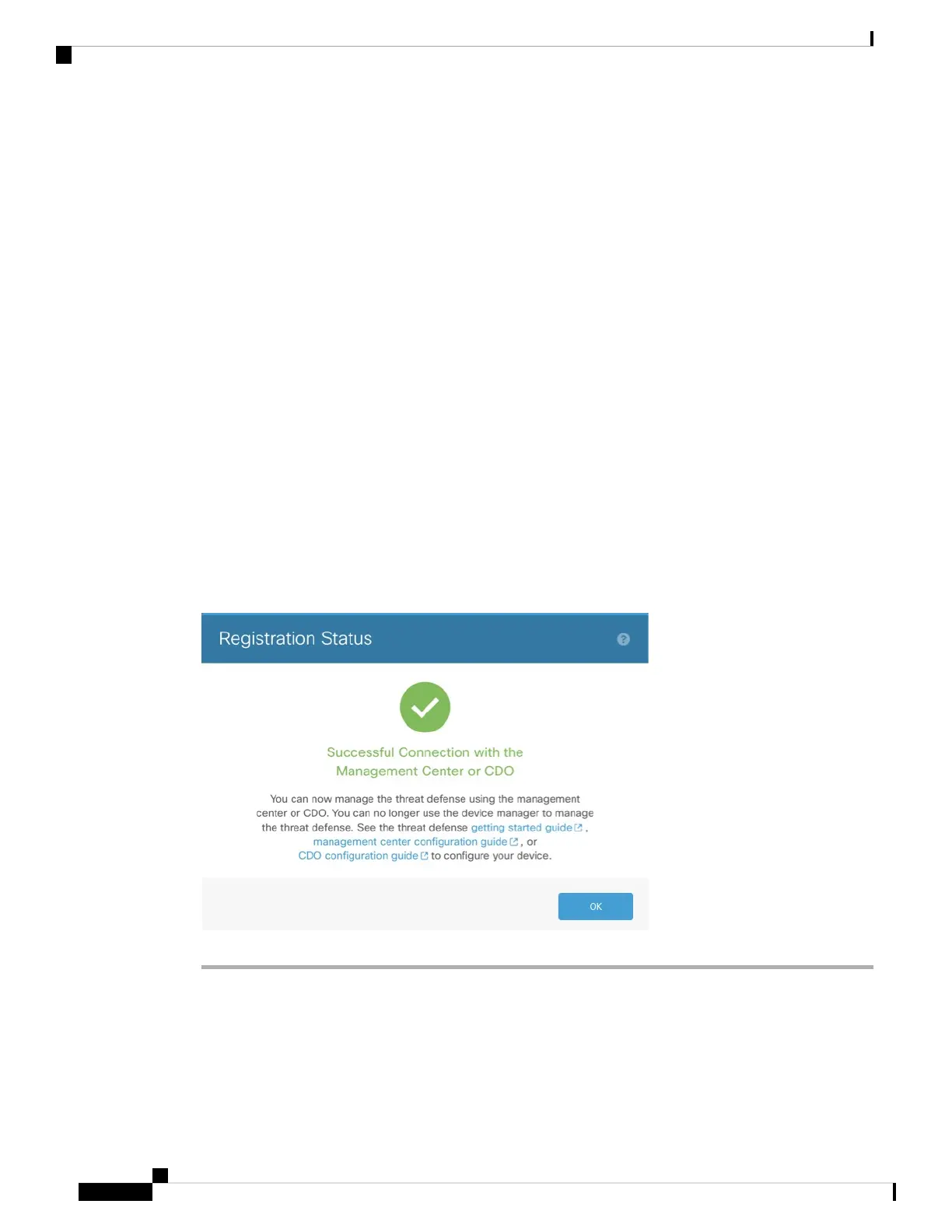
Settings step, you will eventually see the Successful Connection with Management Center or CDO dialog
box, after which you will be disconnected from the device manager.
Figure 37: Successful Connection
Pre-Configuration Using the CLI
Connect to the threat defense CLI to perform initial setup. When you use the CLI for initial configuration,
only the Management interface and manager access interface settings are retained. When you perform initial
setup using the device manager (7.1 and later), all interface configuration completed in the device manager
Cisco Firepower 2100 Getting Started Guide
60
Threat Defense Deployment with a Remote Management Center
Pre-Configuration Using the CLI
 Loading...
Loading...











