296 Matrix SPARSH VP110 User Guide
• EDH-RSA-DES-CBC3-SHA
• EDH-DSS-DES-CBC3-SHA
• DES-CBC3-SHA
• DHE-RSA-AES128-SHA
• DHE-DSS-AES128-SHA
• AES128-SHA
• IDEA-CBC-SHA
• DHE-DSS-RC4-SHA
• RC4-SHA
• RC4-MD5
• EXP1024-DHE-DSS-DES-CBC-SHA
• EXP1024-DES-CBC-SHA
• EDH-RSA-DES-CBC-SHA
• EDH-DSS-DES-CBC-SHA
•DES-CBC-SHA
• EXP1024-DHE-DSS-RC4-SHA
• EXP1024-RC4-SHA
• EXP1024-RC4-MD5
• EXP-EDH-RSA-DES-CBC-SHA
• EXP-EDH-DSS-DES-CBC-SHA
• EXP-DES-CBC-SHA
• EXP-RC4-MD5
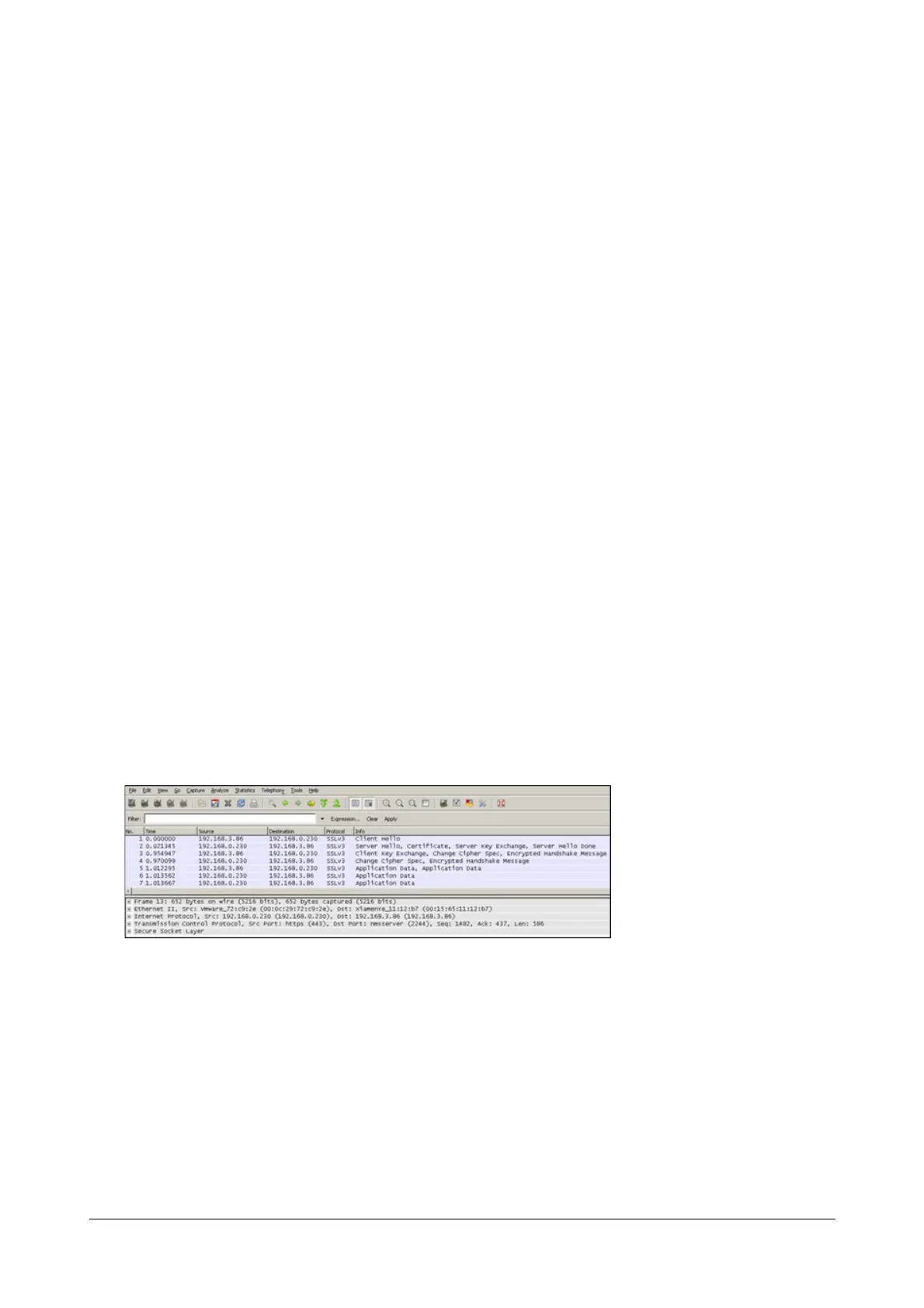
The following figure illustrates the TLS messages exchanged between the IP phone and TLS server to establish an
encrypted communication channel:
Step1: IP phone sends “Client Hello” message proposing SSL options.
Step2: Server responds with “Server Hello” message selecting the SSL options, sends its public key information in
“Server Key Exchange” message and concludes its part of the negotiation with “Server Hello Done” message.
Step3: IP phone sends session key information (encrypted by server’s public key) in the “Client Key Exchange”
message.
Step4: Server sends “Change Cipher Spec” message to activate the negotiated options for all future messages it
will send.
 Loading...
Loading...