D-Link DSR-Series User Manual 100
Section 7 - VPN
Self Certicate Requests
To request a self certicate to be signed by a CA, you can generate a Certicate Signing Request from the router
by entering identication parameters and passing it along to the CA for signing. Once signed, the CA’s Trusted
Certicate and signed certicate from the CA are uploaded to activate the self -certicate validating the identity
of this gateway. The self certicate is then used in IPsec and SSL connections with peers to validate the gateway’s
authenticity.
To generate a certicate signing request:
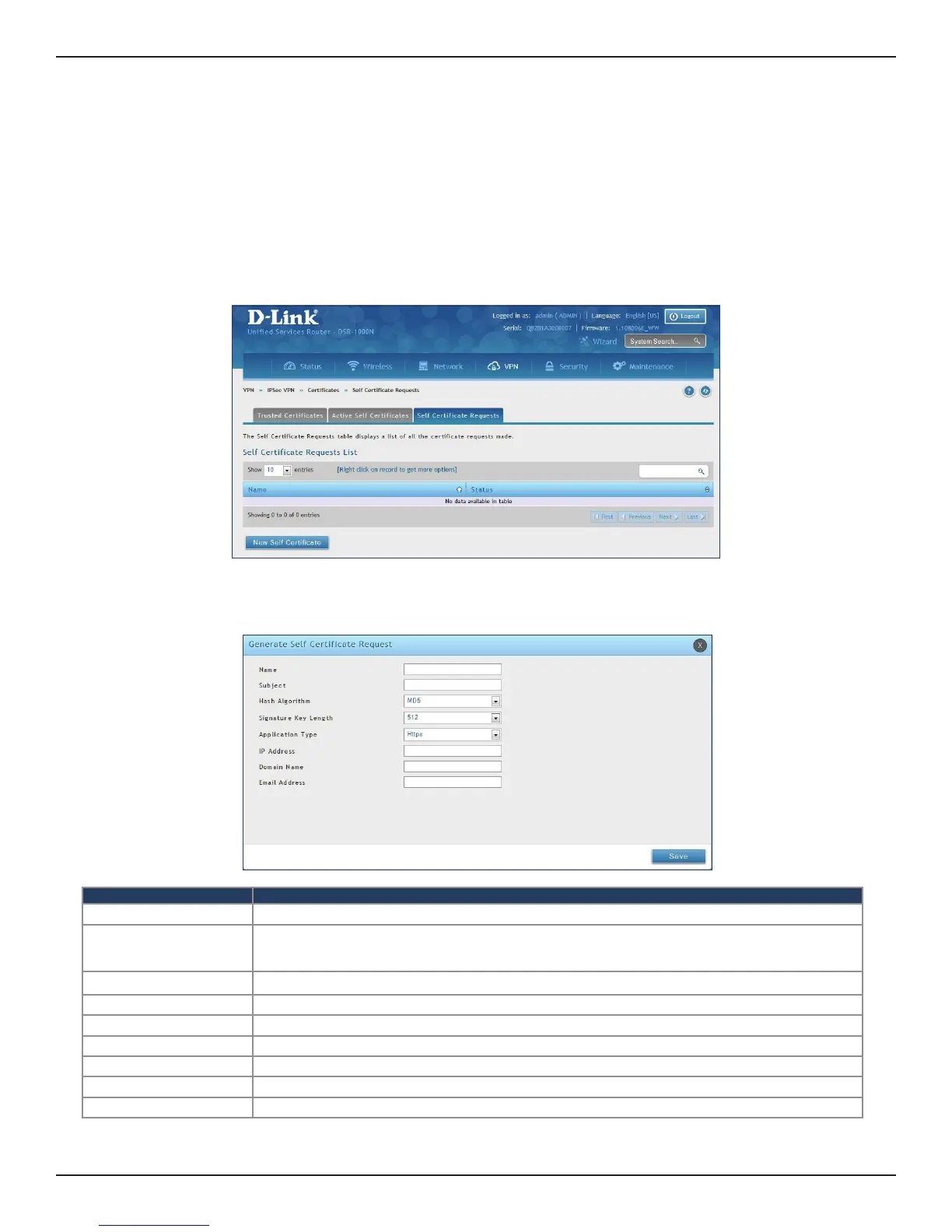
1. Click VPN > IPSec VPN > Certicates > Self Certicate Requests.
2. Click New Self Certicate.
3. Complete the elds in the table below and click Save.
Field Description
Name Enter a name (identier) for the certicate.
Subject
This eld will populate the CN (Common Name) entry of the generated certicate. Subject names are usually
dened in the following format: CN=<device name>, OU=<department>, O=<organization>, L=<city>,
ST=<state>, C=<country>. For example: CN=router1, OU=my_company, O=mydept, L=SFO, C=US.
Hash Algorithm Select the algorithm from the drop-down menu. Select either MD5 or SHA-1.
Signature Key Length Select the signature key length from the drop-down menu. Select either 512, 1024, or 2048
Application Type Select the application type from the drop-down menu. Select either HTTPS or IPSec.
IP Address Enter an IP address (optional).
Domain Name Enter a domain name (optional).
Email Address Enter your email address.
Save Click Save to save and activate your settings.

 Loading...
Loading...