Configuring Security Features
959
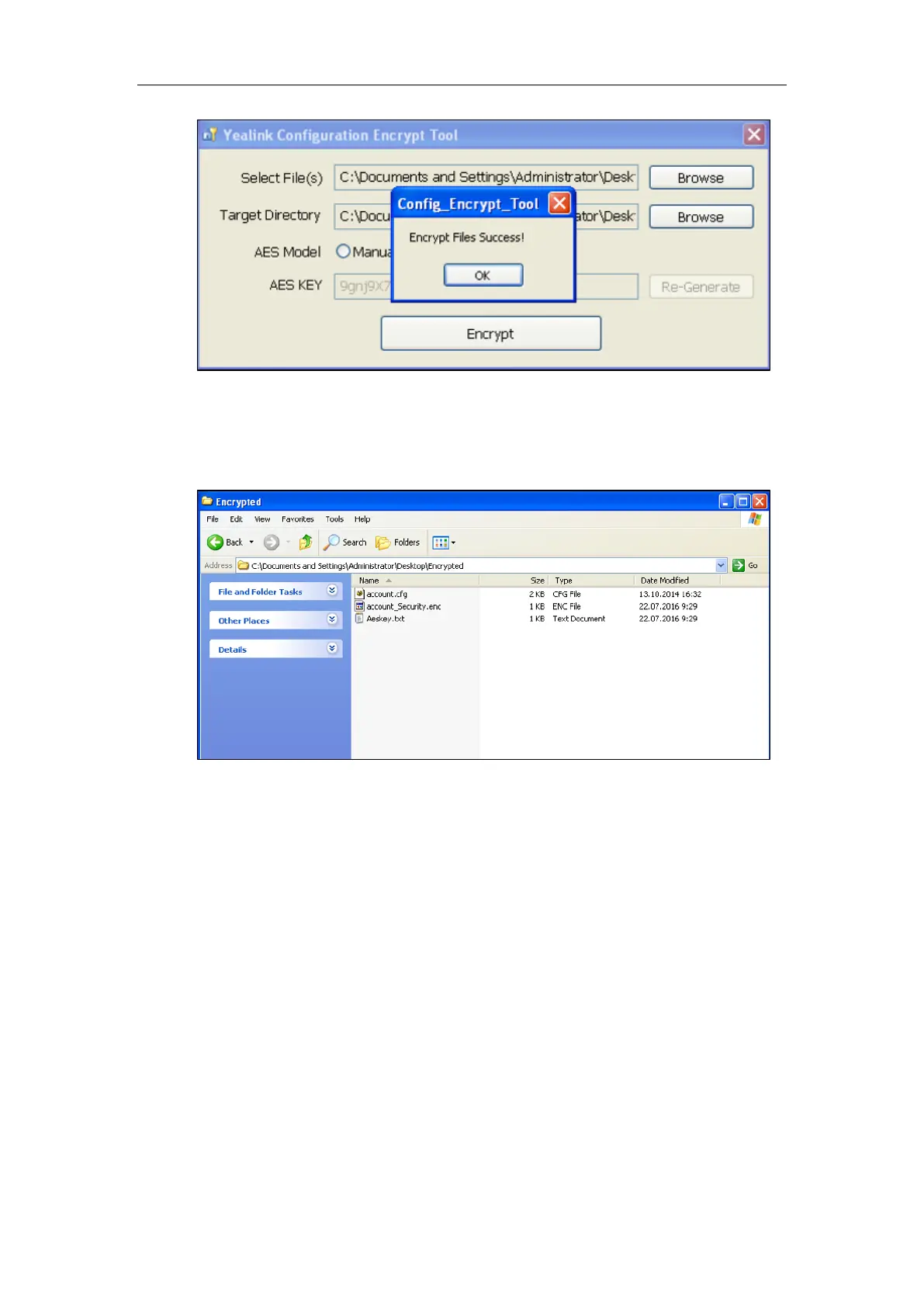
6. Click OK.
The target directory will be automatically opened. You can find the encrypted CFG file(s),
encrypted key file(s) and an Aeskey.txt file storing plaintext AES key(s).
Encrypting and Decrypting Contact Files
Encrypted contact files can be used to protect against unauthorized access and tampering of
private information (e.g., contact number). It is helpful for protecting trade secrets.
You can configure the contact files to be automatically encrypted using 16-character symmetric
keys (configured by the parameter “static.auto_provision.aes_key_16.mac”) when uploading to
the server (by setting the value of the parameter “static.auto_provision.encryption.directory” to
1). The encrypted contact files have the same file names as before. The encrypted contact files
can be downloaded from the server and decrypted using 16-character symmetric keys during
auto provisioning. If the parameter “static.auto_provision.aes_key_16.mac” is left blank, the
value of the parameter “static.auto_provision.aes_key_16.com” will be used.
If the downloaded contact files is encrypted, the IP phone will try to decrypt <MAC>-
contact.xml file using the plaintext AES key. After decryption, the IP phone resolves contact files
and updates contact information onto the IP phone system.
 Loading...
Loading...

















