| Configuring the Security Features | 236
2. Configure and save the following settings:
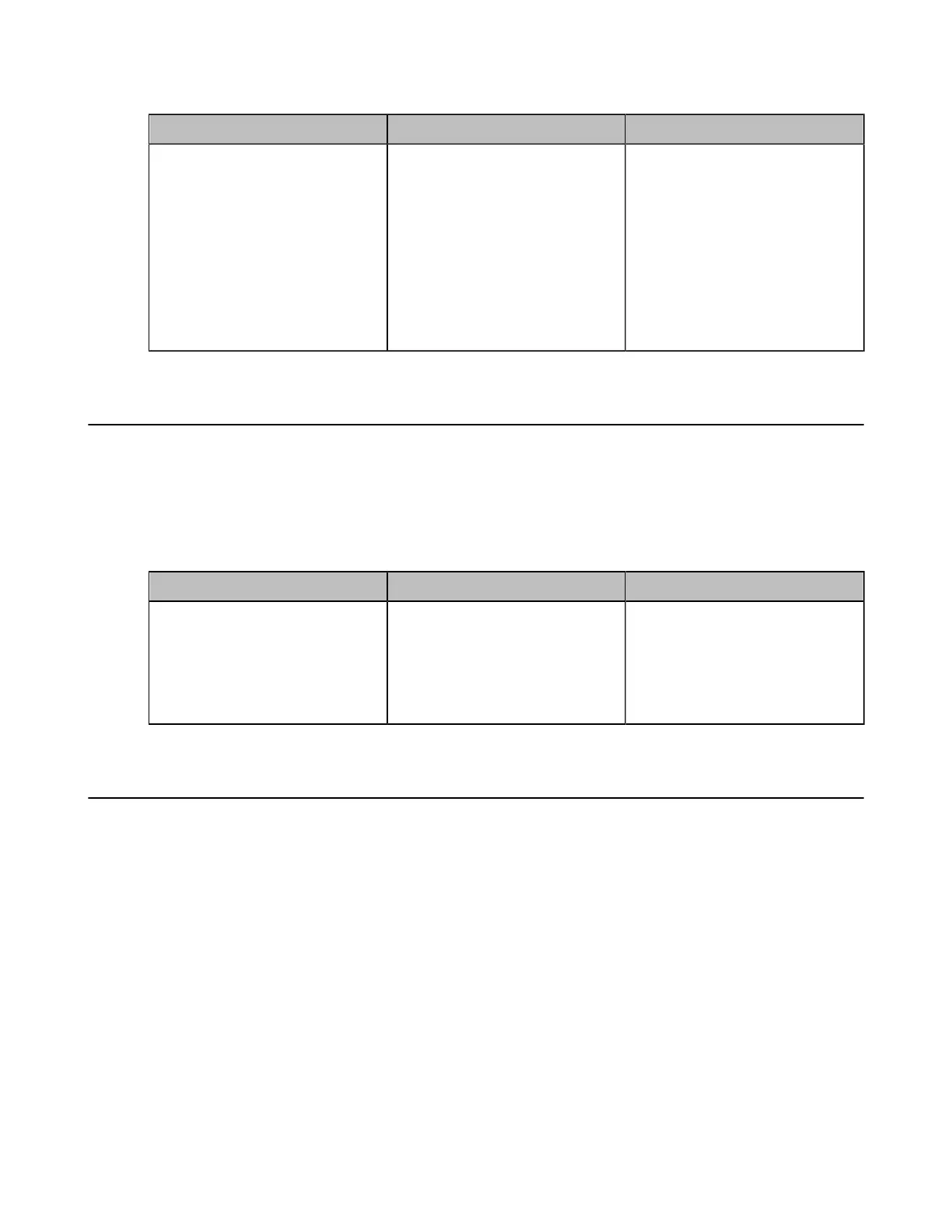
Parameter Description Configuration Method
Accessories Join
Collaboration Confirmation
Enable or disable the
authentication before the
wirelessly connected WPP20/
the touch panel receiving
collaboration data.
Note: the default value is On.
If you change this parameter, the
system will reboot to make the
change take effect.
Web user interface
Configuring the Auto Logout Time
The system will log out of the web user interface automatically after being inactive for a period of time. You
need to re-enter the login credentials to login. You can change the auto logo time.
Procedure
1. On your web user interface, go to Setting > General > Basic > ReLogOffTime(1-1000min).
2. Configure and save the following settings:
Parameter Description Configuration Method
ReLogOffTime (1-1000min)
Specify the inactive time
(minutes) before the system logs
out of the web user interface
automatically.
Default: 5 minute.
Web user interface
Transport Layer Security (TLS)
Transport Layer Protocol (TLS) is a commonly used protocol for ensuring communications privacy and
managing the security of the message transmission. When secured by the TLS protocol, the device can
transmit the data and communicate safely.
The TLS protocol includes two protocol groups: the TLS handshake protocol and the TLS record protocol.
The TLS handshake protocol allows the server and the client to authenticate with each other before
negotiating about the data, the encryption algorithms and the encrypted keys. The TLS Record Protocol
completes the actual data transmission and ensures the data integrity and confidentiality. The TLS protocol
uses an asymmetric encryption algorithm to exchange keys, a symmetric encryption algorithm to ensure
data confidentiality, and the MAC algorithms to ensure data integrity.
• Supported Cipher Suites
• TLS Transport Protocol
• Managing the Trusted Certificates List
• Managing the Server Certificates
• Secure Real-Time Transport Protocol (SRTP)
• H.235 Encryption
• Defending against Attacks

 Loading...
Loading...