1-37
Cisco ASA Series CLI Configuration Guide
Appendix 1 Configuring an External Server for Authorization and Authentication
Configuring an External RADIUS Server
ASA IETF RADIUS Authorization Attributes
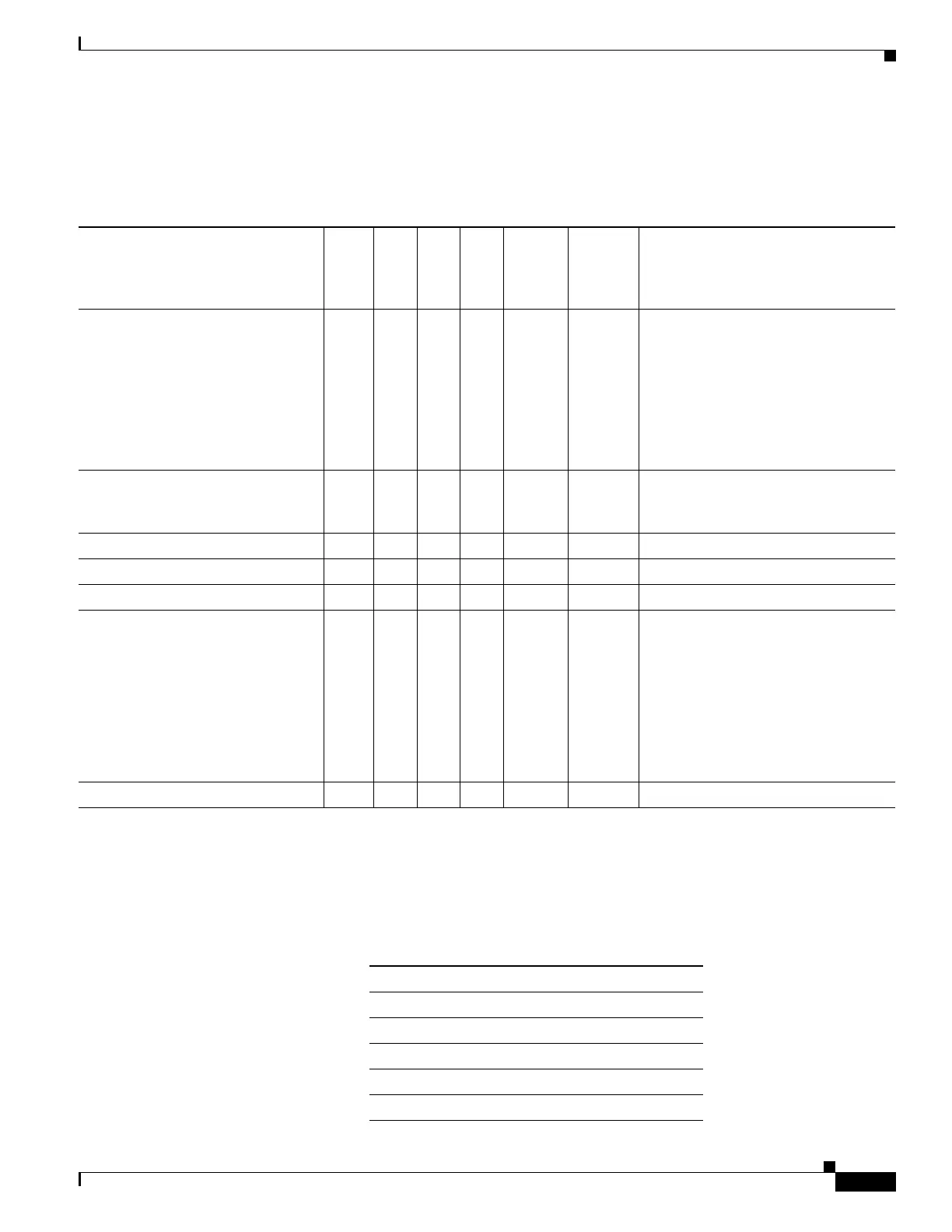
Table 1-8 lists the supported IETF RADIUS attributes.
RADIUS Accounting Disconnect Reason Codes
These codes are returned if the ASA encounters a disconnect when sending packets:
Table 1-8 ASA Supported IETF RADIUS Attributes and Values
Attribute Name
VPN
3000 ASA PIX
Attr.
No.
Syntax/
Type
Single
or
Multi-
Valued Description or Value
IETF-Radius-Class Y Y Y 25 Single For Versions 8.2.x and later, we
recommend that you use the
Group-Policy attribute (VSA 3076,
#25) as described in Table 1-7:
• group policy name
• OU=group policy name
• OU=group policy name
IETF-Radius-Filter-Id Y Y Y 11 String Single Access list name that is defined on the
ASA, which applies only to full
tunnel IPsec and SSL VPN clients
IETF-Radius-Framed-IP-Address Y Y Y n/a String Single An IP address
IETF-Radius-Framed-IP-Netmask Y Y Y n/a String Single An IP address mask
IETF-Radius-Idle-Timeout Y Y Y 28 Integer Single Seconds
IETF-Radius-Service-Type Y Y Y 6 Integer Single Seconds. Possible Service Type
values:
.Administrative—User is allowed
access to configure prompt.
.NAS-Prompt—User is allowed
access to exec prompt.
.remote-access—User is allowed
network access
IETF-Radius-Session-Timeout Y Y Y 27 Integer Single Seconds
Table 1-9
Disconnect Reason Code
ACCT_DISC_USER_REQ = 1
ACCT_DISC_LOST_CARRIER = 2
ACCT_DISC_LOST_SERVICE = 3
ACCT_DISC_IDLE_TIMEOUT = 4
ACCT_DISC_SESS_TIMEOUT = 5
 Loading...
Loading...