1-28
Cisco ASA Series CLI Configuration Guide
Chapter 1 Configuring Network Object NAT
Feature History for Network Object NAT
Feature History for Network Object NAT
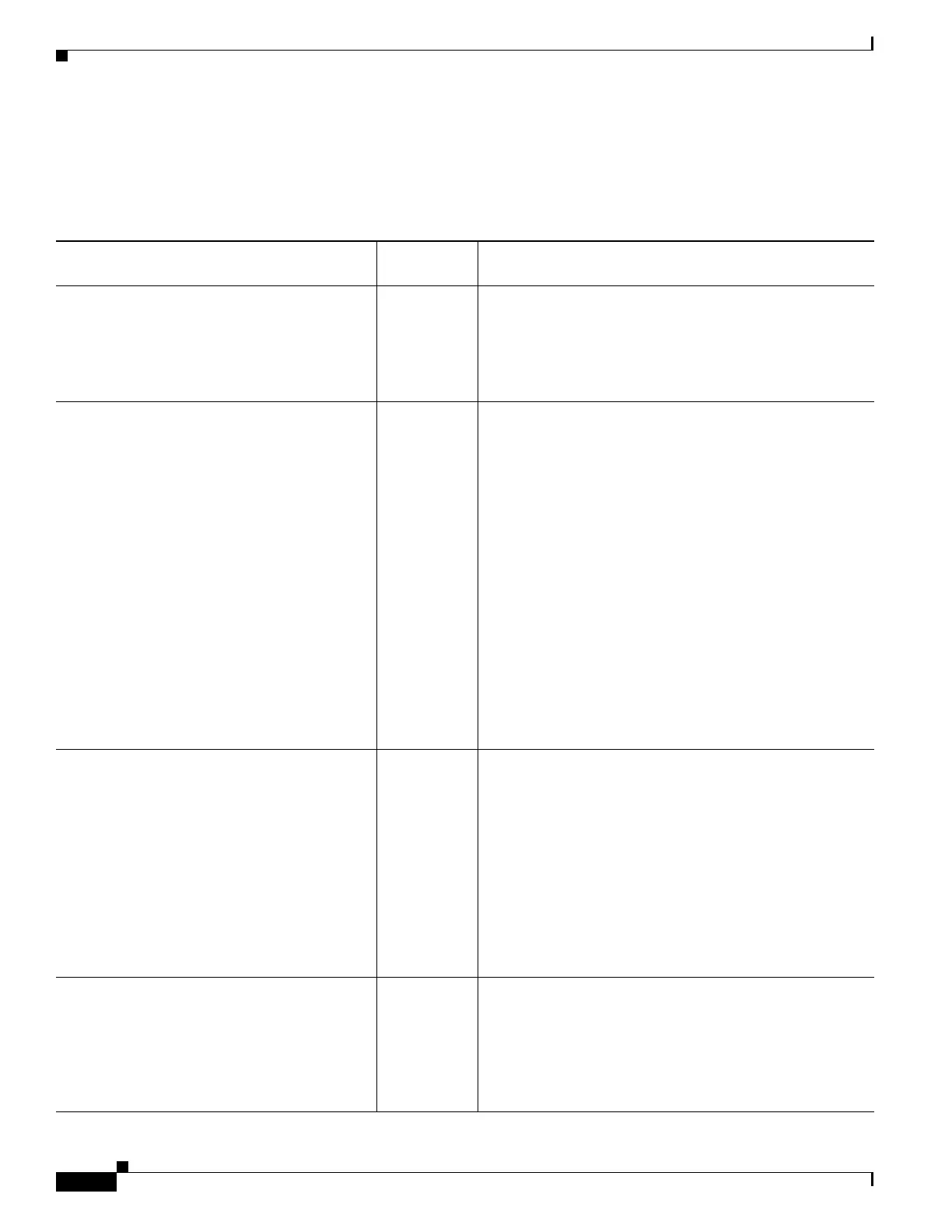
Table 1-1 lists each feature change and the platform release in which it was implemented.
Table 1-1 Feature History for Network Object NAT
Feature Name
Platform
Releases Feature Information
Network Object NAT 8.3(1) Configures NAT for a network object IP address(es).
We introduced or modified the following commands: nat
(object network configuration mode), show nat, show
xlate, show nat pool.
Identity NAT configurable proxy ARP and route
lookup
8.4(2)/8.5(1) In earlier releases for identity NAT, proxy ARP was
disabled, and a route lookup was always used to determine
the egress interface. You could not configure these settings.
In 8.4(2) and later, the default behavior for identity NAT
was changed to match the behavior of other static NAT
configurations: proxy ARP is enabled, and the NAT
configuration determines the egress interface (if specified)
by default. You can leave these settings as is, or you can
enable or disable them discretely. Note that you can now
also disable proxy ARP for regular static NAT.
When upgrading to 8.4(2) from 8.3(1), 8.3(2), and 8.4(1),
all identity NAT configurations will now include the
no-proxy-arp and route-lookup keywords, to maintain
existing functionality.
We modified the following command: nat static
[no-proxy-arp] [route-lookup].
PAT pool and round robin address assignment 8.4(2)/8.5(1) You can now specify a pool of PAT addresses instead of a
single address. You can also optionally enable round-robin
assignment of PAT addresses instead of first using all ports
on a PAT address before using the next address in the pool.
These features help prevent a large number of connections
from a single PAT address from appearing to be part of a
DoS attack and makes configuration of large numbers of
PAT addresses easy.
We modifed the following command: nat dynamic
[pat-pool mapped_object [round-robin]].
Round robin PAT pool allocation uses the same
IP address for existing hosts
8.4(3) When using a PAT pool with round robin allocation, if a host
has an existing connection, then subsequent connections
from that host will use the same PAT IP address if ports are
available.
We did not modify any commands.
This feature is not available in 8.5(1) or 8.6(1).
 Loading...
Loading...