4 CYBER-SECURITY IMPLEMENTATION
The General Electric IEDs have always been and will continue to be equipped with state-of-the-art security
measures. Due to the ev
er-evolving communication technology and new threats to security, this requirement is
not static. Hardware and software security measures are continuously being developed and implemented to
mitigate the associated threats and risks.
This section describes the current implementation of cyber-security. This is valid for the release of platform
software to which this manual pertains. This current cyber-security implementation is known as Cyber-security
Phase 1.
At the IED level, these cyber-security measures have been implemented:
● NERC-compliant default display
● Four-level access
● Enhanced password security
● Password recovery procedure
● Disabling of unused physical and logical ports
● Inactivity timer
● Security events management
External to the IEDs, the following cyber-security measures have been implemented:
● Antivirus
● Security patch management
4.1 NERC-COMPLIANT DISPLAY
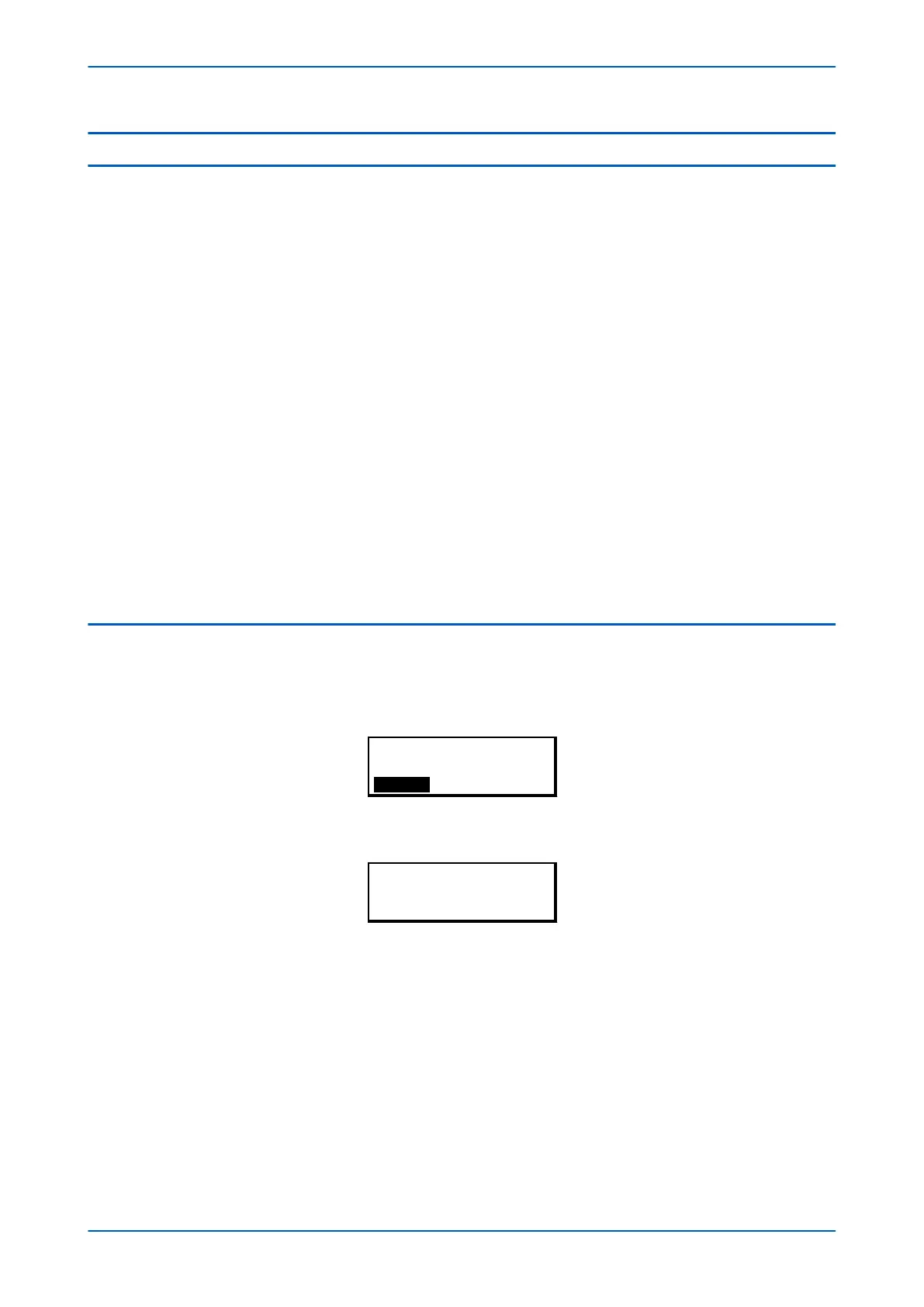
For the device to be NERC-compliant, it must provide the option for a NERC-compliant default display. The default
display that is implemented in our cyber-security concept contains a w
arning that the IED can be accessed by
authorised users. You can change this if required with the User Banner setting in the SECURITY CONFIG column.
ACCESS ONLY FOR
AUTHORISED USERS
HOTKEY
If you try to change the default display from the NERC-compliant one, a further warning is displayed:
DISPLAY NOT NERC
COMPLIANT OK?
The default display navigation map shows how NERC-compliance is achieved with the product's default display
concept.
P14x Chapter 19 - Cyber
-Security
P14xEd1-TM-EN-1 463

 Loading...
Loading...