User's Manual 176 Document #: LTRT-27045
Mediant 1000B Gateway & E-SBC
Where SI is the SIP Interface and NI is the network interface.
The device also sends IDS notifications and alarms in Syslog messages to a Syslog
server. This occurs only if you have configured Syslog (see ''Enabling Syslog'' on page
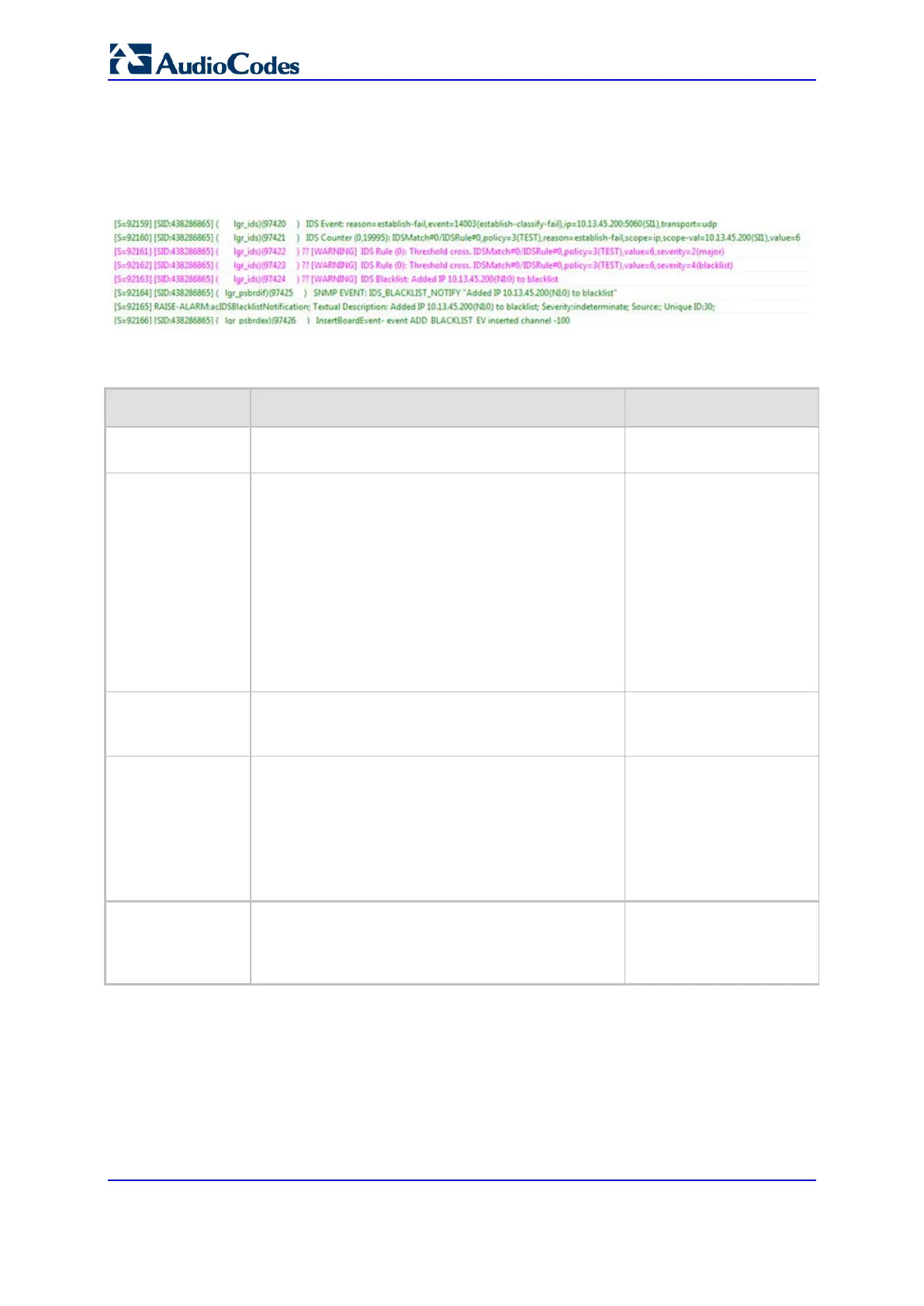
892). An example of a Syslog message with IDS alarms and notifications is shown below:
Figure 13-9: Syslog Message Example with IDS Alarms and Notifications
The table below lists the Syslog text messages per malicious event:
Table 13-6: Types of Malicious Events and Syslog Text String
Reason Description Syslog String
Connection
Abuse
TLS authentication failure abuse-tls-auth-fail
Malformed
Messages
Message exceeds a user-defined maximum
message length (50K)
Any SIP parser error
Message policy match
Basic headers not present
Content length header not present (for TCP)
Header overflow
malformed-invalid-
msg-len
malformed-parse-error
malformed-message-
policy
malformed-miss-
header
malformed-miss-
content-len
malformed-header-
overflow
Authentication
Failure
Local authentication ("Bad digest" errors)
Remote authentication (SIP 401/407 is sent if
original message includes authentication)
auth-establish-fail
auth-reject-response
Dialog
Establishment
Failure
Classification failure
Routing failure
Other local rejects (prior to SIP 180 response)
Remote rejects (prior to SIP 180 response)
Malicious signature pattern detected
establish-classify-fail
establish-route-fail
establish-local-reject
establish-remote-
reject
establish-malicious-
signature-db-reject
Abnormal Flow
Requests and responses without a matching
transaction user (except ACK requests)
Requests and responses without a matching
transaction (except ACK requests)
flow-no-match-tu
flow-no-match-
transaction

 Loading...
Loading...



















