Dell SonicWALL Secure Mobile Access 8.5
Administration Guide
460
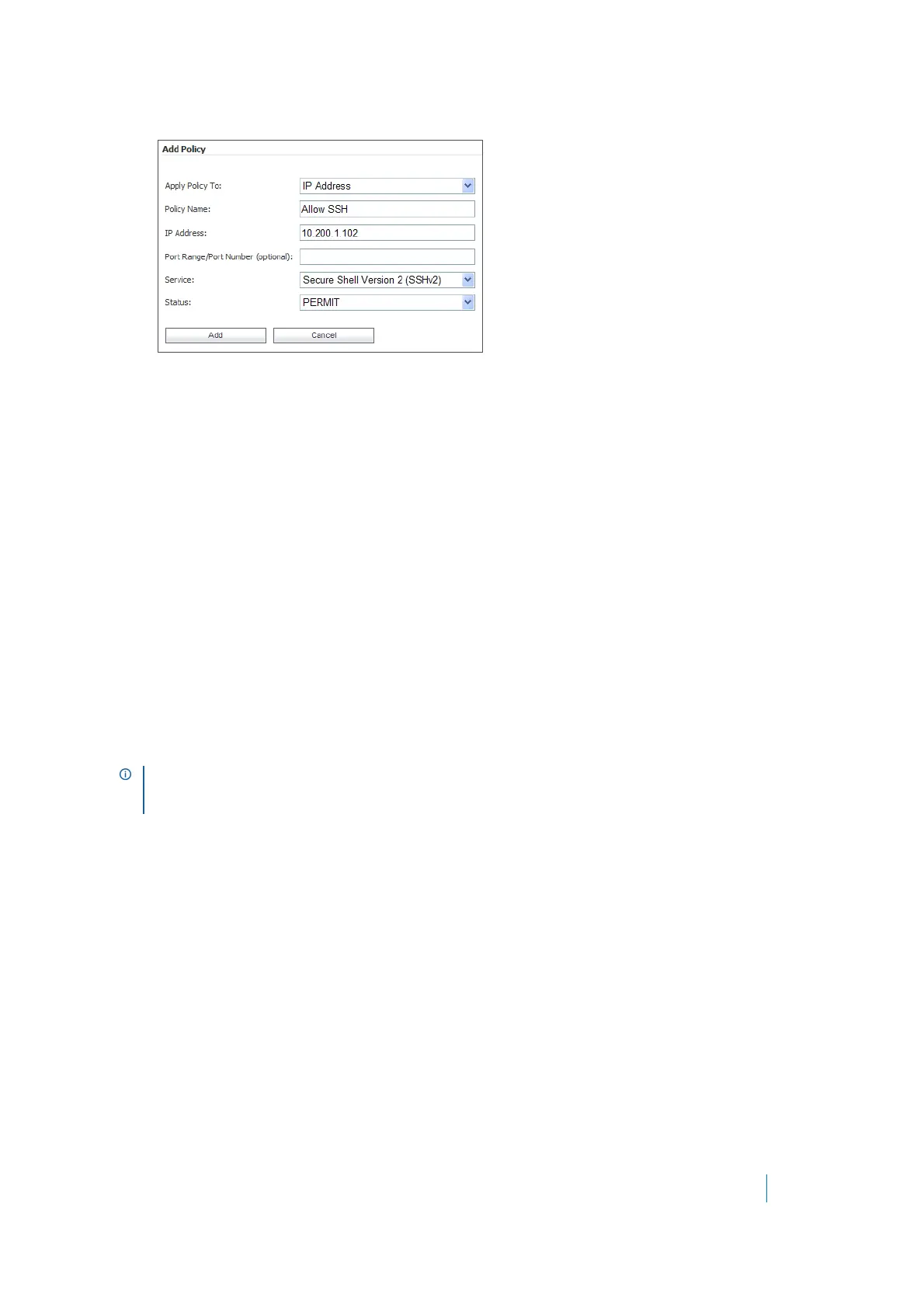
4In the Add Policy window, select IP Address in the Apply Policy To drop-down list.
5In the Policy Name field, enter the descriptive name, Allow SSH.
6In the IP Address field, enter the IP address of the target server, 10.202.1.102.
7In the Services drop-down list, select Secure Shell Version 2 (SSHv2).
8In the Status drop-down list, select PERMIT, and then click Add.
9In the Edit Group Settings window, click OK.
Adding the OWA PERMIT Policies
In this section, we will add two OWA PERMIT policies for both Mega_Group and IT_Group to access the OWA
service using Secure Web (HTTPS).
This procedure creates a policy for the Secure Mobile Access Local Group, Mega_Group, and results in OWA
access for members of the Active Directory group, Mega Group.
To access the Exchange server, adding a PERMIT policy to the 10.200.1.10/exchange URL Object itself is not
enough. Another URL Object policy is needed that permits access to 10.200.1.10/exchweb, because some
OWA Web contents are located in the exchweb directory.
Repeat this procedure for IT_Group to provide OWA access for members of the Active Directory group, IT
Group.
The OWA policies are applied to Exchange server URL Objects rather than server IP addresses since OWA is a
Web service.
1In the Users > Local Groups page, click Configure in the Mega_Group row. We will create two PERMIT
policies for Mega_Group to allow access to the OWA Exchange server.
2In the Edit Group Settings window, click the Policies tab, and then click Add Policy.
NOTE: In this configuration, members of IT_Group and Mega_Group are denied access to the
https://owa-server/public folder, because these groups have access only to the /exchange and /exchweb
subfolders.

 Loading...
Loading...