Web-based Configuration Guide 1 Network Settings
88
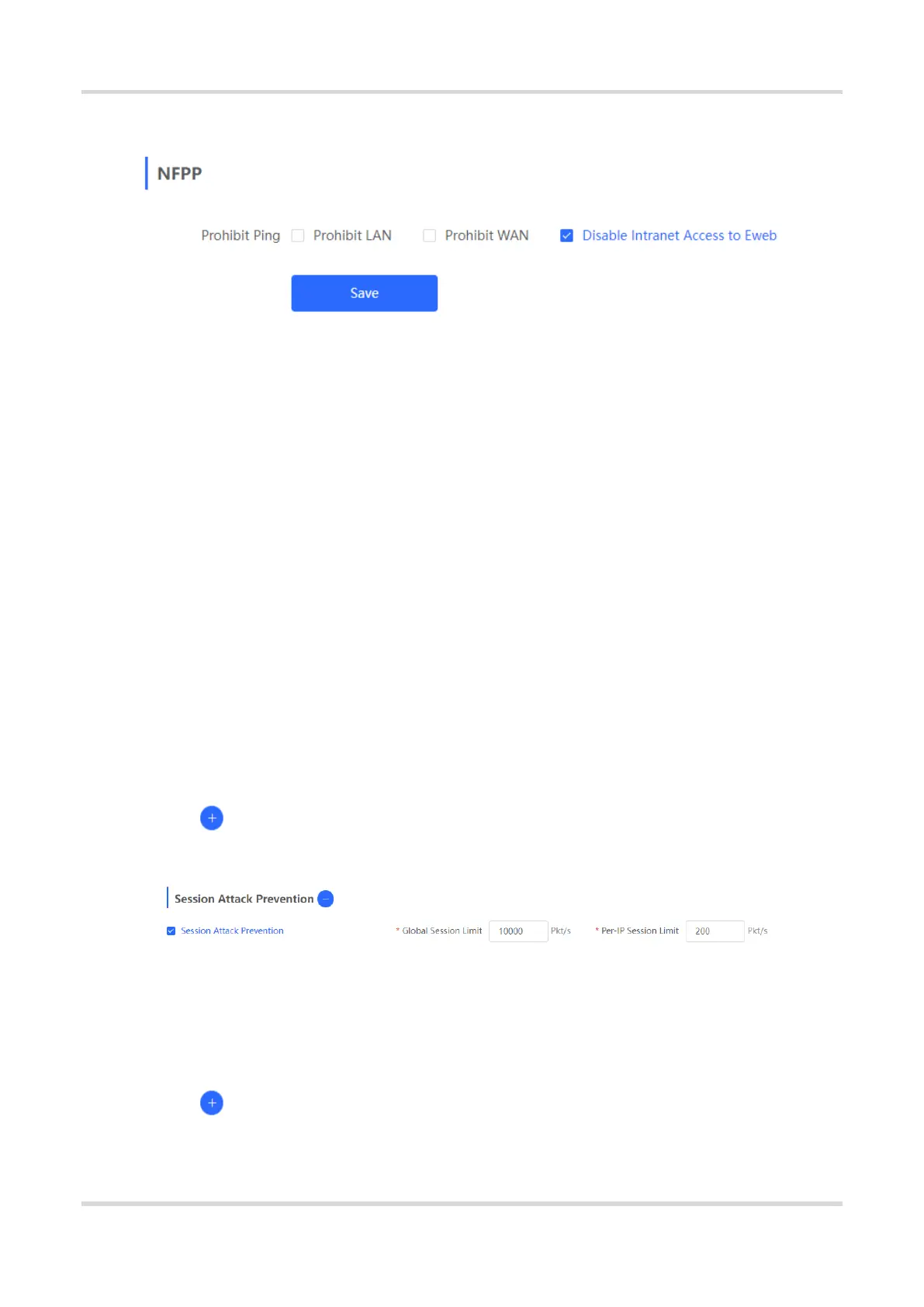
You can disable intranet access to Eweb only after you configure a management IP address.
3.20.2 Configuring Session Attack Prevention
1. Overview
Session Attack Prevention
In a session attack, an attacker sends heavy traffic to the device. In this case, the device has to consume
many resources when creating connections. To reduce the impact of the attack, you can limit the rate of
creating sessions.
Flood Attack Prevention
In a flood attack, an attacker sends tremendous abnormal packets to a device. As a result, the device uses
a large amount of resources to handle the packets. This causes the device performance to deteriorate or the
system to break down. the
Suspicious Packet Attack Prevention
In a suspicious packet attack, an attacker sends tremendous error packets to the device. When the host or
server handles the error packets, its system will crash.
2. Configuring Session Attack Prevention
Choose Local Device > Security > Local Protection > Attack Defense.
(1) Click next to Session Attack Prevention.
(2) Enable Session Attack Prevention.
(3) Configure the session creation rate limit, including global and per-IP values.
(4) Click Save.
3. Configuring Flood Attack Prevention
Choose Local Device > Security > Local Protection > Attack Defense.
(1) Click next to Flood Attack Prevention.
(2) Select required attack prevention types and enable this feature.

 Loading...
Loading...








