109
In this example, select the local CRL publishing mode of HTTP and set the HTTP URL to
http://4.4.4.133:447/myca.crl.
After the configuration, make sure the system clock of the router is synchronous to that of the
CA, so that the router can request certificates and retrieve CRLs properly.
Configuring the router
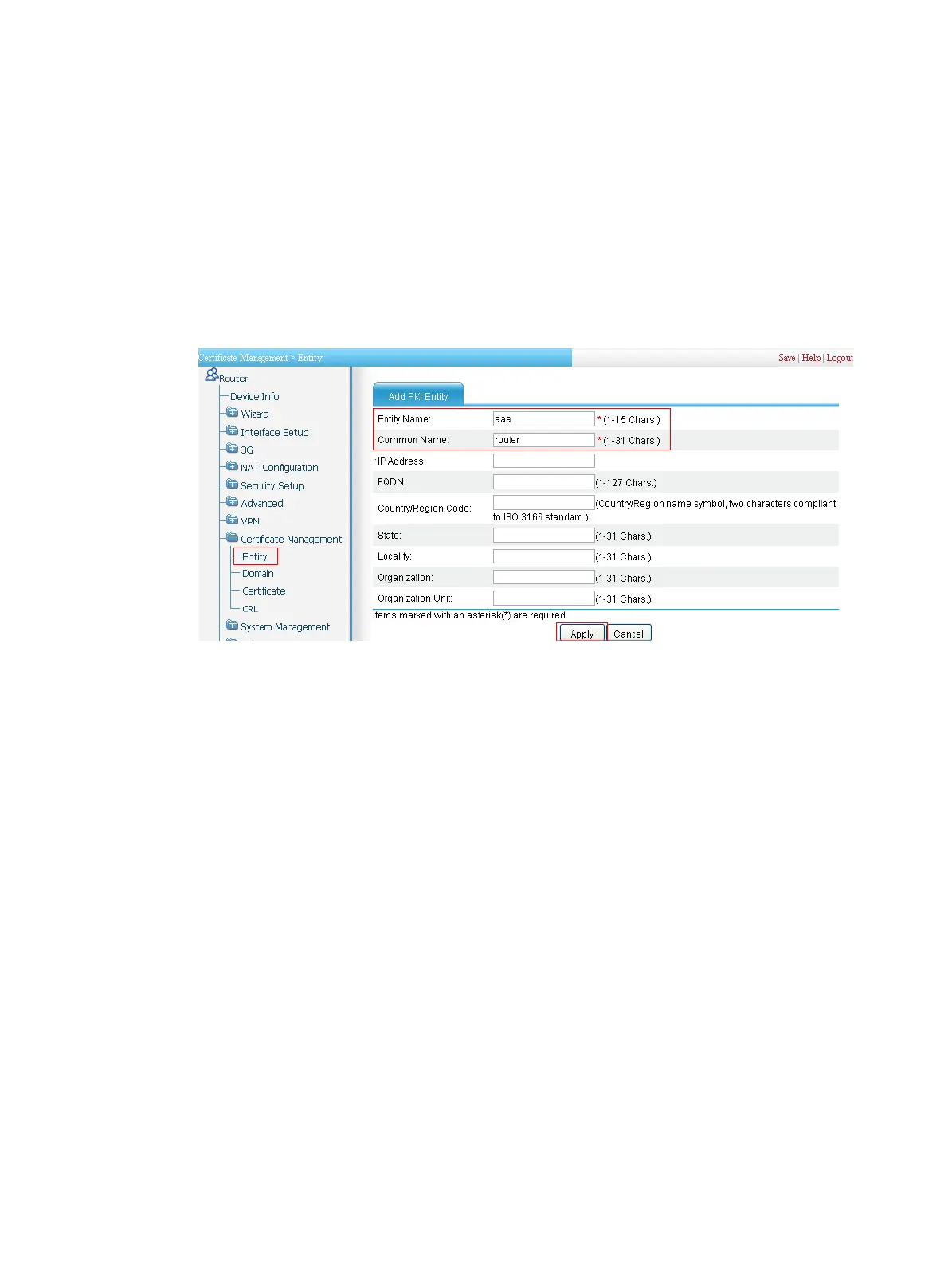
1. Create a PKI entity:
a. From the navigation tree, select Certificate Management > Entity.
b. Click Add.
c. Enter aaa as the PKI entity name, enter router as the common name, and click Apply.
Figure 492 Creating a PKI entity
2. Create a PKI domain:
a. From the navigation tree, select Certificate Management > Domain.
b. Click Add.
The page in Figure 493 a
p
pears.
c. In the upper area of the page, enter torsa as the PKI domain name, enter myca as the CA
identifier, select aaa as the local entity, select CA as the authority for certificate request,
enter http://4.4.4.133:446/c95e970f632d27be5e8cbf80e971d9c4a9a93337 as the URL
for certificate request (the URL must be in the format of http://host:port/Issuing Jurisdiction
ID, where Issuing Jurisdiction ID is the hexadecimal string generated on the CA), and select
Manual as the certificate request mode.
d. Click the expansion button before Advanced Configuration to display the advanced
configuration items.
e. In the advanced configuration area, click the Enable CRL Checking box, and enter
http://4.4.4.133:447/myca.crl as the CRL URL.
f. Click Apply.
The system displays "Fingerprint of the root certificate not specified. No root certificate
validation will occur. Continue?"
g. Click OK to confirm.

 Loading...
Loading...




