Chapter 3 Featured Functions
3.3 Network Redundancy
In some network environments, users need to set up redundant loops in the network to provide a
backup path for disconnection or network device breakdown. But if there are many network devices
in the network, then each host needs to spend more time and cross many network devices to
associate with each other. And sometimes the disconnection happens in a busy network, so the
network must recover in a short time. Setting up redundancy on your network helps protect critical
links against failure, protects against network loops, and keeps network downtime at a minimum.
For example, if the Delta switch is used as a key communications component of a production line,
several minutes of downtime may cause a big loss in production and revenue.
IMPORTANT:
Make sure that you save the configuration in the Save
Configuration page after you have applied the configuration
changes. (Save ConfigSave Configuration) If you don’t
save the configuration, then the configuration will be cleared
after the switch is rebooted.
3.3.1 STP
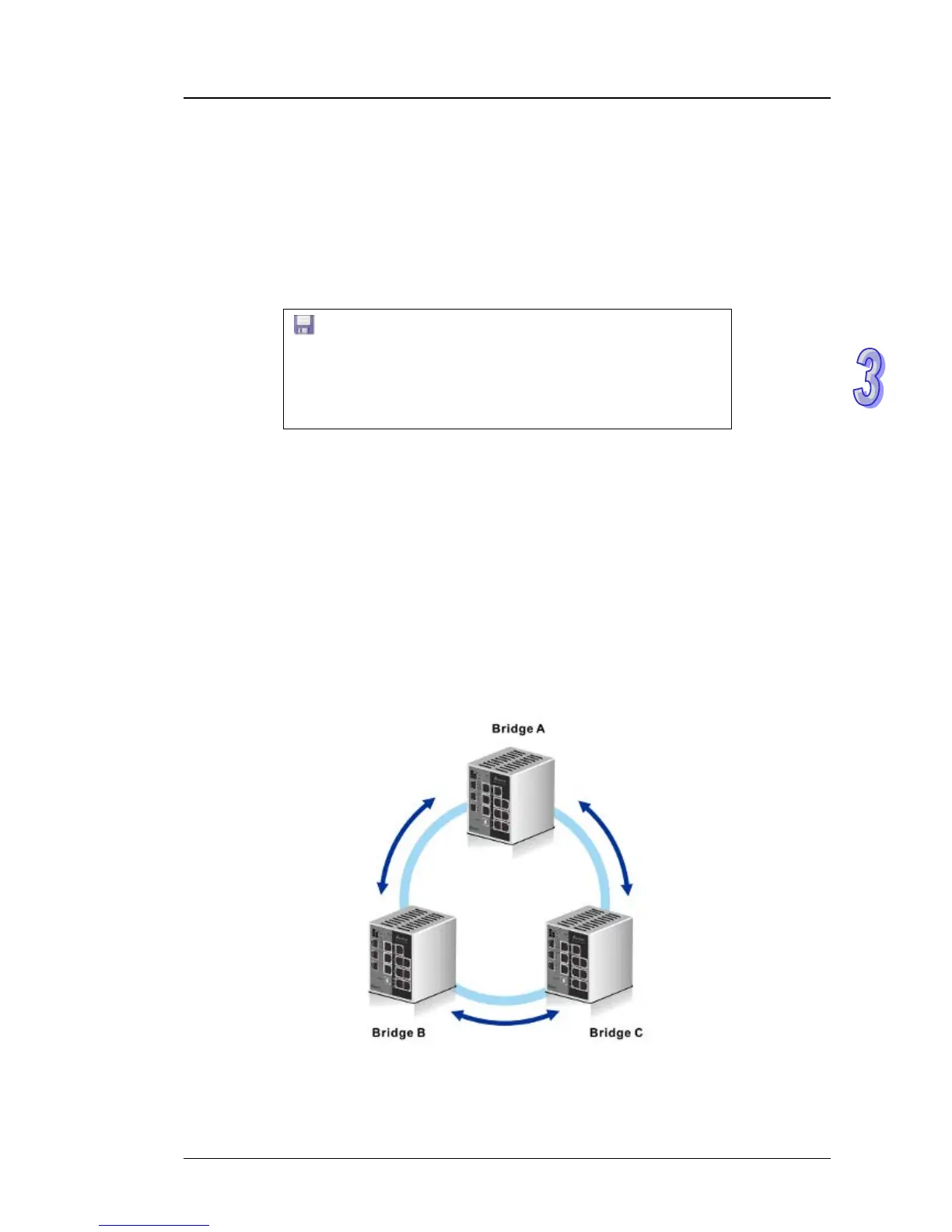
Spanning Tree Protocol (STP) provides a tree topology to help reduce link failure in a network, find
one path between end devices and protect loops in the network. Bridge Protocol Data Unit (BPDU)
includes the calculation of information and it is used to negotiate between switches and establish
STP. STP is a bridge based system and it defines 5 kinds of port statuses: blocking, listening,
learning, forwarding and disabling. If the status of blocking changes to forwarding, STP needs to
spend more than 30 seconds.
Rapid Spanning Tree Protocol (RSTP) was defined by IEEE in 2001. RSTP provides faster tree
convergence after a topology changes. Sometimes it only needs to spend a few hundred
milliseconds. And RSTP can backward compatible with standard STP.
Delta switch supports different protocols to support communication redundancy. When configuring a
redundant ring, all switches on the same ring must be configured to use the same redundant
protocol.
STP/RSTP can let you establish a redundant ring and protect the loop in a network.
3-37
 Loading...
Loading...