Chapter 3 Featured Functions
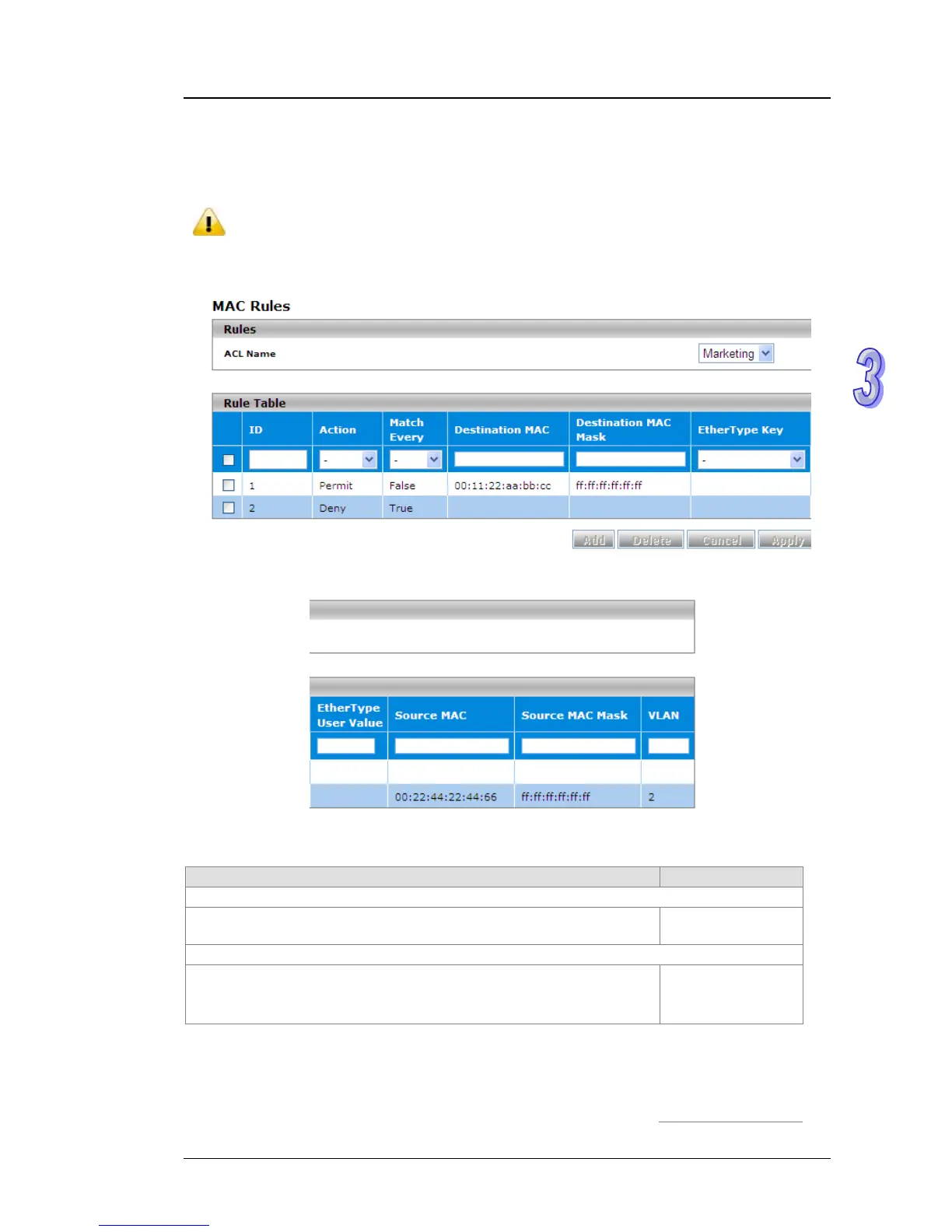
3.10.2 MAC Rules
After creating an ACL name, you can configure the action, match, destination MAC, source MAC
and VLAN in this page. It can determine whether the packet is forwarded normally or discarded.
Note:
You need to create an implicit deny all rule at the end of an ACL rule table to make
sure that a packet is dropped if an ACL is applied to the packet and none of the
explicit rules match.
Rule Table
Description Factory Default
ID
Enter an ID for the rule. Enter a number between 1 and 10. This means
that you can create up to 10 rules for a single MAC ACL name.
None
Action
Specify the action for the rule:
Permit: Packets that meet the ACL criteria are forwarded.
Deny: Packets that meet the ACL criteria are dropped.
None
3-77
 Loading...
Loading...