C
ONFIGURING
THE
S
WITCH
3-88
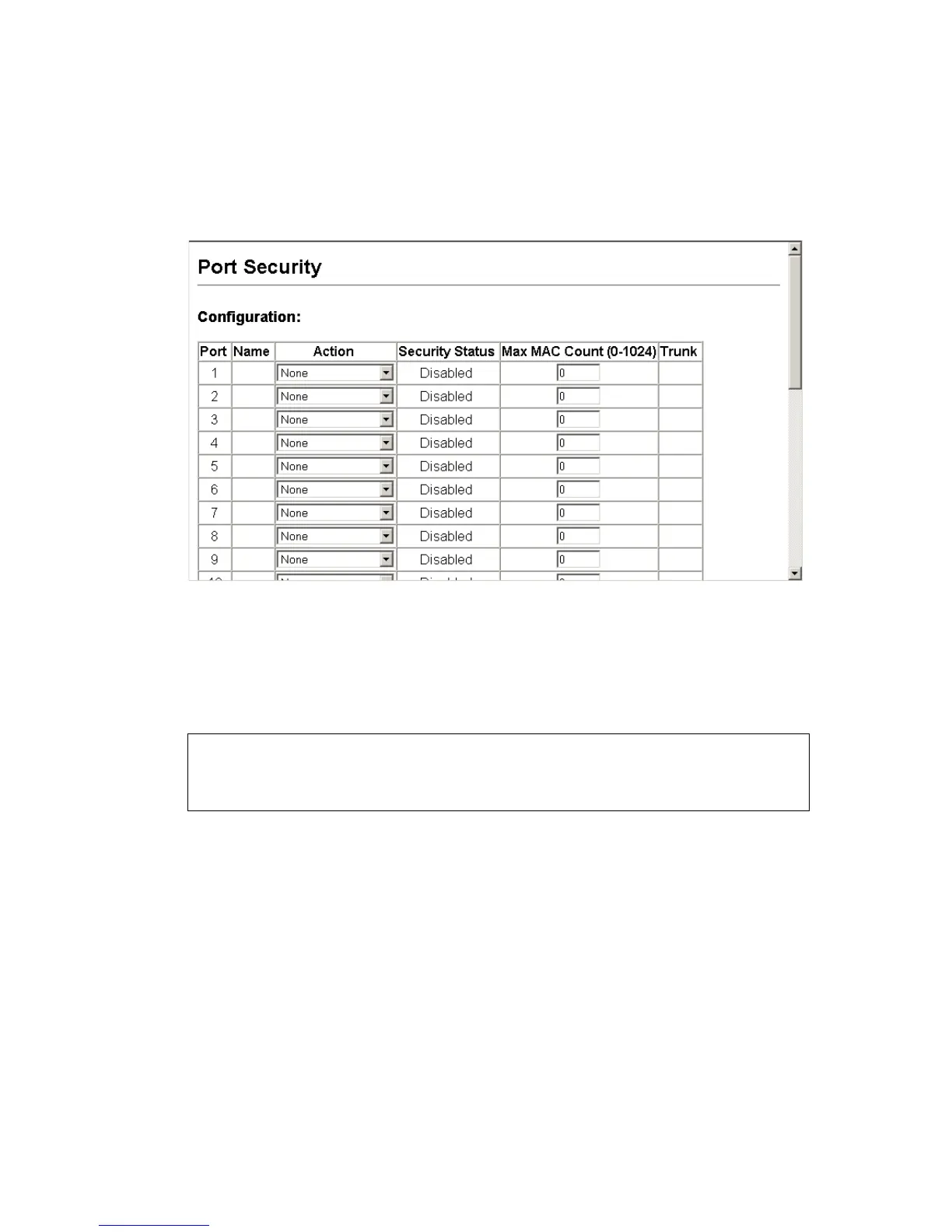
Web – Click Security, Port Security. Set the action to take when an invalid
address is detected on a port, set the maximum number of MAC addresses
allowed on a port, and click Apply.
Figure 3-38. Configuring Port Security
CLI – This example sets the command mode to Port 5, sets the port
security action to send a trap and disable the port, and then enables port
security for the switch.
Configuring 802.1X Port Authentication
Network switches can provide open and easy access to network resources
by simply attaching a client PC. Although this automatic configuration and
access is a desirable feature, it also allows unauthorized personnel to easily
intrude and possibly gain access to sensitive network data.
The IEEE 802.1X (dot1x) standard defines a port-based access control
procedure that prevents unauthorized access to a network by requiring
users to first submit credentials for authentication.
Console(config)#interface ethernet 1/5
Console(config-if)#port security action trap-and-shutdown 4-102
Console(config-if)#port security
Console(config-if)#

 Loading...
Loading...








