C
ONFIGURING
THE
S
WITCH
3-48
• Access Mode – Specifies the access rights for the community string:
- Read-Only – Authorized management stations are only able to
retrieve MIB objects.
- Read/Write – Authorized management stations are able to both
retrieve and modify MIB objects.
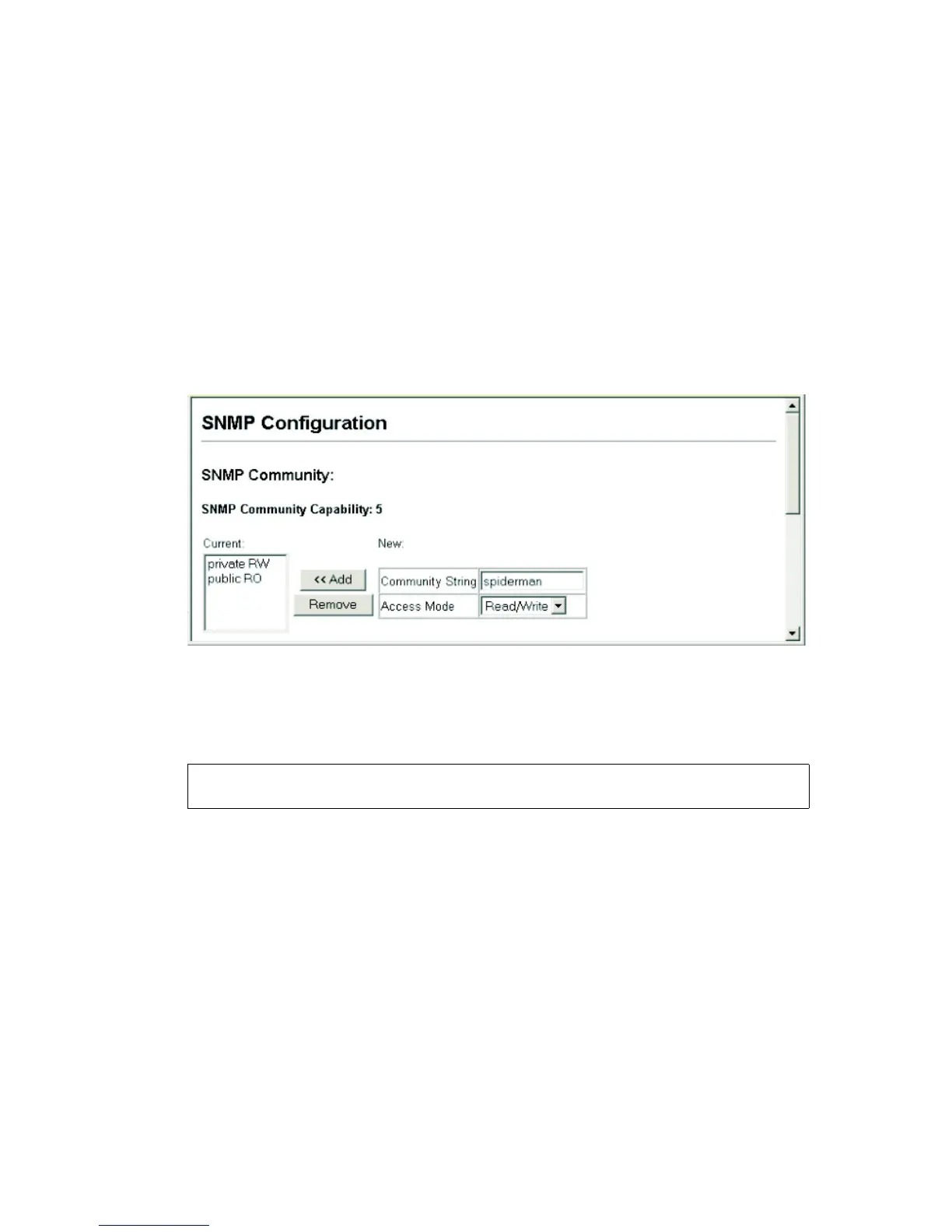
Web – Click SNMP, Configuration. Add new community strings as
required, select the access rights from the Access Mode drop-down list,
then click Add.
Figure 3-24 Configuring SNMP Community Strings
CLI – The following example adds the string “spiderman” with read/write
access.
Console(config)#snmp-server community spiderman rw 4-127
Console(config)#

 Loading...
Loading...






