P
ORT
C
ONFIGURATION
3-133
Command Usage
• Input and output rate limits can be enabled or disabled for individual
interfaces.
Command Attribute
• Port/Trunk – Display the port number.
• Input/Output Rate Limit Status– Enables or disables the rate limit
(Default: Enabled)
• Input/Output Rate Limit Level - Sets the rate limit level.
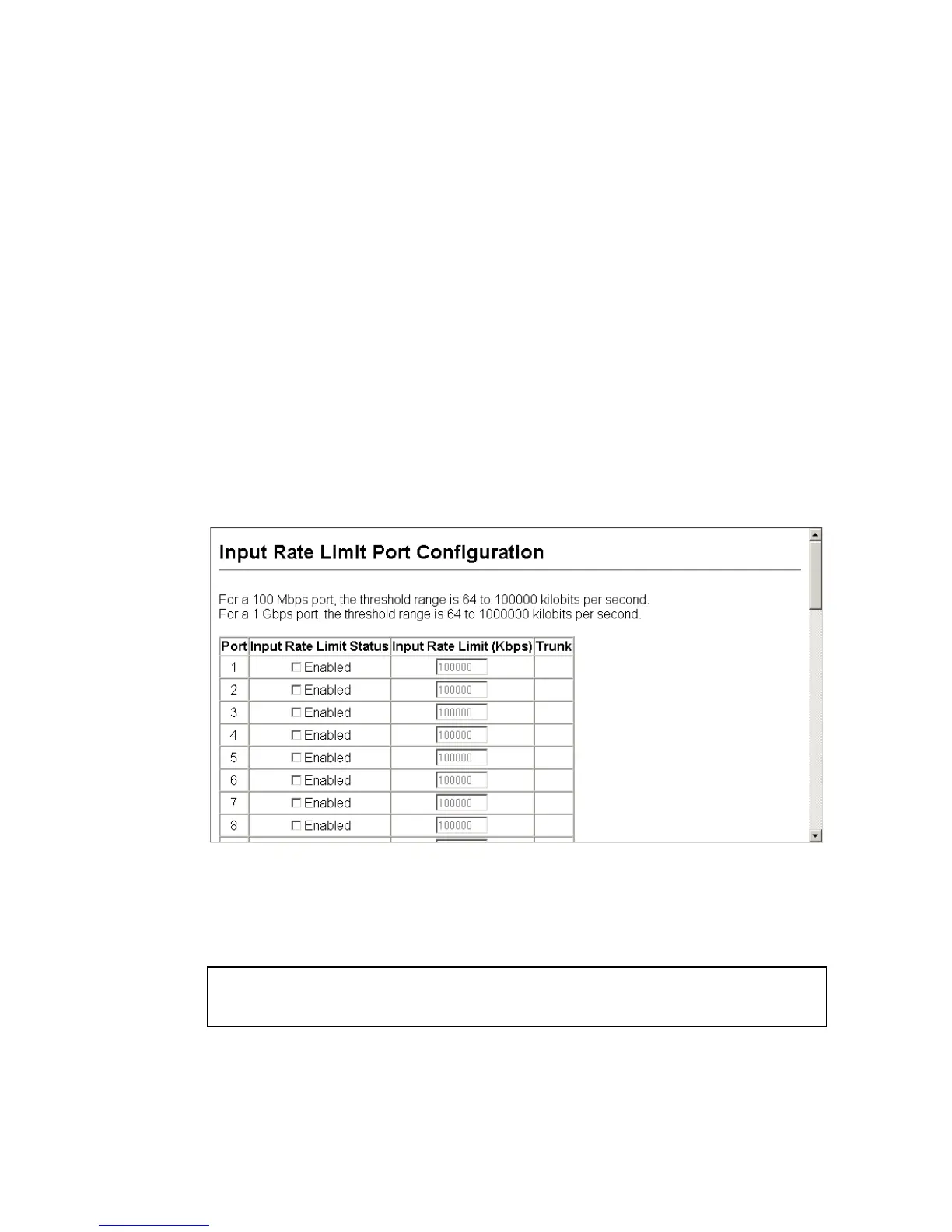
Web - Click Port, Rate Limit, Input/Output Port/Trunk Configuration.
Enable the Rate Limit Status for the required interfaces, set the Rate Limit
Level, and click Apply.
Figure 3-59. Configuring Input Port Rate Limiting
CLI - This example sets the rate limit for input traffic passing through
port 3.
Console(config)#interface ethernet 1/3 4-144
Console(config-if)#rate-limit input 25 4-160
Console(config-if)#

 Loading...
Loading...








