User authentication LDAP
Digi Connect EZ Mini User Guide
546
n Start TLS: Makes a non-secure TCP connection to the LDAP server on port 389, then
sends a request to upgrade the connection to a secure TLS connection. This is the
preferred method for LDAP.
7. If Enable TLS or Start TLS are selected for TLS connection:
n Leave Verify server certificate at the default setting of enabled to verify the server
certificate with a known Certificate Authority.
n Disable Verify server certificate if the server is using a self-signed certificate.
8. (Optional) For Server login, type a distinguished name (DN) that is used to bind to the LDAP
server and search for users, for example cn=user,dc=example,dc=com. Leave this field blank if
the server allows anonymous connections.
9. (Optional) For Server password, type the password used to log into the LDAP server. Leave
this field blank if the server allows anonymous connections.
10. For User search base, type the distinguished name (DN) on the server to search for users. This
can be the root of the directory tree (for example, dc=example,dc=com) or a sub-tree (for
example. ou=People,dc=example,dc=com).
11. For Login attribute, enter the user attribute containing the login of the authenticated user.
For example, in the LDAP user configuration, the login attribute is uid. If this attribute is not
set, the user will be denied access.
12. (Optional) For Group attribute, type the name of the user attribute that contains the list of
Connect EZ authentication groups that the authenticated user has access to. See LDAP user
configuration for further information about the group attribute.
13. For Timeout, type or select the amount of time in seconds to wait for the LDAP server to
respond. Allowed value is between 3 and 60 seconds.
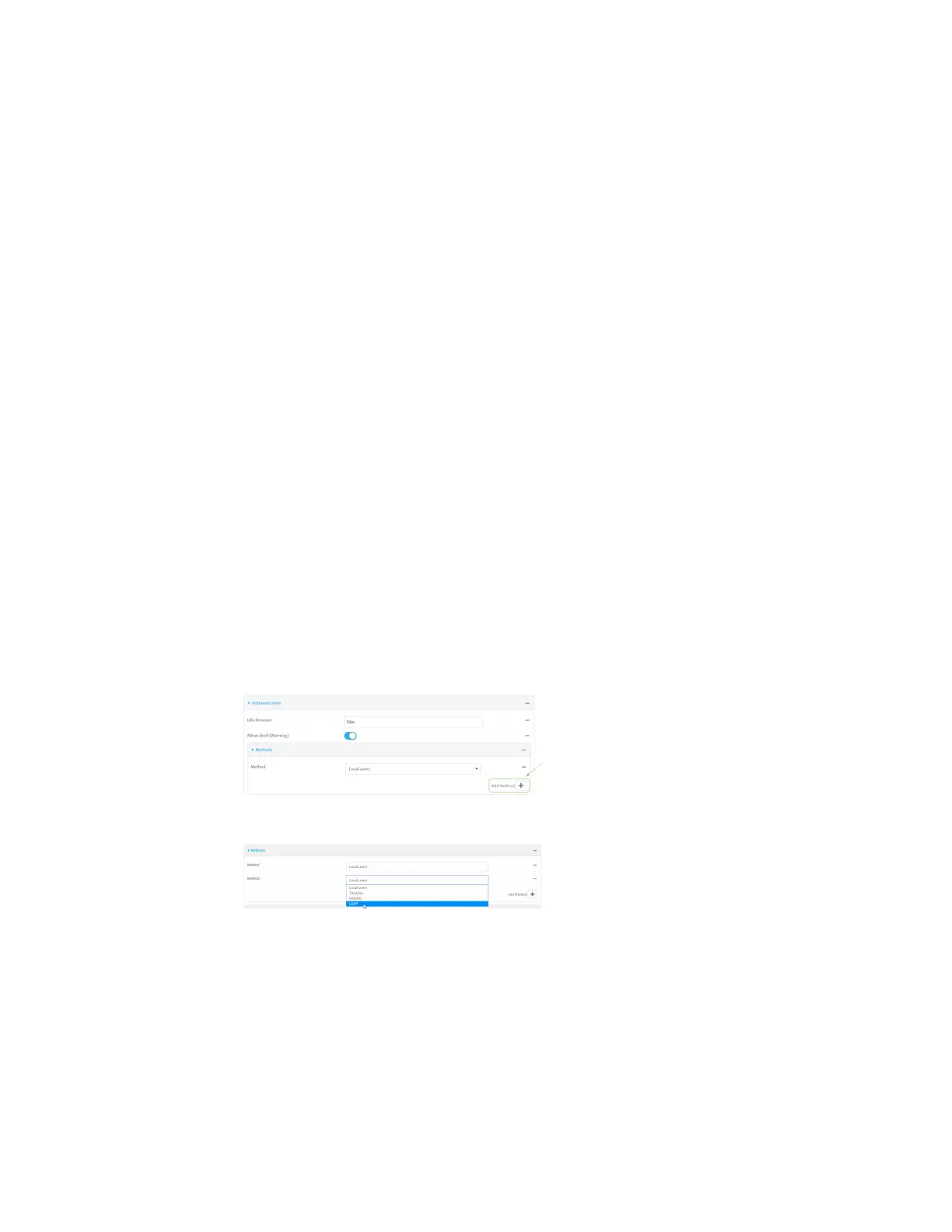
14. Add LDAP to the authentication methods:
a. Click Authentication > Methods.
b. For Add method, click .
c. Select LDAP for the new method from the Method drop-down.
Authentication methods are attempted in the order they are listed until an authentication
response, either pass or fail, is received. If Authoritative is enabled (see above), non-
authoritative methods are not attempted. See Rearrange the position of authentication
methods for information about rearranging the position of the methods in the list.
15. Click Apply to save the configuration and apply the change.
Command line
 Loading...
Loading...











