Configuring SSL/TLS
Configuring the machine to use SSL/TLS enables encrypted communication. Doing so makes it possible
to prevent data from being intercepted during transmission, and its content from being analyzed or
tampered with.
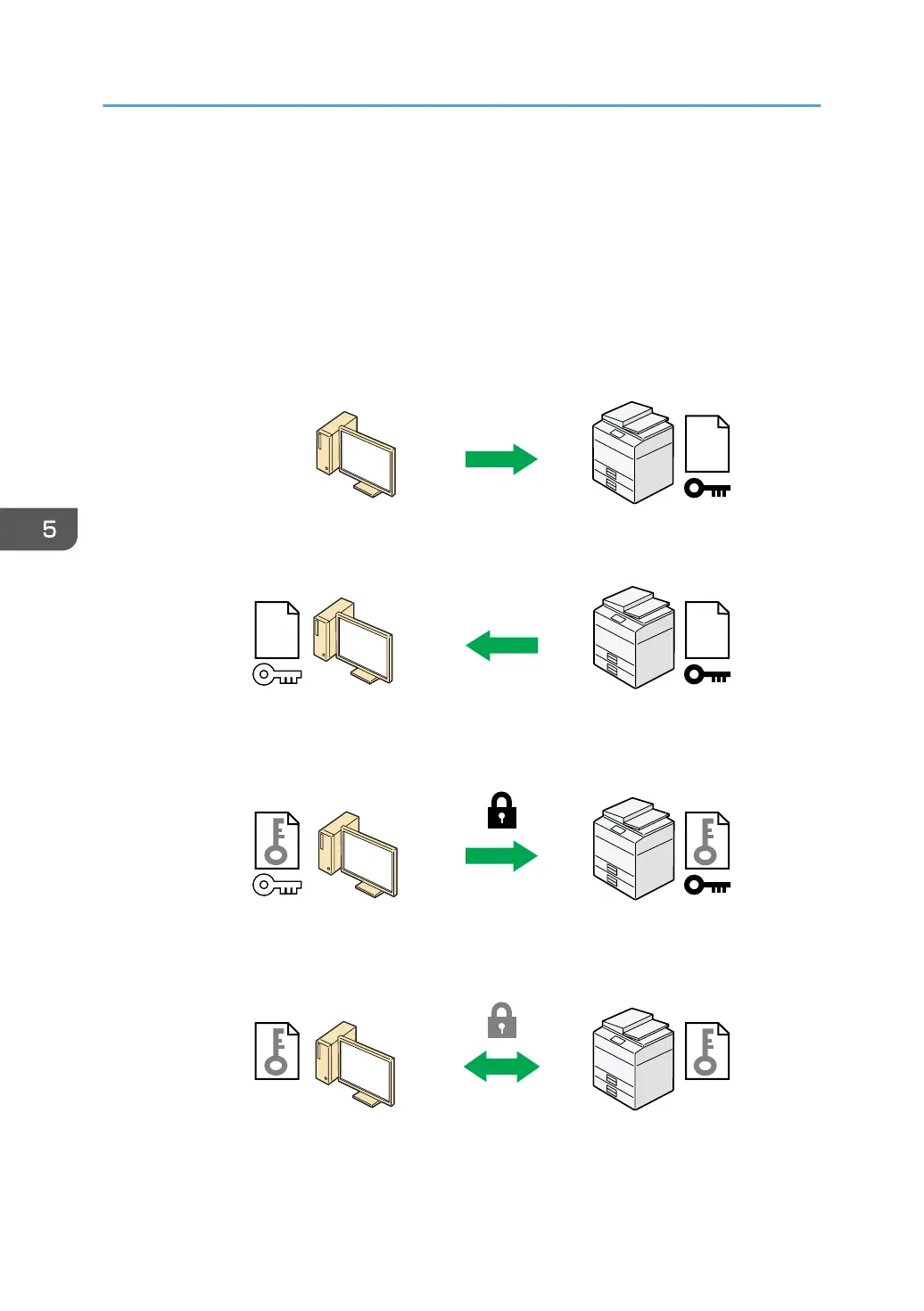
Flow of SSL/TLS encrypted communications
1. To access the machine from a user's computer, request the SSL/TLS device certificate and
public key.
2. The device certificate and public key are sent from the machine to the user's computer.
3. The shared key created with the computer is encrypted using the public key, sent to the
machine, and then decrypted using the private key in the machine.
4. The shared key is used for data encryption and decryption, thus achieving secure
transmission.
Configuration flow when using a self-signed certificate
1. Creating and installing the device certificate
5. Enhanced Network Security
132

 Loading...
Loading...