16-5
Cisco Security Appliance Command Line Configuration Guide
OL-10088-01
Chapter 16 Identifying Traffic with Access Lists
Adding an Extended Access List
If you perform NAT on both interfaces, keep in mind the addresses that are visible to a given interface.
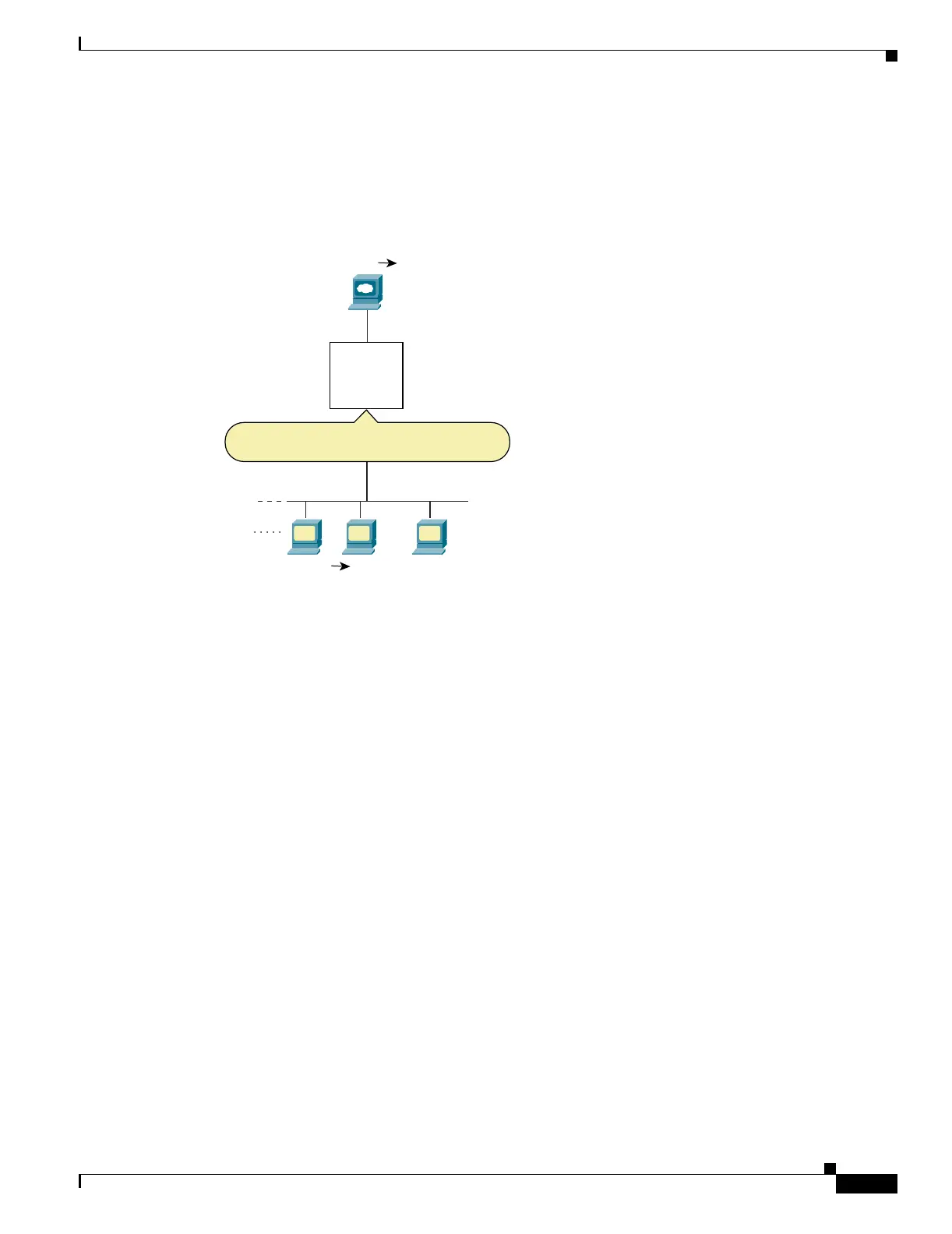
In Figure 16-3, an outside server uses static NAT so that a translated address appears on the inside
network.
Figure 16-3 IP Addresses in Access Lists: NAT used for Source and Destination Addresses
See the following commands for this example:
hostname(config)# access-list INSIDE extended permit ip 10.1.1.0 255.255.255.0 host
10.1.1.56
hostname(config)# access-group INSIDE in interface inside
Adding an Extended Access List
This section describes how to add an extended access list, and includes the following sections:
• Extended Access List Overview, page 16-5
• Adding an Extended ACE, page 16-6
Extended Access List Overview
An extended access list is made up of one or more ACEs, in which you can specify the line number to
insert the ACE, source and destination addresses, and, depending on the ACE type, the protocol, the
ports (for TCP or UDP), or the ICMP type (for ICMP). You can identify all of these parameters within
the access-list command, or you can use object groups for each parameter. This section describes how
to identify the parameters within the command. To use object groups, see the “Simplifying Access Lists
with Object Grouping” section on page 16-10.
For information about logging options that you can add to the end of the ACE, see the “Logging Access
List Activity” section on page 16-18. For information about time range options, see “Scheduling
Extended Access List Activation” section on page 16-17.
209.165.200.225
10.1.1.0/24
Inside
Outside
Static NAT
10.1.1.56
ACL
Permit from 10.1.1.0/24 to 10.1.1.56
PAT
209.165.201.4:port10.1.1.0/24
104635

 Loading...
Loading...











