43-4
Cisco Security Appliance Command Line Configuration Guide
OL-10088-01
Chapter 43 Troubleshooting the Security Appliance
Testing Your Configuration
Figure 43-3 Ping Failure Because of IP Addressing Problems
Step 3
Ping each security appliance interface from a remote host. For transparent mode, ping the management
IP address.
This test checks that the directly connected router can route the packet between the host and the security
appliance, and that the security appliance can correctly route the packet back to the host.
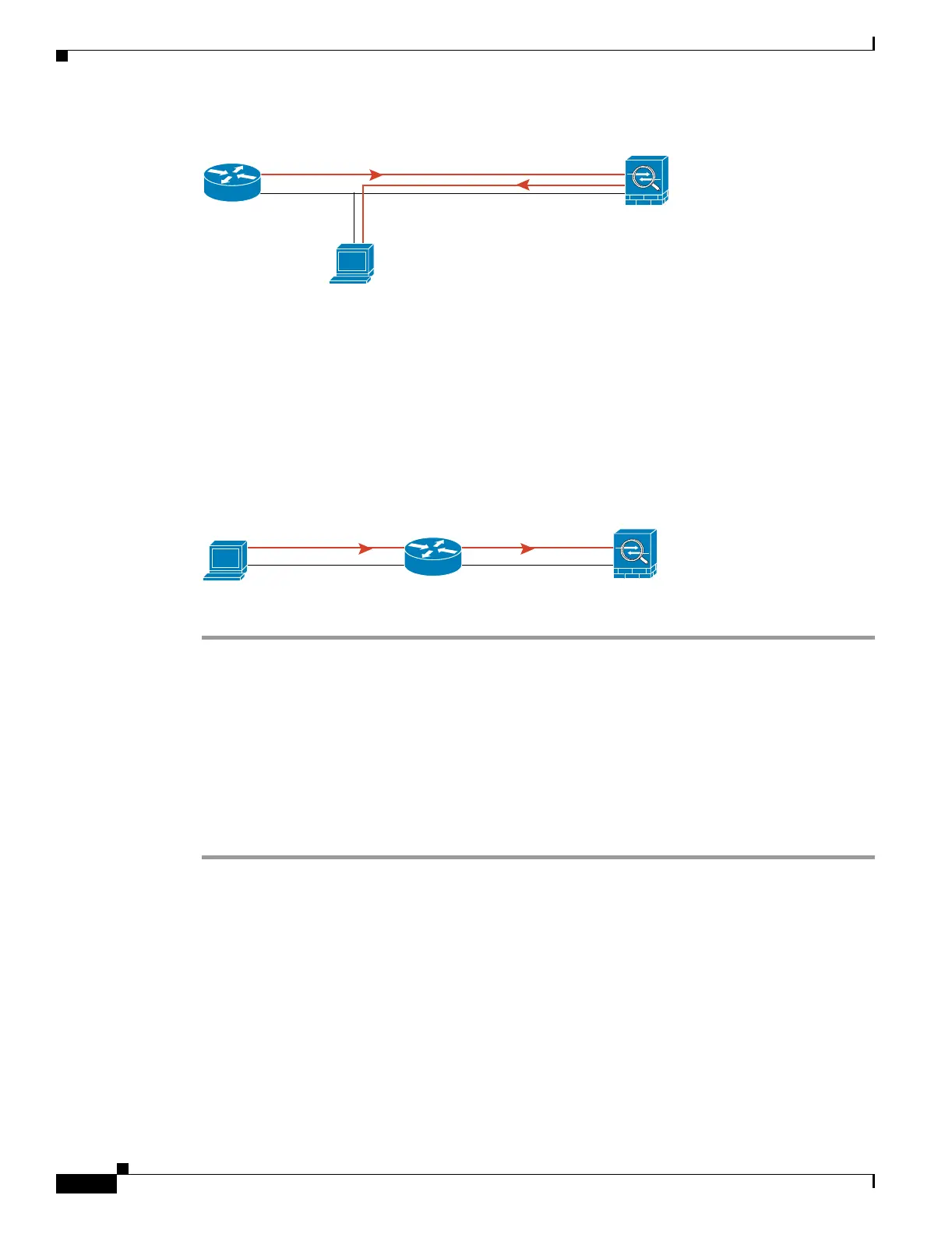
A ping might fail if the security appliance does not have a route back to the host through the intermediate
router (see Figure 43-4). In this case, the debug messages show that the ping was successful, but you see
system message 110001 indicating a routing failure.
Figure 43-4 Ping Failure Because the Security Appliance has no Route
Pinging Through the Security Appliance
After you successfully ping the security appliance interfaces, you should make sure traffic can pass
successfully through the security appliance. For routed mode, this test shows that NAT is working
correctly, if configured. For transparent mode, which does not use NAT, this test confirms that the
security appliance is operating correctly; if the ping fails in transparent mode, contact Cisco TAC.
To ping between hosts on different interfaces, perform the following steps:
Step 1 To add an access list allowing ICMP from any source host, enter the following command:
hostname(config)# access-list ICMPACL extended permit icmp any any
By default, when hosts access a lower security interface, all traffic is allowed through. However, to
access a higher security interface, you need the preceding access list.
Step 2 To assign the access list to each source interface, enter the following command:
hostname(config)# access-group ICMPACL in interface interface_name
Repeat this command for each source interface.
Step 3 To enable the ICMP inspection engine, so ICMP responses are allowed back to the source host, enter the
following commands:
hostname(config)# class-map ICMP-CLASS
192.168.1.1192.168.1.2
192.168.1.2
Ping
Router
Security
Appliance
Host
126696
Ping
Router
Host
?
Security
Appliance
126693

 Loading...
Loading...











