A-2
Cisco Security Appliance Command Line Configuration Guide
OL-10088-01
Appendix A Feature Licenses and Specifications
Supported Platforms and Feature Licenses
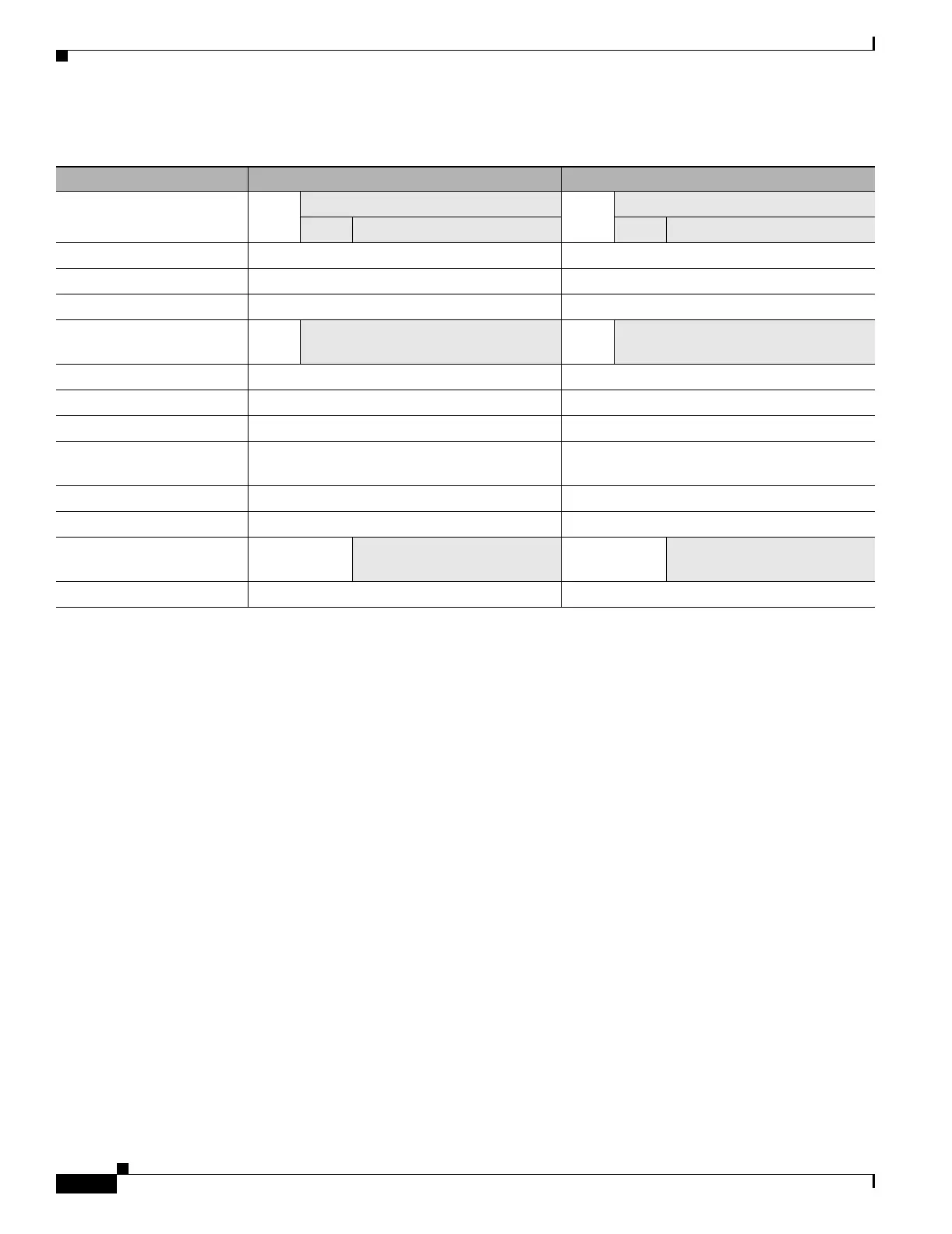
Table A-1 ASA 5505 Adaptive Security Appliance License Features
ASA 5505 Base License Security Plus
Users, concurrent
1
1. In routed mode, hosts on the inside (Business and Home VLANs) count towards the limit only when they communicate with the outside (Internet VLAN).
Internet hosts are not counted towards the limit. Hosts that initiate traffic between Business and Home are also not counted towards the limit. The interface
associated with the default route is considered to be the Internet interface. If there is no default route, hosts on all interfaces are counted toward the limit.
In transparent mode, the interface with the lowest number of hosts is counted towards the host limit. See the show local-host command to view the host
limits.
10 Optional Licenses: 10 Optional Licenses:
50 Unlimited 50 Unlimited
Security Contexts No support No support
VPN Sessions
2
2. Although the maximum IPSec and WebVPN sessions add up to more than the maximum VPN sessions, the combined sessions should not exceed the VPN
session limit. If you exceed the maximum VPN sessions, you can overload the security appliance, so be sure to size your network appropriately.
10 combined IPSec and WebVPN 25 combined IPSec and WebVPN
Max. IPSec Sessions 10 25
Max. WebVPN
Sessions
2
Optional License: 10 2 Optional License: 10
VPN Load Balancing No support No support
Failover None Active/Standby (no stateful failover)
GTP/GPRS No support No support
Maximum VLANs/Zones 3 (2 regular zones and 1 restricted zone that
can only communicate with 1 other zone)
5 (3 zones, 1 failover link, and 1 backup ISP
link)
Concurrent Firewall Conns
3
3. The concurrent firewall connections are based on a traffic mix of 80% TCP and 20% UDP, with one host and one dynamic translation for every four
connections.
10 K 25 K
Max. Physical Interfaces Unlimited, assigned to VLANs/zones Unlimited, assigned to VLANs/zones
Encryption Base (DES)
Optional license:
Strong (3DES/AES)
Base (DES) Optional license:
Strong (3DES/AES)
Minimum RAM 256 MB 256 MB
 Loading...
Loading...











