E-19
Cisco Security Appliance Command Line Configuration Guide
OL-10088-01
Appendix E Configuring an External Server for Authorization and Authentication
Configuring an External LDAP Server
Reviewing Examples of Active Directory Configurations
This section presents example procedures for configuring authentication and authorization on the
security appliance using the Microsoft Active Directory server. It includes the following topics:
• Example 1: Configuring LDAP Authorization with Microsoft Active Directory (ASA/PIX)
• Example 2: Configuring LDAP Authentication with Microsoft Active Directory
• Example 3: LDAP Authentication and LDAP Authorization with Microsoft Active Directory
Example 1: Configuring LDAP Authorization with Microsoft Active Directory (ASA/PIX)
This example presents a configuration procedure for authentication using SDI and authorization using
LDAP and Microsoft Active Directory (AD). To execute this sample procedure, perform the following
steps:
Step 1 Using LDIF files, create the cVPN3000-User-Authorization record on the Microsoft AD database. This
record contains the Cisco VPN authorization attributes for the user.
Note Contact Cisco TAC to obtain the Microsoft AD LDAP schema for Cisco VPN attributes.
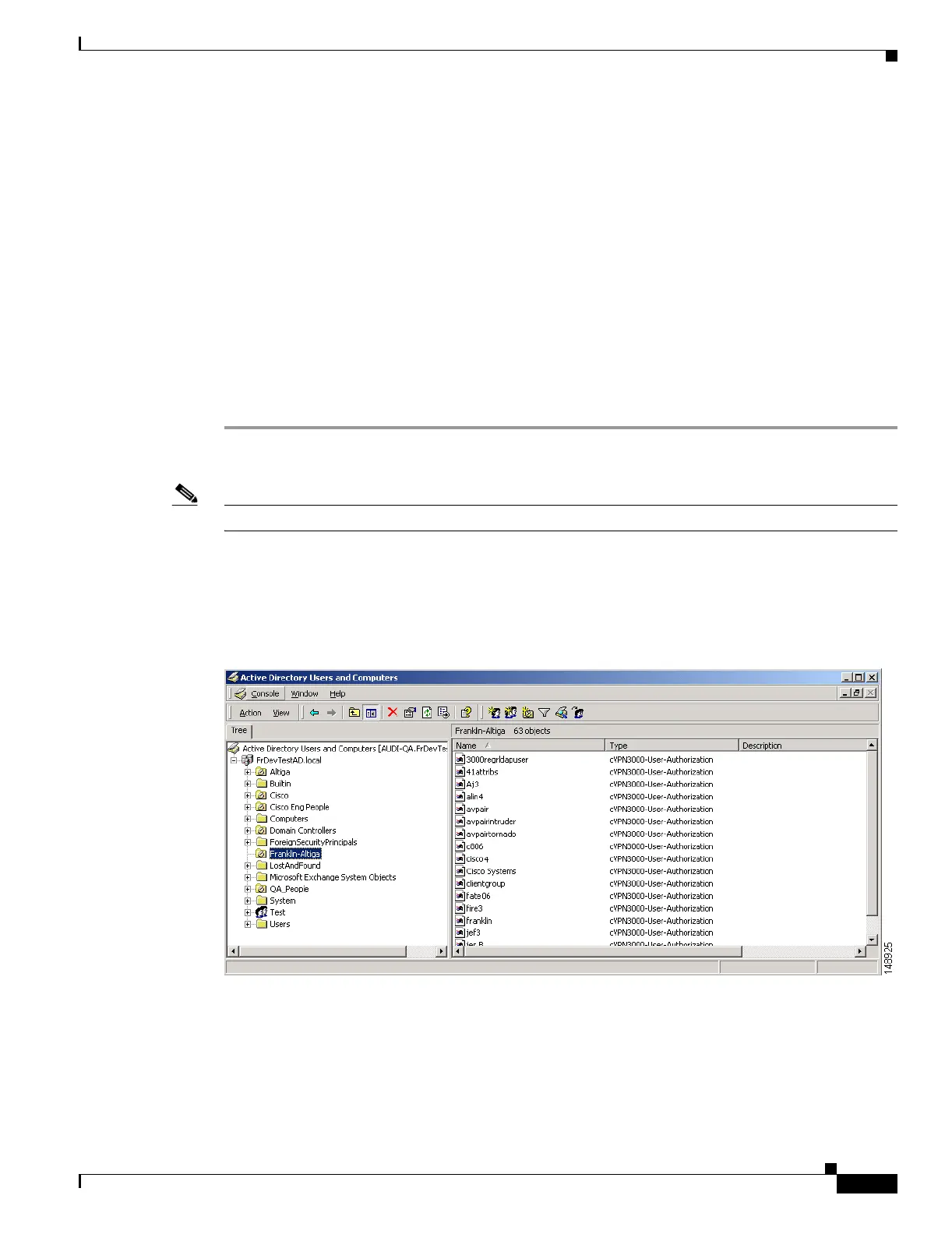
Step 2 To confirm the new record, choose Start > Settings > Control Panel > Administrative Tools > Active
Directory Users and Computers.
The Active Directory Users and Computers window appears as shown in Figure E-2.
Figure E-2 Active Directory Users and Computers Window
Step 3 On the security appliance, create a aaa-server record for the LDAP server. For this example, these
authorization records are stored in the Franklin-Altiga folder. The necessary steps are shown in the
following commands:
hostname(config)# aaa-server ldap-authorize-grp protocol ldap
hostname(config-aaa-server-group)# aaa-server ldap-authorize-grp host 10.1.1.4
hostname(config-aaa-server-host)# ldap-base-dn ou=Franklin-Altiga,dc=frdevtestad, dc=local
hostname(config-aaa-server-host)# ldap-scope subtree
 Loading...
Loading...











