34-2
Cisco Security Appliance Command Line Configuration Guide
OL-10088-01
Chapter 34 Configuring Easy VPN Services on the ASA 5505
Specifying the Client/Server Role of the Cisco ASA 5505
Specifying the Client/Server Role of the Cisco ASA 5505
The Cisco ASA 5505 can function as a Cisco Easy VPN hardware client (also called “Easy VPN
Remote”) or as a server (also called a “headend”), but not both at the same time. It does not have a default
role. Use one of the following commands in global configuration mode to specify its role:
• vpnclient enable to specify the role of the ASA 5505 as an Easy VPN Remote
• no vpnclient enable to specify the role of the ASA 5505 as server
The following example shows how to specify the ASA 5505 as an Easy VPN hardware client:
hostname(config)# vpnclient enable
hostname(config)#
The CLI responds with an error message indicating that you must remove certain data elements if you
switch from server to hardware client, depending on whether the elements are present in the
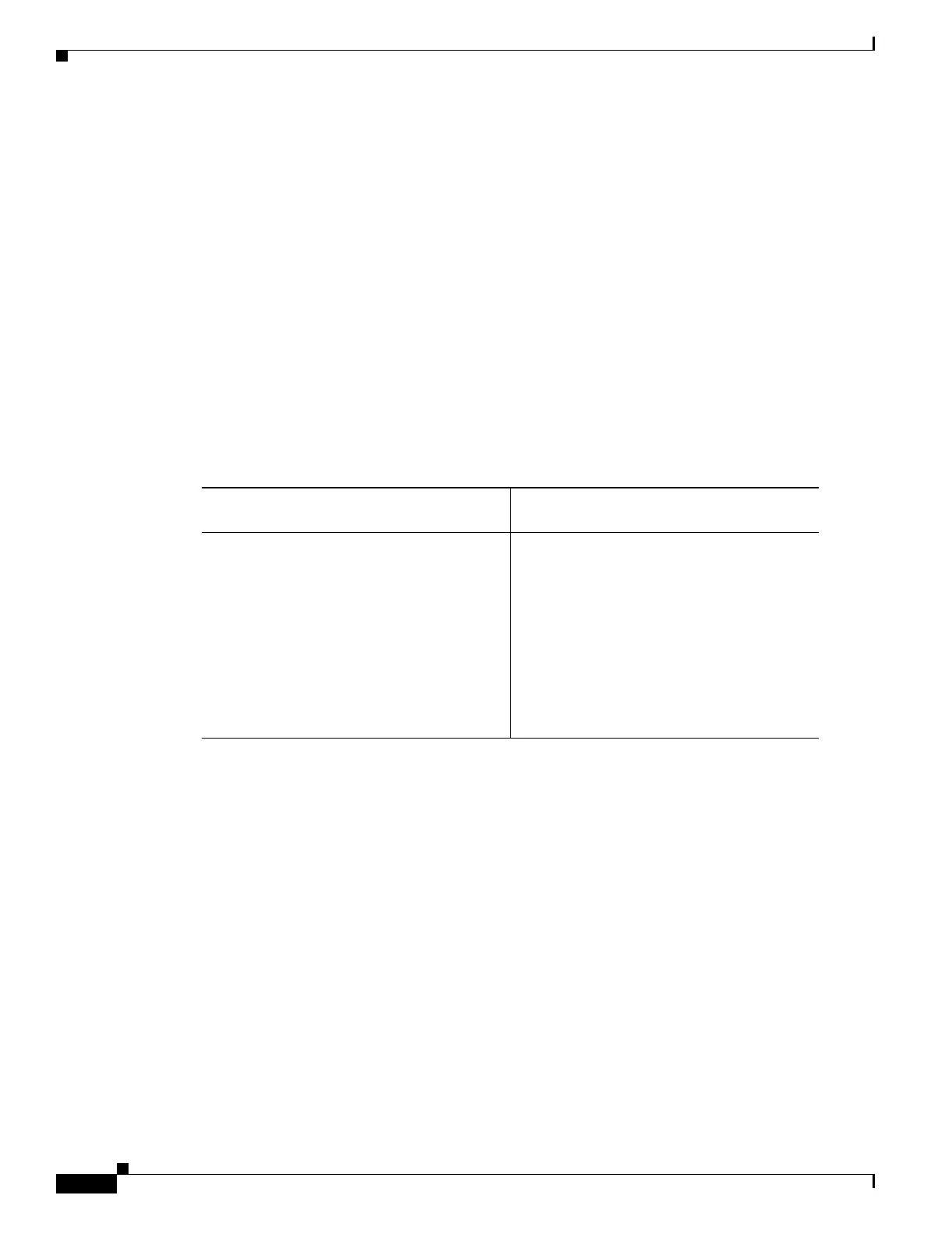
configuration. Table 0-1 lists the data elements that are permitted in both client and server
configurations, and not permitted in client configurations.
An ASA 5505 configured as an Easy VPN hardware client retains the commands listed in the first
column within its configuration, however, some have no function in the client role.
The following example shows how to specify the ASA 5505 as an Easy VPN server:
hostname(config)# no vpnclient enable
hostname(config)#
After entering the no version of this command, configure the ASA 5505 as you would any other ASA,
beginning with “Getting Started” section on page 2-1 of this guide.
Table 34-1 Configuration Privileges and Restrictions on the ASA 5505
Permitted in Both Client and Server
Configurations Not Permitted in Client Configurations
crypto ca trustpoints tunnel-groups
digital certificates isakmp policies
group-policies crypto maps
crypto dynamic-maps
crypto ipsec transform-sets
crypto ipsec security-association lifetime
crypto ipsec fragmentation before-encryption
crypto ipsec df-bit copy-df
 Loading...
Loading...











