43-5
Cisco Security Appliance Command Line Configuration Guide
OL-10088-01
Chapter 43 Troubleshooting the Security Appliance
Testing Your Configuration
hostname(config-cmap)# match access-list ICMPACL
hostname(config-cmap)# policy-map ICMP-POLICY
hostname(config-pmap)# class ICMP-CLASS
hostname(config-pmap-c)# inspect icmp
hostname(config-pmap-c)# service-map ICMP-POLICY global
Alternatively, you can also apply the ICMPACL access list to the destination interface to allow ICMP
traffic back through the security appliance.
Step 4 Ping from the host or router through the source interface to another host or router on another interface.
Repeat this step for as many interface pairs as you want to check.
If the ping succeeds, you see a system message confirming the address translation for routed mode
(305009 or 305011) and that an ICMP connection was established (302020). You can also enter the
show xlate and show conns commands to view this information.
If the ping fails for transparent mode, contact Cisco TAC.
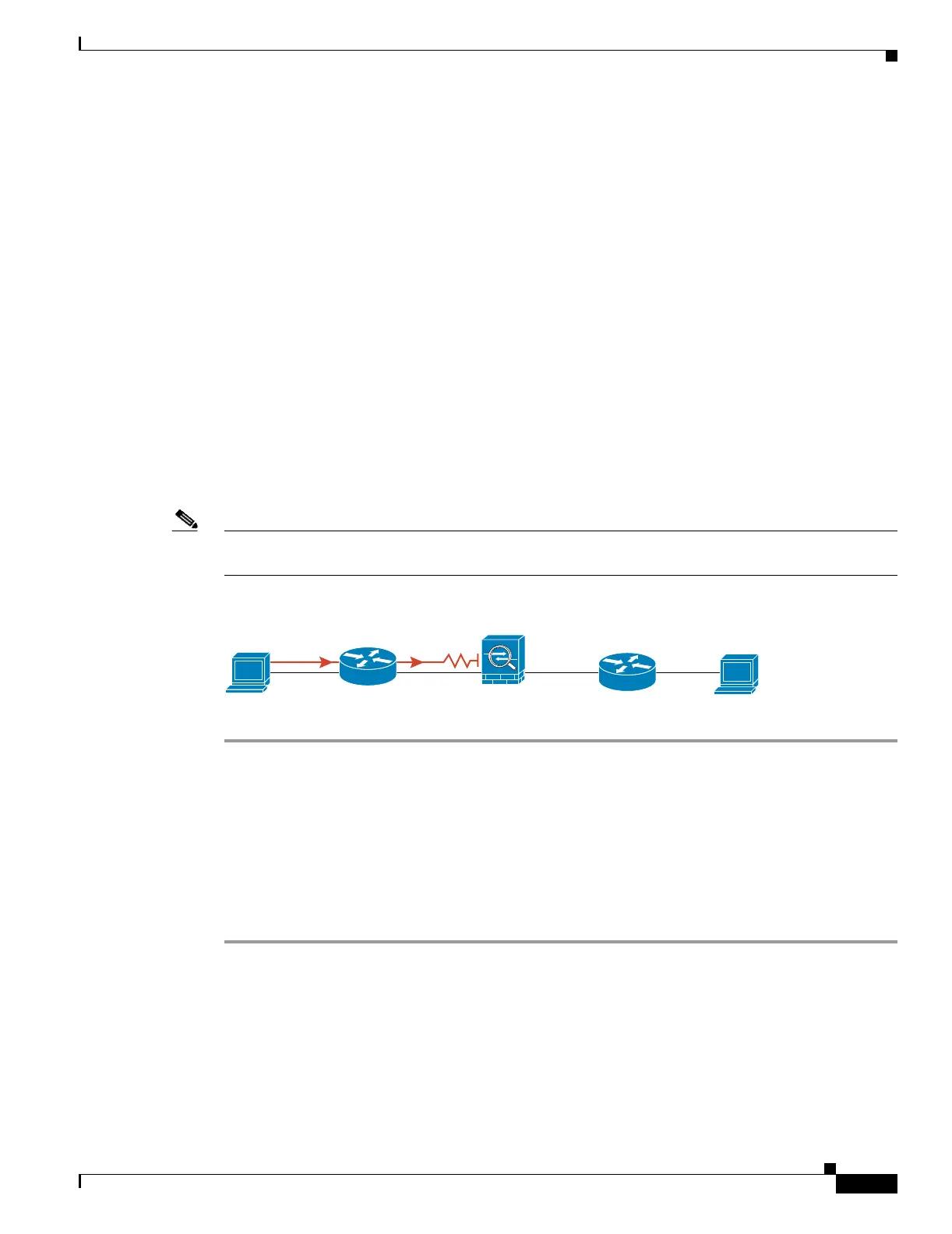
For routed mode, the ping might fail because NAT is not configured correctly (see Figure 43-5). This is
more likely if you enable NAT control. In this case, you see a system message showing that the NAT
translation failed (305005 or 305006). If the ping is from an outside host to an inside host, and you do
not have a static translation (which is required with NAT control), you see message 106010: deny
inbound icmp.
Note The security appliance only shows ICMP debug messages for pings to the security appliance interfaces,
and not for pings through the security appliance to other hosts.
Figure 43-5 Ping Failure Because the Security Appliance is not Translating Addresses
Disabling the Test Configuration
After you complete your testing, disable the test configuration that allows ICMP to and through the
security appliance and that prints debug messages. If you leave this configuration in place, it can pose a
serious security risk. Debug messages also slow the security appliance performance.
To disable the test configuration, perform the following steps:
Step 1 To disable ICMP debug messages, enter the following command:
hostname(config)# no debug icmp trace
Step 2 To disable logging, if desired, enter the following command:
hostname(config)# no logging on
Step 3 To remove the ICMPACL access list, and also delete the related access-group commands, enter the
following command:
Ping
Router
Router
Host
Host
Security
Appliance
126694
 Loading...
Loading...











