E-25
Cisco Security Appliance Command Line Configuration Guide
OL-10088-01
Appendix E Configuring an External Server for Authorization and Authentication
Configuring an External RADIUS Server
• For other vendors’ RADIUS servers (for example, Microsoft Internet Authentication Service): you
must manually define each security appliance attribute. To define an attribute, use the attribute name
or number, type, value, and vendor code (3076). For a list of security appliance RADIUS
authorization attributes and values, see Table E-4.
Step 2 Set up the users or groups with the permissions and attributes to send during IPSec/WebVPN tunnel
establishment. The permissions or attributes might include access hours, primary DNS, banner, and so
forth.
Security Appliance RADIUS Authorization Attributes
Note Authorization refers to the process of enforcing permissions or attributes. A RADIUS server defined as
an authentication server enforces permissions or attributes if they are configured.
Table E-4 lists all the possible security appliance supported attributes that can be used for user
authorization.
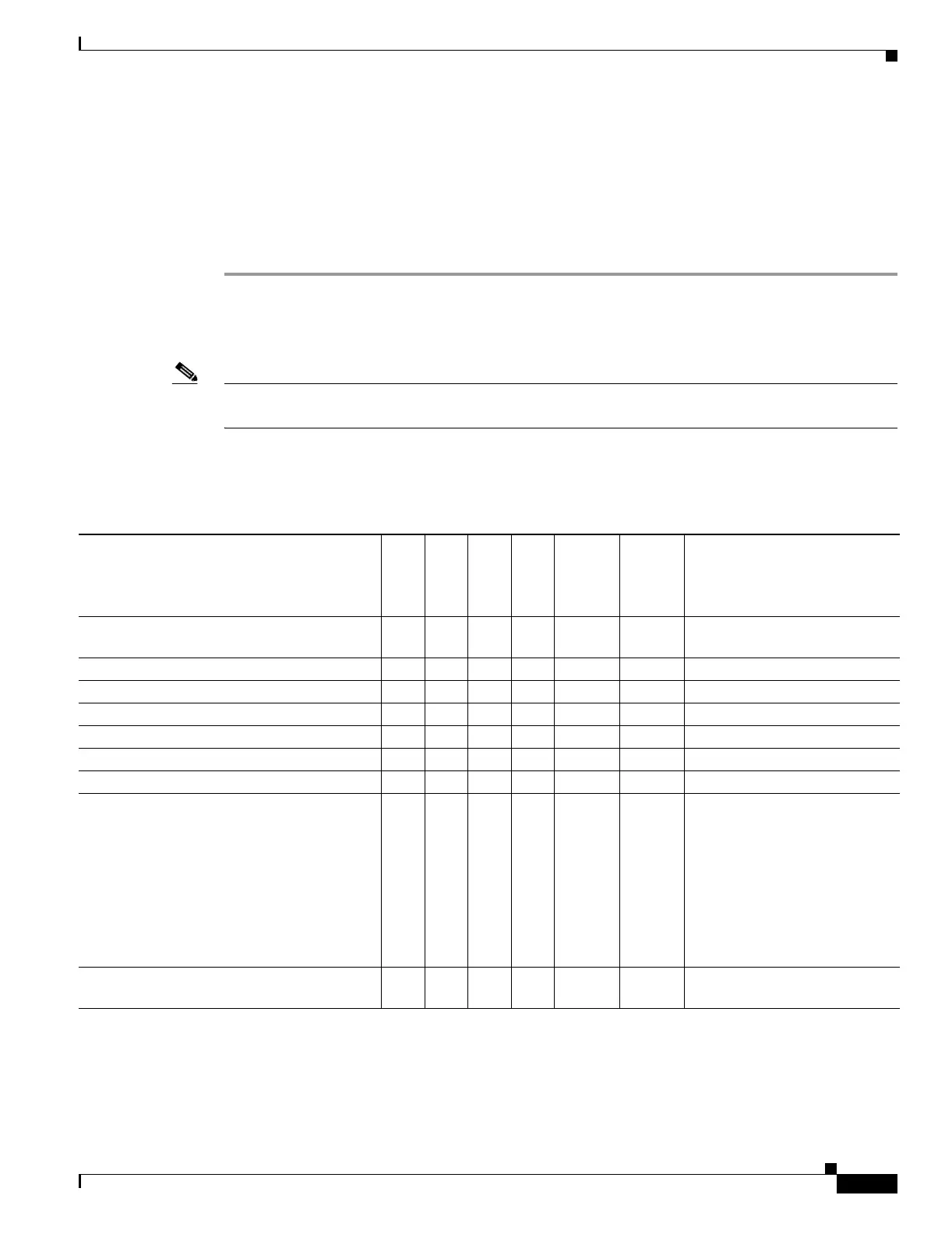
Table E-4 Security Appliance Supported RADIUS Attributes and Values
Attribute Name
VPN
3000 ASA PIX
Attr.
#
Syntax/
Type
Single
or
Multi-
Valued
Single or Multi-
Valued
Access-Hours Y Y Y 1 String Single Name of the time range, e.g.,
Business-hours
Simultaneous-Logins Y Y Y 2 Integer Single An integer 0 to 2147483647
Primary-DNS Y Y Y 5 String Single An IP address
Secondary-DNS Y Y Y 6 String Single An IP address
Primary-WINS Y Y Y 7 String Single An IP address
Secondary-WINS Y Y Y 8 String Single An IP address
SEP-Card-Assignment 9 Integer Single Not used
Tunneling-Protocols Y Y Y 11 Integer Single 1 = PPTP
2 = L2TP
4 = IPSec
8 = L2TP/IPSec
16 = WebVPN
4 and 8 are mutually exclusive,
(0-11, 16-27 are legal values)
IPSec-Sec-Association Y 12 String Single Name of the security
association
 Loading...
Loading...











