15
Security
15-40 bizhub PRO 1050P
15.6.4 Analyze audit log
Audit logs need to be analyzed by the machine manager regularly (once per
month) or when unauthorized access and tampering of data saved in the ma-
chine in Security Strengthen mode is noticed.
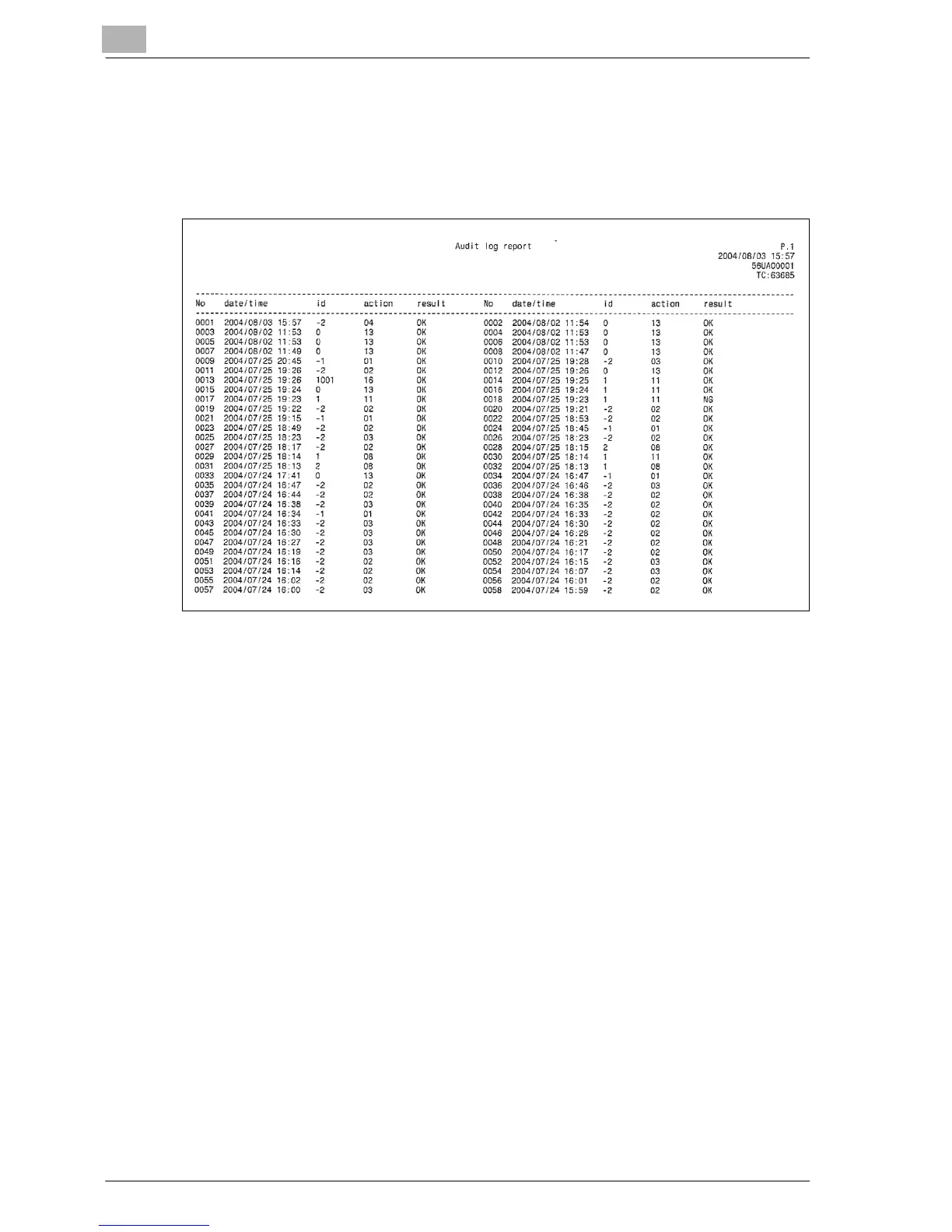
Audit Log Information
The audit log contains the following information.
1.
date/time:
date and time when an operation was made that results in the creation of
a log entry.
2.
id:
the person who made the operation or who is subject to security protec-
tion can be specified.
"-1": Operation by CE (service representative).
"-2": Operation by the machine manager.
"-3": Operation by the unregistered user.
Other integer: Indicates subjects for security protection, and the follow-
ing action IDs narrow down the subject for protection.
User ID (1 to 1000 numerical symbols)
Confidential User ID (1 to 99999 numerical symbols)
3.
action:
Used to specify the operation.
Check details of operation that action indicates in the following table.

 Loading...
Loading...











